Wpeeper Malware is a type of malicious software that infects Android devices and steals sensitive information from users. This malware often disguises itself as a legitimate app or software update, tricking users into downloading it onto their devices. Once installed, Wpeeper Malware can access personal data such as passwords, credit card information, and browsing history.
How to remove Brandnewsearch.com
Brandnewsearch.com is a type of adware that infiltrates computers and browsers in order to display unwanted advertisements and redirect users to sponsored websites. This adware typically gets installed on a user's system without their knowledge or consent, often bundled with freeware or shareware programs. Once installed, Brandnewsearch.com modifies browser settings and displays pop-up ads, banners, and in-text advertisements, disrupting the user's browsing experience.
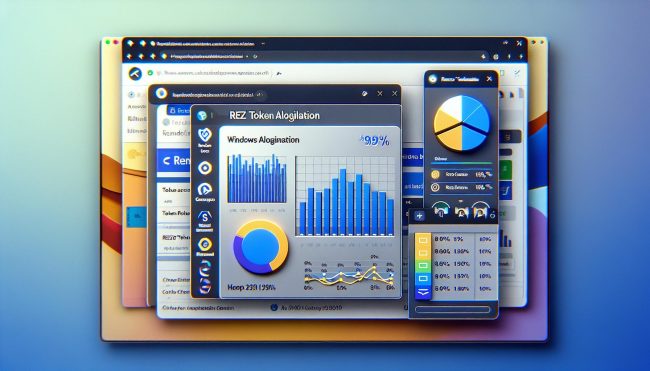
How to remove Renzo ($REZ) Token Allocation pop-ups
Renzo ($REZ) Token Allocation refers to the distribution of the Renzo token within the cryptocurrency ecosystem. The Renzo token is used as a utility token within the Renzo platform, serving various functions such as governance, staking, and incentivizing community participation. The token allocation determines how many tokens are reserved for each of these functions, as well as for early investors, team members, and advisors.
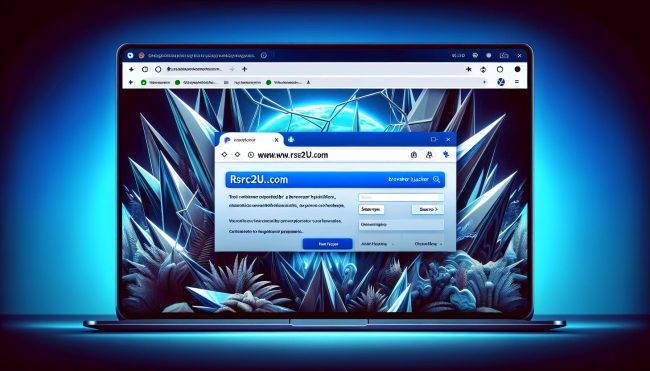
How to remove Rsrc2u.com
Rsrc2u.com is a type of adware that infects computers and web browsers by bombarding users with unwanted advertisements and pop-up windows. The adware typically gets installed on a computer through bundled software downloads or by clicking on malicious links. Once installed, Rsrc2u.com can track a user's browsing habits and display targeted ads based on their interests.
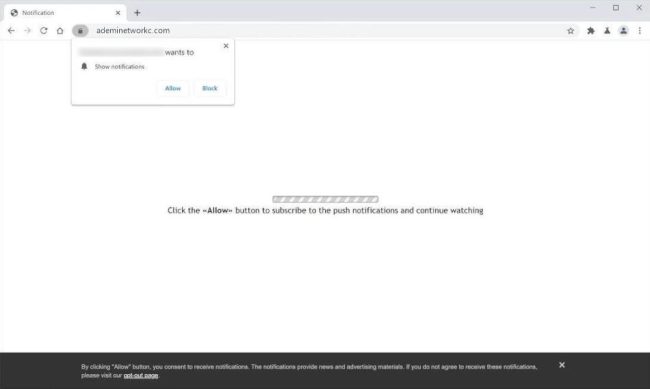
How to remove Ademinetworkc.com
Ademinetworkc.com is a malicious website that is known for infecting computers and exploiting browser notifications. It typically infects computers through deceptive tactics such as bundling with freeware or shareware, phishing emails, or malicious websites. Once a computer is infected, Ademinetworkc.com can cause various issues such as pop-up ads, browser redirects, and even data theft.
