What is “Unapproved Emails” Email Spam
Subject: cPanel Withheld Incoming Mails
******** Notification!
Dear ********,
You have [13] unapproved emails on 5/21/2024 11:26:59 a.m. This was caused due to a system delay. Please rectify below:
Release Pending messages to inbox now.
Source: ******** Support
Unapproved Emails email spam refers to unsolicited emails that are sent to individuals without their consent, usually for the purpose of promoting products or services. These emails often contain misleading information and may contain malicious links or attachments that can infect a computer with malware. Unapproved Emails spam campaigns are typically sent out in bulk to a large number of email addresses, with the hope that some recipients will click on the links or download the attachments.
When a recipient interacts with an Unapproved Emails email scam, they are at risk of having their personal information compromised, their computer infected with malware, or becoming a victim of financial fraud. These emails often use social engineering tactics to trick recipients into clicking on links or providing sensitive information, such as login credentials or credit card numbers. It is important for individuals to be cautious when receiving unsolicited emails and to avoid interacting with any emails that seem suspicious or from unknown senders.

How to stop email spam like “Unapproved Emails”
You can use an anti-spam filter which will block most known sources of spam before they even reach your inbox. MailWasher is a program you may try. It filters spam and lets you preview emails on a server without downloading them onto your computer. MailWasher has customizable spam filters, uses bayesian filtering and works with all major email programs: Outlook, Outlook Express, Thunderbird, GMail, etc.
Types of spam email
Spam email messages can be approximately divided into three categories: those that prompt you to download and run something, those that ask for your personal data, and those asking you to make payments. Let’s take a closer look at each one so we can better protect ourselves from these scams.
-
Emails with attachments
In the first case the email contains an attachment which it prompts you to open. Those attachments may consist of executable files or they may be Microsoft Word or Excel documents containing malicious macro scripts. Once you launch the executable file or allow the document to run its macros, malware downloads onto your device and wreaks all kinds of havoc with it.
The malware may range from adware showing extra ads on your browsers to ransomware that encrypts your files and aks for payment to decrypt them.
-
Phishing emails
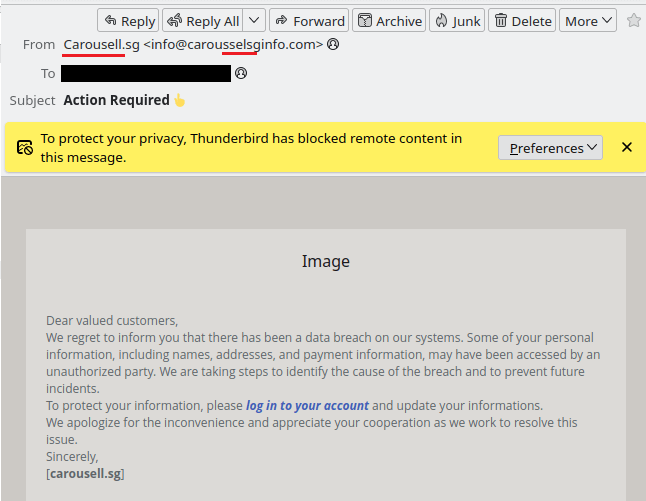
The second type of spam (phishing emails) try to trick you into entering your name, logins, passwords, credit card details, etc. on what you think are legitimate and respectable websites.
Those emails usually pretend to be messages from well-known websites that you are probably registered on, and prompt you to follow a link to their site for some reason (for example, there is something wrong with your account). The provided link leads to fake site of course, and the data you enter ends up in the hands of cybercriminals.
-
Advance-fee scam and sextortion scam emails
Finally there are the emails urging people make payments. These can be further divided into two types: the first type, asking people to invest into something, to pay some money now and get back much more later (the advance-fee scam); the second one, scaring people into paying to prevent something bad from happening.
An example of the first one is the well-known Nigerian Prince email. A example of the second is sextortion scam: emails that claim that the email author has access to the victims’s web cam and has the victims intimate videos, which the criminal threatens to publish unless paid off.
How to find out that the email is scam

- Check the sender’s address – if the address doesn’t match up with what you expect from that company, then it’s very likely that the email is scam. Be aware though that the sender address can be faked, so if the address looks legitimate it is not guaranteed that the email is legit.
- Look for spelling and grammar mistakes and weird phrasing – real emails from reputable companies are far less likely to have those.
- Watch for urgent requests – legitimate companies will never ask customers for sensitive information such as credit card numbers via email, so if an email suddenly asks for urgent action like requesting payment details within few hours, chances are high this could potentially be a scam attempt.
How to protect yourself from email scam
- Use an email filtering service – email filtering services like MailWasher Pro allow you to filter out unwanted messages before they reach your inbox. These services use sophisticated algorithms to identify suspicious content in incoming emails and block them automatically so that only legitimate messages make it through the filter.
- Avoid clicking on suspicious links – if you receive an email with a link that looks suspicious, do not click on it! Even if the sender appears familiar, chances are high that the link is malicious and could lead you down a path of malware infection or identity theft. It is best not to open any unknown links at all.
- Don’t respond directly – never reply directly to spam emails as this will confirm for spammers that your address is active which may result in more unsolicited mail being sent your way. Instead, mark these messages as “Spam” within your email client/service provider so that their filters can better detect similar types of mail next time.
- Keep software up-to-date – make sure all software installed onto devices such as computers and smartphones is kept up-to date with latest security patches released by developers; this helps reduce risk posed by cyber criminals who exploit vulnerabilities found in outdated versions of programs including email clients.
- Use anti virus protection – install reputable antivirus solutions onto any device receiving emails; most modern day anti viruses come equipped with advanced features such as real time scanning which help detect potential threats immediately upon opening files attached to emails.
