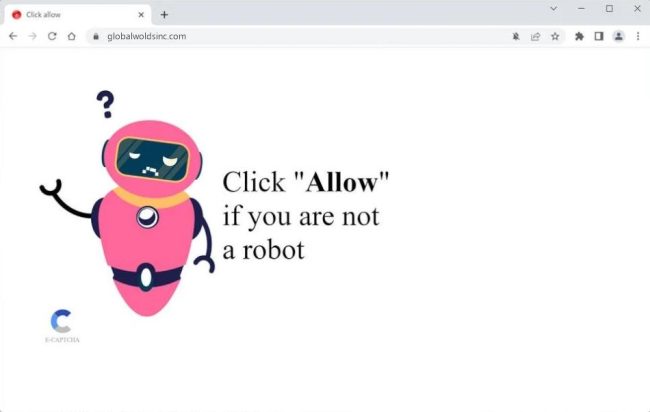
How to remove Search-it-now.com (Mac)
Search-it-now.com is a notorious adware that targets Mac computers, bombarding users with unwanted advertisements and redirects to dubious websites. This adware infiltrates Mac computers through deceptive techniques such as software bundling, where it is packaged with legitimate software and installed without the user's knowledge. Once installed, Search-it-now.com modifies browser settings and starts displaying intrusive ads in the form of pop-ups, banners, and sponsored links.