How to remove Meson ($MSN) Airdrop Claim pop-ups
Meson ($MSN) Airdrop Claim is a term used to describe a pop-up message that appears in web browsers, prompting users to claim a certain amount of Meson tokens for free. Meson is a cryptocurrency project that distributes tokens through airdrops as a way to promote its platform and attract new users. The Airdrop Claim message typically asks users to complete certain tasks, such as sharing their wallet address or signing up for a newsletter, in order to receive the free tokens.
How to remove KUZA Ransomware and decrypt .ripa files
KUZA Ransomware is a dangerous malware that infects computers through various methods, such as malicious email attachments, fake software updates, or exploit kits. Once it infiltrates a system, KUZA Ransomware starts encrypting files on the infected computer, adding the .ripa extension to them. This file extension indicates that the files have been encrypted and are inaccessible without the decryption key.
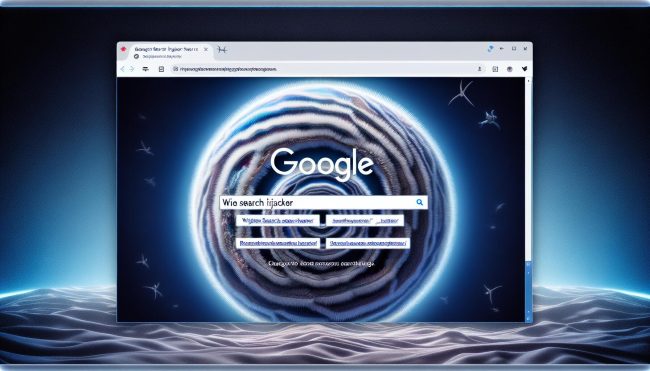
How to remove Wise Search
Wise Search is a type of adware that infects computers and web browsers, causing unwanted advertisements to appear on the screen. This intrusive software is often installed without the user's knowledge or consent, typically bundled with freeware or shareware programs. Once installed, Wise Search tracks the user's browsing habits and displays targeted ads based on their online activity.
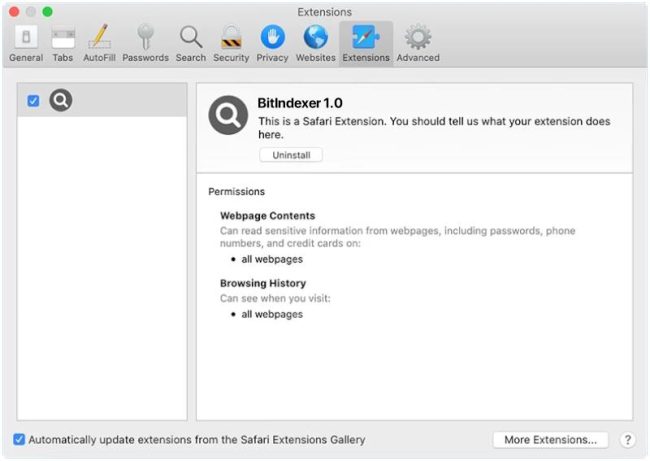
How to remove BitIndexer (Mac)
BitIndexer is a type of malware that specifically targets Mac computers. It is designed to infiltrate a user's system and gather sensitive information without their knowledge or consent. BitIndexer can infect a Mac through various means, including phishing emails, malicious websites, or by disguising itself as a legitimate software update.
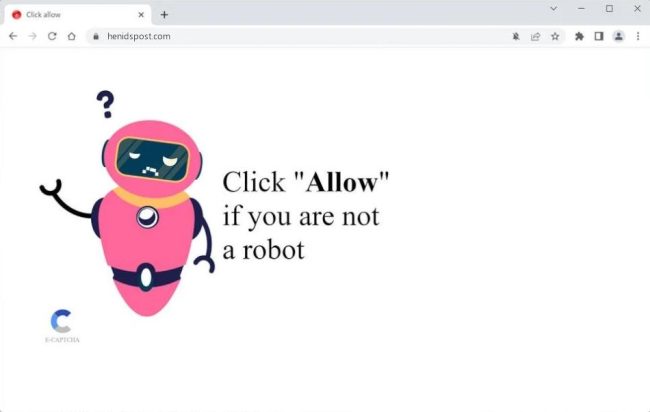
How to remove Henidspost.com
Henidspost.com is a malicious website that infects computers through various means, such as drive-by downloads, phishing emails, and malicious software bundles. Once a user visits the site, it may prompt them to download an application or click on a link that leads to the installation of malware on their device. This malware can then exploit vulnerabilities in the user's system to gain access to sensitive information or perform malicious activities.