What is Gaze ransomware?
Gaze is a ransomware virus. Viruses of this type encrypt all files on the victim’s computer and demand ransom to decrypt them. Hence, the name.
Gaze is not a unique virus; it was made using the STOP/Djvu template. Each day, hackers create new viruses using this template, altering them slightly in hopes of bypassing antivirus protection. As a result, thousands of STOP/Djvu viruses exist: Gapo, Xaro, and Xash are several recent examples.
But, although Gaze is similar to other viruses in the STOP/Djvu family, there is still a reliable way to identify it. All STOP/Djvu viruses rename the victim’s files after encryption and give them a new four-letter extension – .gaze file extension, in our case.
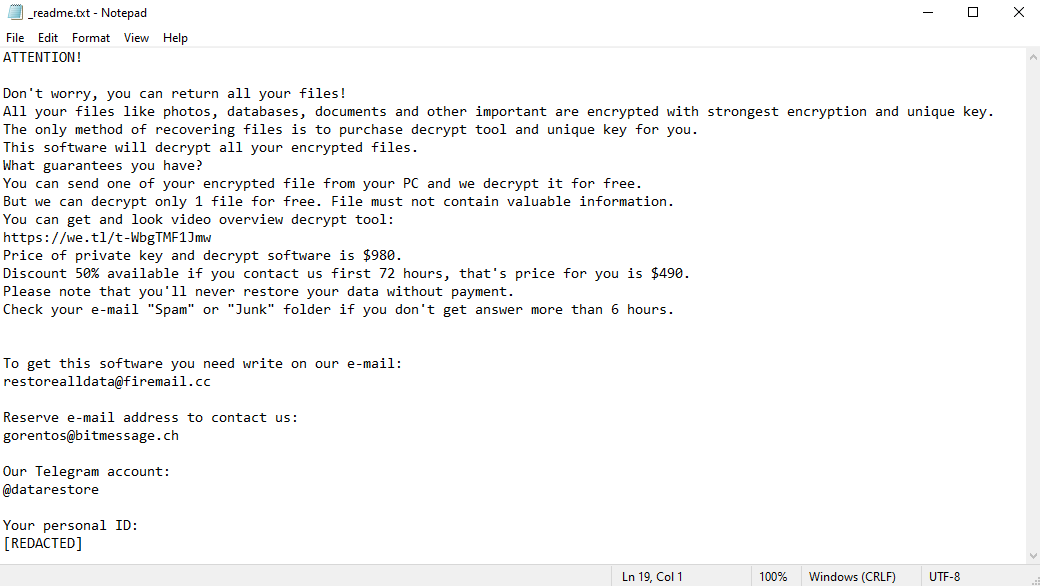
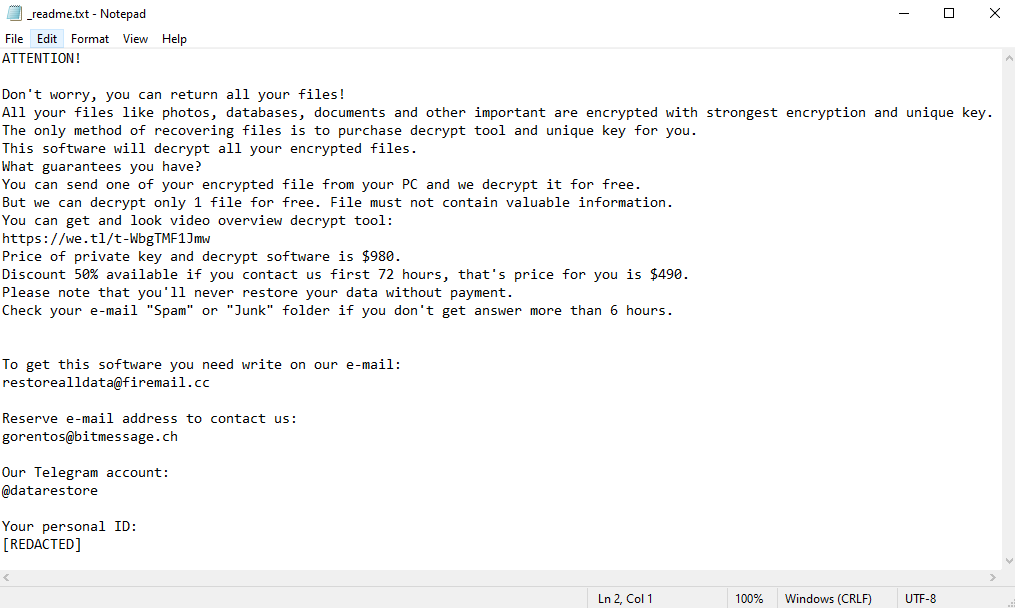
The hackers’ demands remain the same in each STOP/Djvu iteration – evidently, they see no need to alter them. They are communicated via a ransom note – always called “_readme.txt” – and are pretty simple. The victim must pay $980 to receive their files back, or $490 if they pay within 72 hours (3 days) of infection.
The hackers insist that paying is the only way to restore your files, but this is a lie. There are, in fact, other ways to remove Gaze ransomware and decrypt .gaze files – read about them in the article below.