What is Boost Ransomware?
Boost Ransomware is a malicious software that infects computers by tricking users into downloading and installing it through deceptive emails, malicious websites, or software vulnerabilities. Once installed, Boost Ransomware encrypts files on the infected computer, adding the .boost file extension to each encrypted file. It uses a powerful encryption algorithm to lock files, making them inaccessible to the user.
After encrypting the files, Boost Ransomware creates a ransom note, typically named “ReadMe.txt” or “ReadMe.html,” which contains instructions on how to pay a ransom in exchange for a decryption key. The ransom note usually demands payment in cryptocurrency and provides a deadline for the victim to comply. While there are no official decryption tools available for Boost Ransomware, some cybersecurity experts and researchers may develop decryption tools to help victims recover their files. If infected with Boost Ransomware, victims should avoid paying the ransom and seek assistance from reputable cybersecurity professionals who may be able to provide decryption solutions.
Ransom note:
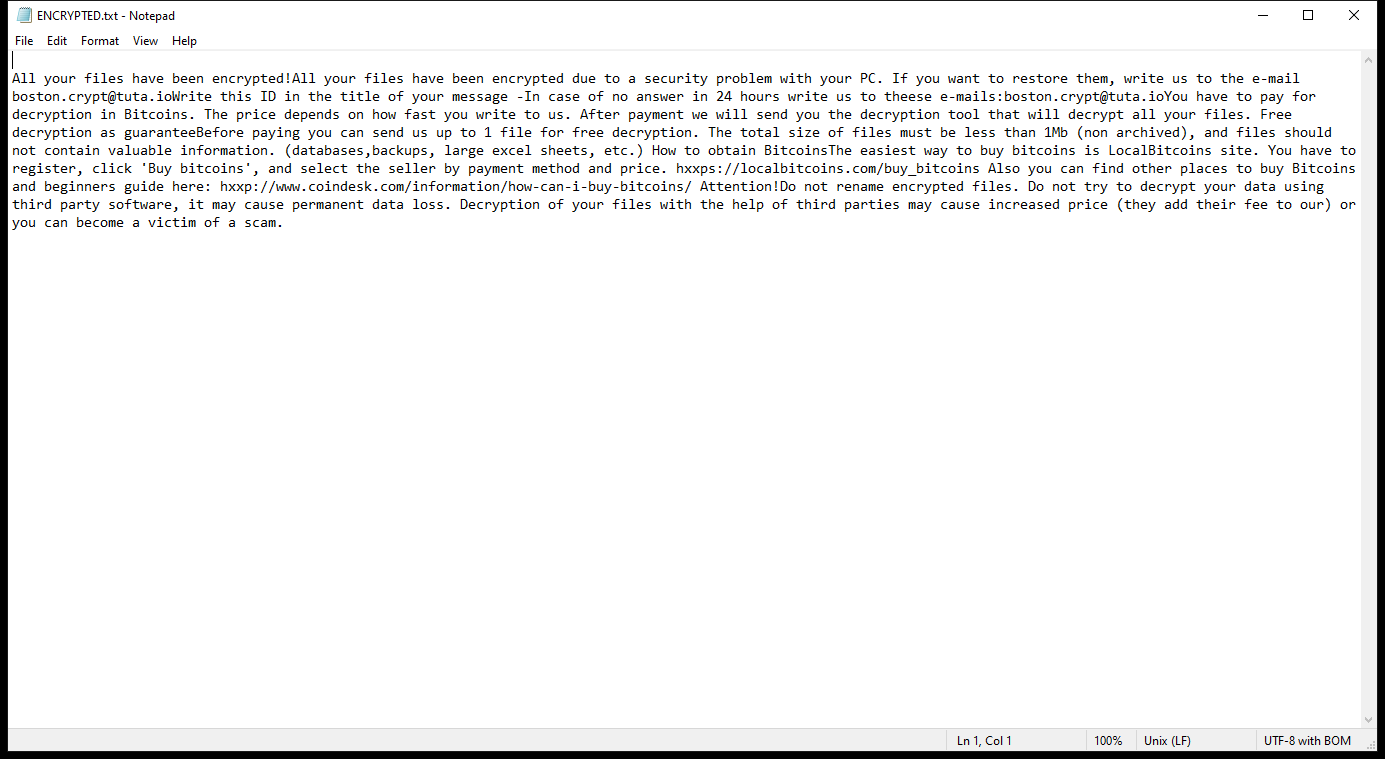
ENCRYPTED.txt contents:
All your files have been encrypted!All your files have been encrypted due to a security problem with your PC. If you want to restore them, write us to the e-mail boston.crypt@tuta.ioWrite this ID in the title of your message -In case of no answer in 24 hours write us to theese e-mails:boston.crypt@tuta.ioYou have to pay for decryption in Bitcoins. The price depends on how fast you write to us. After payment we will send you the decryption tool that will decrypt all your files. Free decryption as guaranteeBefore paying you can send us up to 1 file for free decryption. The total size of files must be less than 1Mb (non archived), and files should not contain valuable information. (databases,backups, large excel sheets, etc.) How to obtain BitcoinsThe easiest way to buy bitcoins is LocalBitcoins site. You have to register, click ‘Buy bitcoins’, and select the seller by payment method and price. hxxps://localbitcoins.com/buy_bitcoins Also you can find other places to buy Bitcoins and beginners guide here: hxxp://www.coindesk.com/information/how-can-i-buy-bitcoins/ Attention!Do not rename encrypted files. Do not try to decrypt your data using third party software, it may cause permanent data loss. Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
How Ransomwares Like Boost Ransomware Ends Up on Users’ Computers:
Ransomware employs various methods to infect computers, exploiting vulnerabilities in both software and human behavior. One common tactic involves malicious email attachments or links, where unsuspecting users inadvertently download and execute the ransomware payload. Additionally, attackers may exploit software vulnerabilities, exploiting security flaws in outdated systems or applications to gain unauthorized access. Another avenue is through malicious websites or ads, which can silently install ransomware when visited. Furthermore, ransomware can spread through networked devices, leveraging weak passwords or unsecured connections to infiltrate entire systems.
- Remove Boost Ransomware Automatically
- Back up Your Encrypted Files
- Decrypt .boost Files
- Restore .boost Files With File Recovery Tools
- Recover Encrypted Files From Shadow Copies
