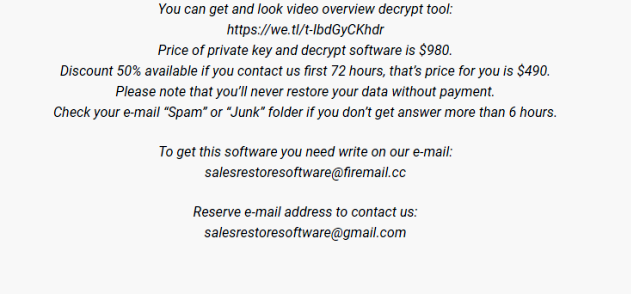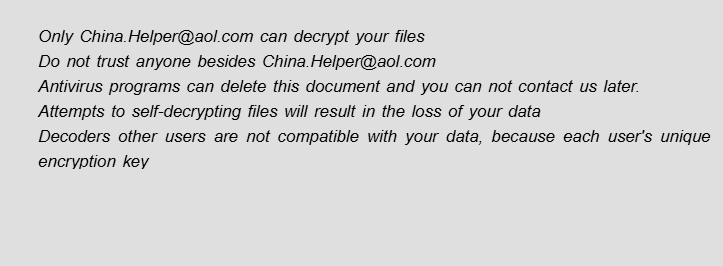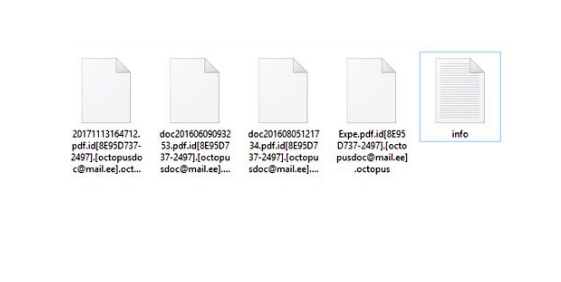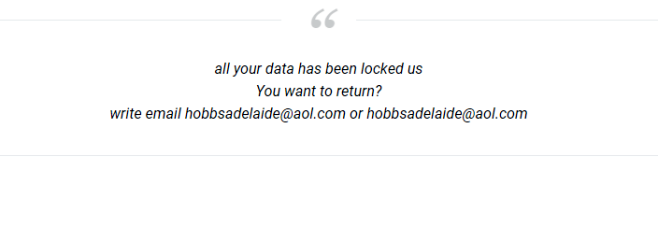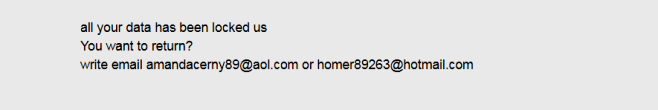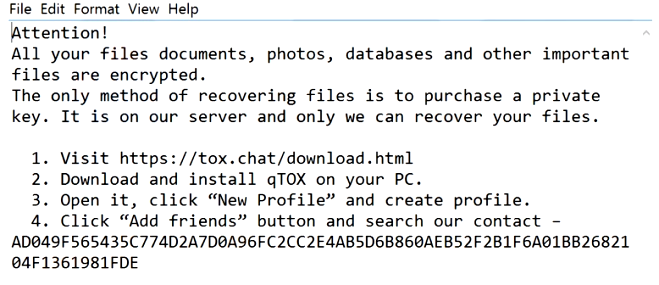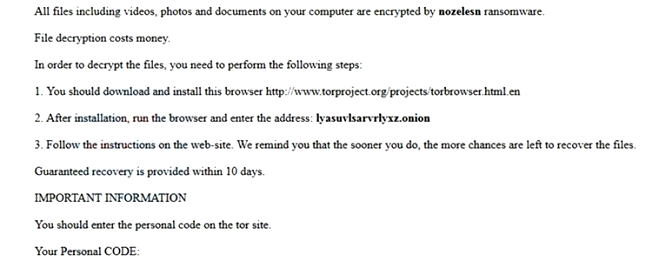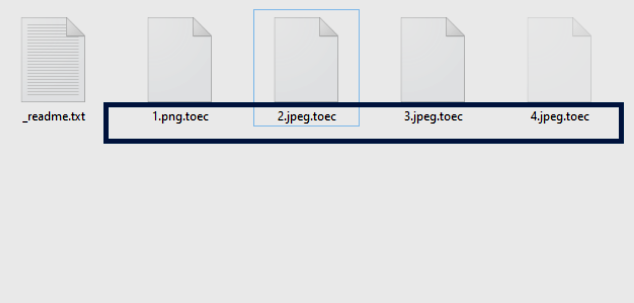
What is [Fire_show@tuta.io].adobe ransomware?
If you find that you cannot access your files, it means that files were blocked by the ransomware. More often than not, ransomware viruses infiltrate the computer to infect files and encrypt them. If the extension in the name of your files has changed to [fire_show@tuta.io] .adobe, you can be sure that your system is infected with [Fire_show@tuta.io].adobe ransomware. This is a file blocking malware that will encrypt all your files and then require a ransom in order to get the decryption key. Continue reading the article to see how infection can be prevented.