What is Arena ransomware
![Ransom note of Crysis’s Arena: All your files have been encrypted!
All your files have been encrypted due to a security problem with your PC. If you want to restore them, write us to the e-mail [contact-email]
Write this ID in the title of your message [your-id]
In case of no answer in 24 hours write us to theese e-mails:[contact-email]
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us. After payment we will send you the decryption tool that will decrypt all your files.
Free decryption as guarantee
Before paying you can send us up to 5 files for free decryption. The total size of files must be less than 10Mb (non archived), and files should not contain valuable information. (databases,backups, large excel sheets, etc.)
How to obtain Bitcoins
The easiest way to buy bitcoins is LocalBitcoins site. You have to register, click 'Buy bitcoins', and select the seller by payment method and price.
https://localbitcoins.com/buy_bitcoins
Also you can find other places to buy Bitcoins and beginners guide here:
http://www.coindesk.com/information/how-can-i-buy-bitcoins/
Attention!
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.](https://www.computips.org/wp-content/uploads/2017/12/arena-ransomware.png)
At least two ransomware variants use .arena extension for encrypted files: Arena from Crysis (Dharma) ransomware family and Arena from CryptoMix family. Crysis’s Arena usually infects computers through Remote Desktop Services (RDP). It encrypts files using strong encryption algorithm that is considered unbreakable and upends .id-[your-id].[contact-email].arena to file names. From the information we gathered, users are asked to pay 0.5 bitcoins in the first 24 hours and 1 bitcoin later. This Arena will launch automatically every time you login to Windows and will encrypt new files that were created since its last run. Crysis’s Arena will create ransom notes called info.hta and FILES ENCRYPTED.txt (with a short text “all your data has been locked us You want to return? write email [contact-email]”).
CryptoMix’s Arena modifies names of encrypted files into hexadecimal strings and upends .arena extension. Its ransom note is named _HELP_INSTRUCTION.TXT.
Unfortunately, both Arena versions don’t have free decrypters as of now. However, you may try some other methods of recovering encrypted files.
How to Remove Arena Ransomware
If you have working backups of your encrypted files or you are not going to try and recover lost files, then scan your computer with one or several antivirus and anti-malware programs or reinstall the operatig system altogether.
SpyHunter is a powerful anti-malware solution that protects you against malware, spyware, ransomware and other types of Internet threats. SpyHunter is available for Windows and macOS devices.
Some alternatives:
Norton (Windows, macOS, iOS, Android) The link may not work correctly if your country is currently under sanctions.
However, if you want to try all possible ways of recovering encrypted files, including data recovery tools, then I suggest you use these tools first and scan with anti-malware later. Skip to the explanation
How to Recover Files Encrypted by Arena Ransomware
Once your files are encrypted by ransomware, you have several possible ways to recover them:
Going further, we need to 1) stop ransomware from encrypting files that we recover, if malware is still active; 2) try not to overwrite files deleted by ransomware. The best way to do it is disconnect your hard drive and connect it to another computer. You will be able to browse all your folders, scan them with antivirus programs, use file recovery software or restore data from Shadow Volume Copies. Although it is better to download all tools you’ll need beforehand and disconnect the computer from the Internet before connecting the infected hard drive, just to be safe.
Disadvantages of this method:
- This might void your warranty.
- It’s harder to do with laptops, and you’ll need a special case (disk enclosure) to put a hard drive in before connecting it to another machine.
- It is possible to infect the other computer if you open a file from the infected drive before scanning the drive with AVs and removing all found malware; or if all AVs fail to find and delete the malware.
Another, easier, way is to load into Safe Mode and do all file recovery measures from there. However, that will mean using the hard drive and potentially overwriting some data. In this case it’s preferable to use only portable versions of recovery software (the ones that don’t require installation), download them onto an external device, and save any recovered files onto an external device too (external hard drive, thumb drive, CD, DVD, etc.).
Boot Into Safe Mode:
 Windows XP,
Windows XP,  Windows Vista,
Windows Vista,  Windows 7:
Windows 7:
- Restart the computer.
- Once you see a boot screen tap F8 key continuously until a list of options appears.
- Using arrow keys, select Safe Mode with Networking.
- Press Enter.
 Windows 8,
Windows 8,  Windows 8.1,
Windows 8.1,  Windows 10:
Windows 10:
- Hold down Windows key
 and hit X key.
and hit X key. - Select Shut down or sign out.
- Press Shift key and click on Restart.
- When asked to choose an option, click on Advanced options => Startup Settings.
- Click Restart in the bottom right corner.
- After Windows reboots and offers you a list of options, press F5 to select Enable Safe Mode with Networking.
Back up Your Encrypted Files
It is alwayse advisable to create a copy of the encrypted files and put it away. That might help you if free ransomware decryptor becomes available in the future, or if you decide to pay and get the decryptor but something goes wrong and files get irreparably damaged.
Use File Recovery Tools to Recover Files
Recuva (free)
PhotoRec (free)
Step-by-step guide on how to use PhotoRec
Puran File Recovery (free for non-commercial use)

Video guide on how to use Puran File Recovery
R-Undelete (free version allows recovery of files under 256KB in size for Windows)
Detailed guide on how to recover deleted files with R-Undelete
Recover Encrypted Files From Shadow Copies.
The easiest way to access Shadow Volume Copies is by using a free tool called Shadow Explorer. Just download the latest version and install it (or download the portable version).
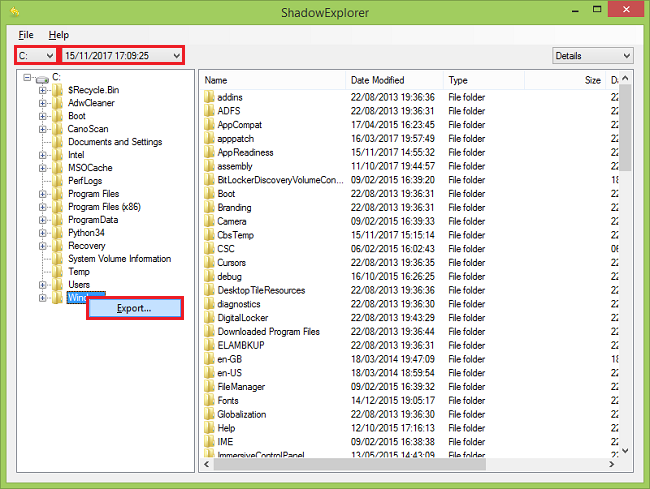
- Launch Shadow Explorer.
- On the top left part of the window you can select a disk (C:\, D:\, etc.) and a date when a snapshot of files was taken.
- To recover a file or a folder right-click on it and select Export….
- Choose where do you want to put the files.
Remove Arena Ransomware
Now that you have your recovered or still encrypted files on an external device, it is time to scan your computer with AV and anti-malware software or, better yet, reinstall the operating system, to fully get rid of possible ransomware traces. Remember to also scan your external device before putting files back on your computer!