- How to Protect Your PC From Malware and Prevent Ransomware Infections In the Future
Remove Boost Ransomware
First, we advise you to scan your computer with an antivirus to find and remove all remaining instances of Boost Ransomware.
Other anti-malware software that may be able to get rid of Boost Ransomware:
Norton (Windows, macOS, iOS, Android) The link may not work correctly in some countries.
Malwarebytes (Windows)
Back up Your Encrypted Files:
We advise you to create a copy of the encrypted files and put it away. That might help you if free ransomware decryptor becomes available in the future, or if you decide to pay and get the decryptor but something goes wrong and files get irreparably damaged in the process of decryption.
Decrypt .boost Files:
Most ransomware use very complex encryption methods. Only the creators have the special key needed to unlock the files. Without this key, it’s impossible to get the data back. Usually, the hackers keep these keys on their own servers, not on the infected computers. Some ransomware is so well-made that it’s almost impossible to recover files without the hackers’ help. But some are not so good and have mistakes, like using the same key for everyone or keeping keys on the infected computer. That’s why it’s a good idea to look for tools to unlock your files if you get hit by ransomware. You can use NoMoreRansom site to find if a specific decryption tool for Boost Ransomware exists.
Restore .boost Files With File Recovery Tools:
Screenshot:
About Stellar Data Recovery
- Retrieves data from formatted, encrypted, or corrupted drives.
- Free trial version allows user to scan, preview and download up to 1GB of data.
- Supports Windows 11, 10, 8 and 7. A Mac variant is also available.
Recover Encrypted Files From Shadow Copies:
Shadow Explorer is a free tool designed to access Shadow Volume Copies in Windows systems. It allows users to retrieve previous versions of files and folders stored in these shadow copies. By selecting a specific disk and date, users may be able to recover lost or overwritten data. Download and install the latest version of Shadow Explorer, or opt for the portable version.
- Launch Shadow Explorer.
- On the top left part of the window pick a disk (C:\, D:\, etc.) and a date when a snapshot of files was captured.
- To retrieve file or a folder, right-click on it and select Export.
- Select the destination where you want to store the files
How to Protect Your PC From Malware and Prevent Ransomware Infections In the Future:
- Keep software updated: Regularly update your operating system, antivirus software, and other applications to patch security vulnerabilities.
- Use antivirus and anti-malware software: Install reputable antivirus and anti-malware programs to detect and remove ransomware threats.
- Enable firewall: Activate and properly configure a firewall to monitor and block suspicious network traffic.
- Backup data regularly: Create and maintain regular backups of important files and data on separate storage devices or cloud services to mitigate the impact of a ransomware attack.
- Exercise caution with email: Be cautious when opening email attachments or clicking on links, especially from unknown or suspicious senders.
- Stay informed: Stay up-to-date on the latest ransomware threats, tactics, and prevention strategies to adapt your defenses accordingly.
