What is Fofd ransomware?
Fofd is a ransomware-type virus: a virus that encrypts all data on your computer and demands money to decrypt it. This particular ransomware was made using the STOP/Djvu virus template.
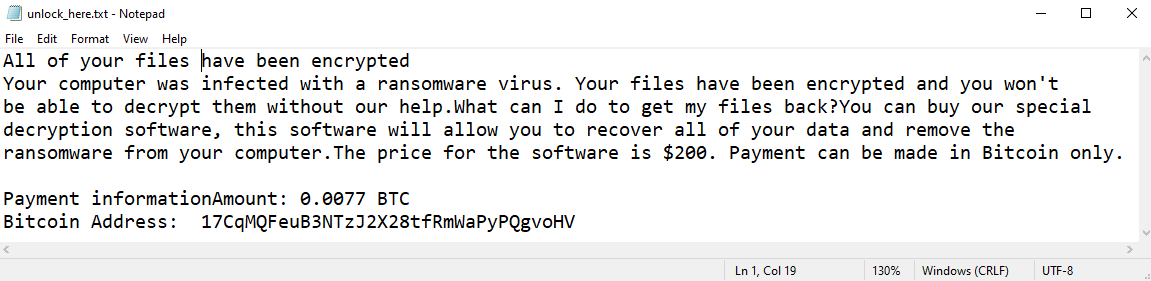
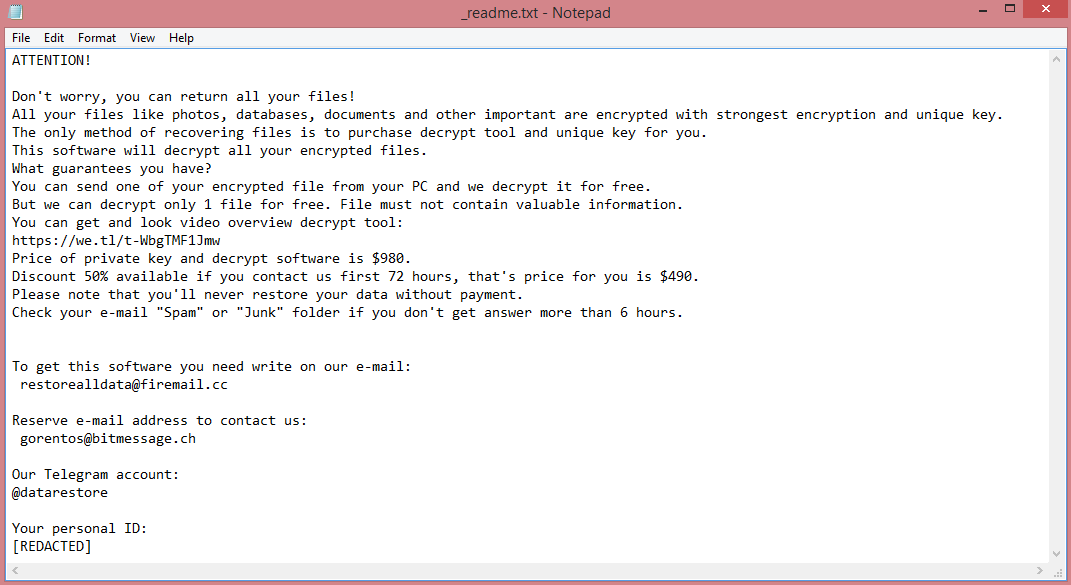
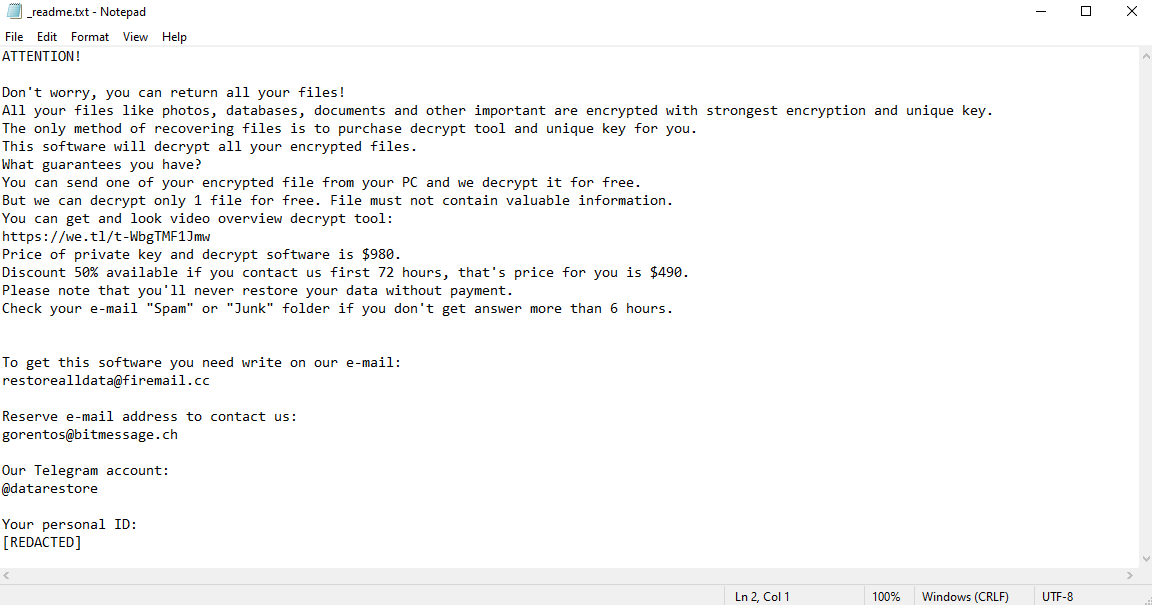
Fofd ransomware can be recognized very easily. You see, when the virus encrypts the files, it also changes their filename, adding .fofd file extension. So, checking the extension is a reliable to identify Fofd. In fact, it is the only way. The ransom note created by the virus, “_readme.txt”, is used by other STOP/Djvu viruses as well, so it cannot be used for the purposes of identification.
Reading the note can, however, let us know what the hackers’ demands are. They are fairly simple: $980, or $490 if the ransom is paid in the first three days after infection. However, we cannot recommend paying.
One reason not to pay the hackers is to avoid rewarding them for their crimes. After all, if their criminal venture is successful, they will likely launch yet another attack afterwards. But there’s a more practical reason, too. The hackers don’t always decrypt the files after payment; often, they simply cut communications after receiving money.
With this in mind, read the guide below. It contains several alternative ways to remove Fofd ransomware and decrypt .fofd files – this way you don’t have to pay the cybercriminals.