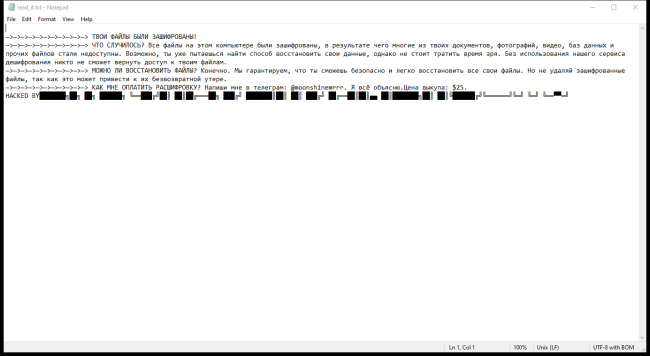
How to remove TechRangeSearch
TechRangeSearch is a type of adware that infects computers and displays unwanted advertisements and pop-ups to users. This adware is typically installed on a computer without the user's knowledge or consent, often bundled with other software downloads or through malicious websites. Once installed, TechRangeSearch tracks the user's browsing activity and collects data on their online behavior in order to display targeted ads.