What is Djvu ransomware
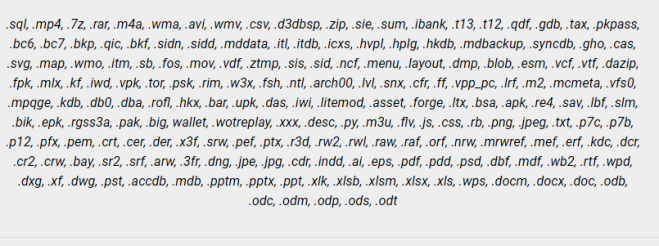
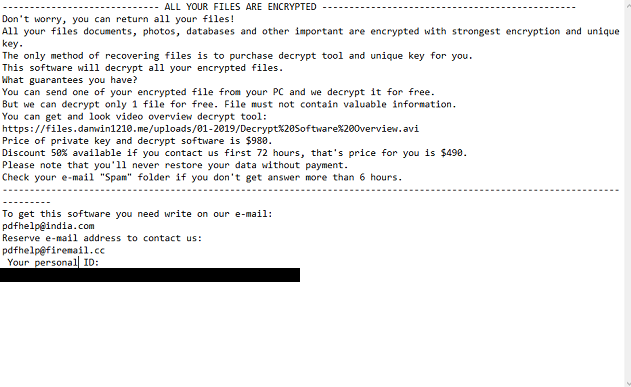
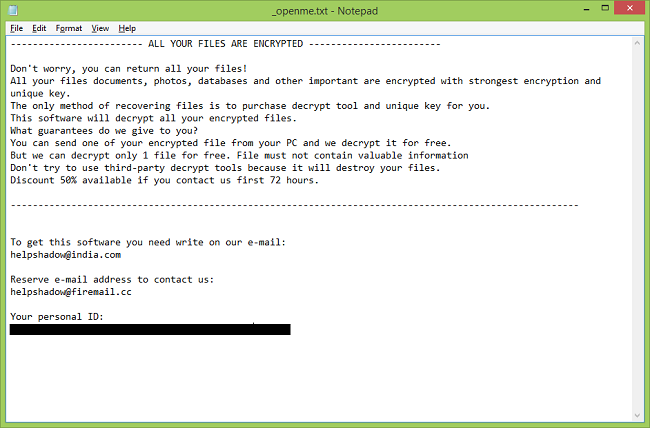
Professional users are aware of viruses such as extortionists. Djvu ransomware refers specifically to this type of virus. Djvu ransomware, also known as djvu files virus, is a very risky computer infection which modifies the Windows Registry. According to some information, this virus links with Stop Ransomware, because it shows the _openme.txt message, that gives an invasion and requires unlock files by contacting with us giving before this email helphadow@india.com or restorejvu@firemail.com to discuss the price of the decryptor and even a 50% discount if the answer lasts for 72 hours! There are several versions of djvu ransomware : Djvus virus, Djvuu virus, Uudjvu ransomware, Udjvuq ransomware. The activity of this crypto-extortionist came at the beginning of June 2018. It is focused on English-speaking users, but this does not prevent spreading it around the world. So, if you want to know how to remove djvu ransomware from your computer and decrypt .djvu files, read our article.
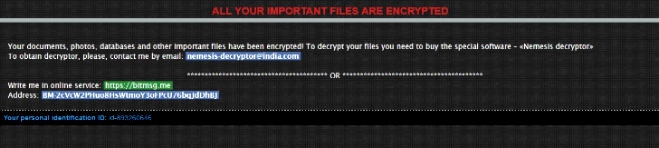
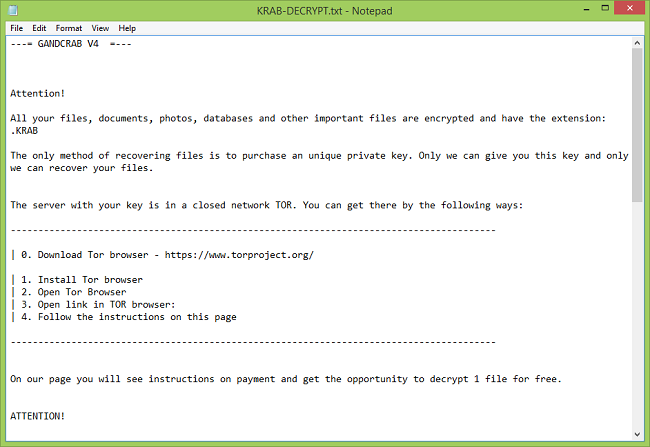
The content of the redemption text:
All your important files were encrypted on this computer.
You can verify this by clicking on see files and try to open them.
Encryption was produced using unique public key RSA-4096 generated for this computer.
To decrypted files, you need to obtain the private key.
The single copy of the private key, with will allow you to decrypt the files, is located on a secret server on the internet;
The server will destroy the key within 48 hours after encryption completed.
To retrieve the private key, you need to pay 2 bitcoins IMPORTANT YOU HAVE ONLY 48 HOURS IF U DON'T PAY ALL YOUR FILES WILL BE DELETED!
Bitcoins have to be sent to this address: 15sJ3pT7J6zefRs95SEsfBZMz8jAw1zAbh
After we confirm the payment , we send the private key so you can decrypt your system. READ MORE