
What is NBES ransomware?
It is a virus ransomware program for Windows designed to encrypt files. It modifies files and adds the .nbes extension to encrypted files
Articles about ransomware – malware encrypting your personal files or stopping you from accessing your computer – and ways to remove it

It is a virus ransomware program for Windows designed to encrypt files. It modifies files and adds the .nbes extension to encrypted files

It is a newly discovered system pest that targets computer networks. Its main purpose is to capture user files by encrypting them and use them as an object for blackmail. Firstly, Losers ransomware penetrates the system secretly and begins the search important files. Next, Losers ransomware launches his encryption technique. It encrypts files and prevents you from working normally, requiring a ransom payment for returning files. In fact, scammers try to lure you with imaginary help to get your money. Remove this virus to get the files in their usual form

RedRum is a malicious application that belongs to the type of ransomware. The goal of RedRum is to infect the system and make a profit from it. RedRum gives 24 hours to contact developers of RedRum until after which the files become unusable. Developers threaten victims that their files will be lost

Looks .righ ransomware is a threat that is already taking over computers without the knowledge of the users themselves. This is an encryption virus that locks files in a computer system and displays a message of extortion to users. The method of locking files, and then demanding money for them is the main way the developers of this program earn money. Most often, users trust scrapbook notes for money and pay. This article is written so that you do not repeat the mistakes of those people who fell into the shop of Looks .righ ransomware. You will not get help from developers that they promise. You will give money just like that. Use this article to remove Looks .righ ransomware and return all files.

Snc ransomware belongs to the ransomware family. It encrypts files and adds an extension to the file names, which shows that the files are no longer available for use. This extension is the name of the virus

Real-news.net is a malicious computer infection such as ransomware. Real-news.net was created specifically for illegal profits. Firstly, it will infect your entire system and change your computer without permission
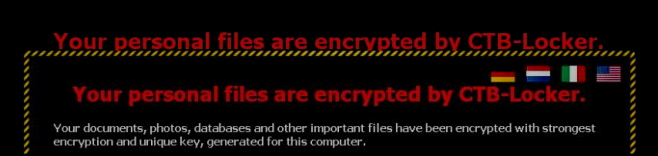
CTB-Locker is a cryptographic malware such as ransomware, released around mid-July 2014, which is almost identical to the viruses Merl ransomware, Rooster865qqz. According to statistics, this application attacks more users of the USA, Germany, Italy and the Netherlands

MERL ransomware is a ransomware virus that penetrates the system without visible symptoms. The most common way to infect systems is through spam messages. Usually, users open messages without any fear. In fact, opening a message, MERL ransomware enters the computer and rings the system. A file that was encrypted using the program becomes inaccessible. To mark locked files, the virus adds its extension to the file name

Rooster865qqZ was created using very powerful encryption algorithms from virus developers such as ransomware. In the vastness of the computer world, there are a large number of similar viruses (how to remove roger ransomware, how to remove sauron locker ransomware, how to remove fcrypt ransomware, how to remove phobos ransomware). Rooster865qqZ blocks all files on your computer, adding the extension .Rooster865qqZ to files, and then issues a ransom note on your computer, which claims to recover files encrypted by ransomware after you pay for them to extort. But this is not true. These are the usual tricks for such viruses. If you want to rid your computer of Rooster865qqZ, use this article.

ROGER ransomwareis a dangerous virus, a virus that works by the algorithm of infection and extortion of money by blackmail. There is a large number of viruses that look like a ROGER ransomware in the vastness of the computer world. For instance, GESD ransomware, NYTON ransomware, CILLA ransomware