What Is ListScheduler?
ListScheduler is a type of adware that targets Mac computers, infecting them with unwanted advertisements and pop-up notifications. This malicious software infiltrates the system through deceptive methods such as fake software updates, misleading email attachments, and malicious websites. Once installed, ListScheduler displays intrusive ads, redirects users to suspicious websites, and tracks their online activities to gather personal information for targeted advertising.
ListScheduler can slow down the performance of the infected Mac, consume system resources, and compromise the user’s privacy and security. To prevent infection, Mac users should be cautious when downloading software from untrusted sources, avoid clicking on suspicious links or ads, and keep their operating system and security software up to date. If a Mac becomes infected with ListScheduler, it is recommended to use reputable antivirus software to scan and remove the adware from the system.
How to Remove ListScheduler:
- Remove ListScheduler Automatically
- Delete Rogue Applications
- Remove Rogue Profiles from Macbook
- Remove ListScheduler From Browsers
- How to Protect Your PC From ListScheduler and Other Adware
Remove Gloss Glamour Automatically
You may try to remove the adware automatically or use the manual instructions provided below.
However it is still recommended that you scan your system with a good antivirus or anti-malware tool, to find and remove other possible malware and PUPs (potentially unwanted programs) that may have been installed along with ListScheduler.
Some alternatives:
Spyhunter (macOS and Windows)
Delete Rogue Applications:
Go to Applications folder and delete new and suspicious apps.
- On the top menu select Go => Applications.
- Drag an unwanted application to the Trash bin.
- Right-click on the Trash and select Empty Trash.
Remove Rogue Profiles from Macbook:
- Open System Preferences.
- Click on Profiles.
- Click the minus button below to delete rogue settings.
Remove ListScheduler from browsers:
Remove ListScheduler and other new and unfamiliar extensions.
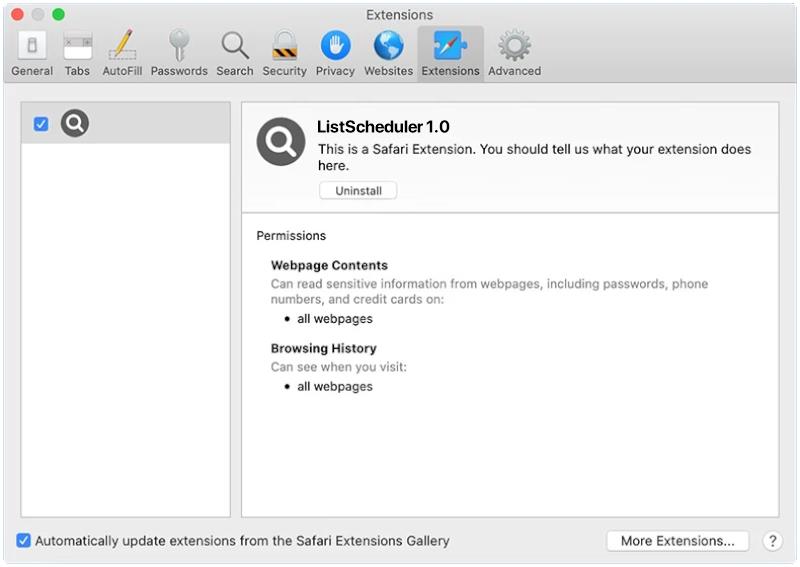
Remove ListScheduler from Safari:
- On the top menu select Safari => Preferences (or Settings).
- Select Extensions tab.
- Select an extension you want to delete and click Uninstall button under the extension’s description.
Remove ListScheduler from Google Chrome:
- Click on three dots menu button
 .
. - Select More tools => Extensions.
- Find an extension you want to delete and click REMOVE under it.
- Click Remove in the dialog box.
ListScheduler Removal from Mozilla Firefox:
- Click on menu button
 and select Add-ons.
and select Add-ons. - Go to the Extensions tab.
- To uninstall an add-on, click on three dots button next to it and select Remove.
How to Protect Your Mac From ListScheduler and Other Adware:
- Use an antivirus:Get a powerful anti-malware software, capable of detecting and eliminating PUPs. Having several on-demand scanners would be a good idea too.
- Keep macOS and apps updated: Regularly update your macOS and applications to patch security vulnerabilities and strengthen your system against malware.
- Use ad-blockers:Download and use Adguard, uBlock Origin or one of the other trustworthy extensions for blocking third-party advertisements on websites.
- Download from trusted sources: Only download apps, software, and files from trusted sources like the Apple App Store to minimize the risk of malware infections.
- Read dialogue boxes carefully: Pay close attention to dialogue boxes to avoid inadvertently installing malware.
- Be cautious with email attachments and links: Avoid opening suspicious email attachments and clicking on unfamiliar links to prevent malware infiltration.
