What is Ahgr ransomware?
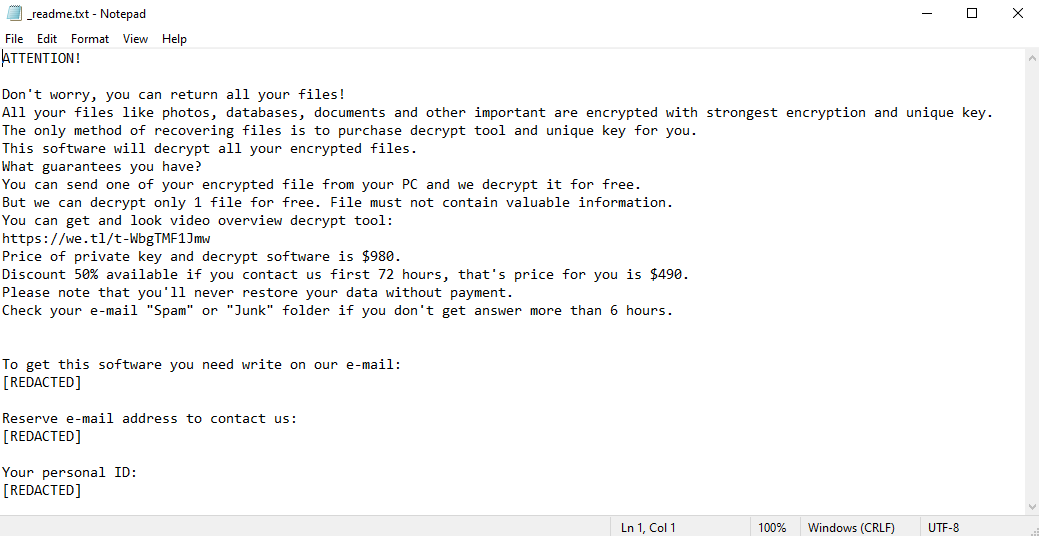
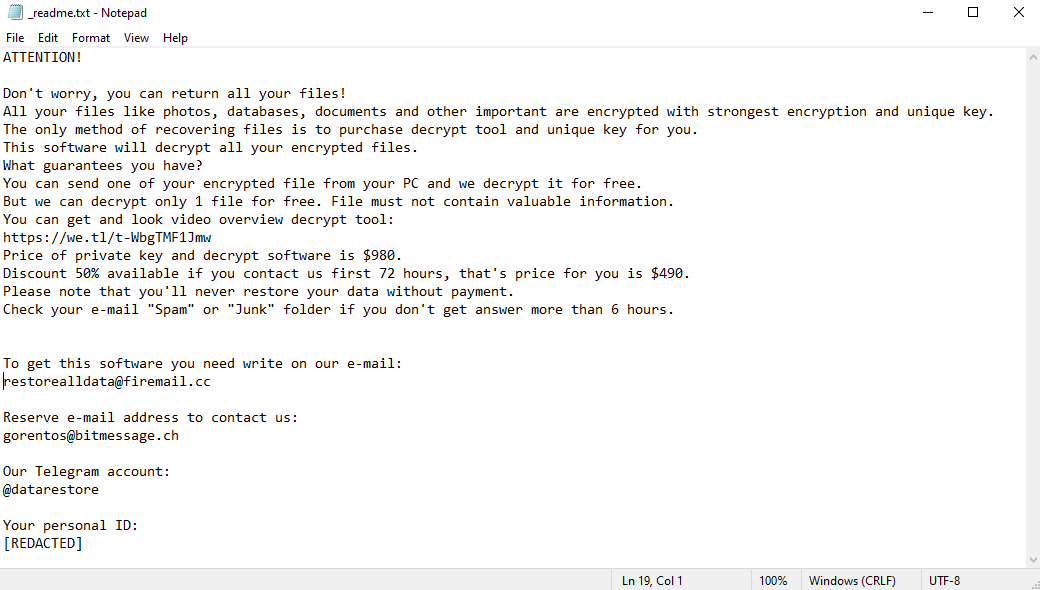
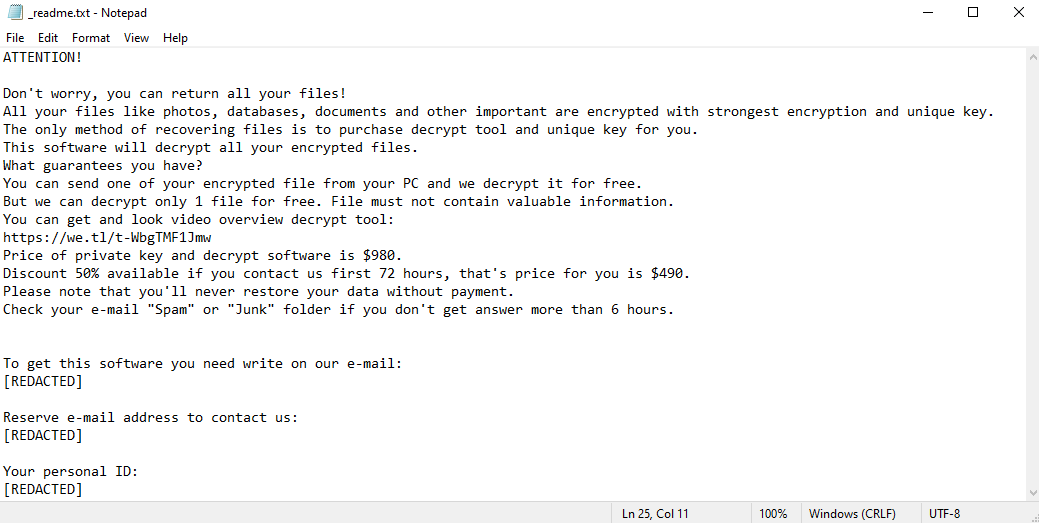
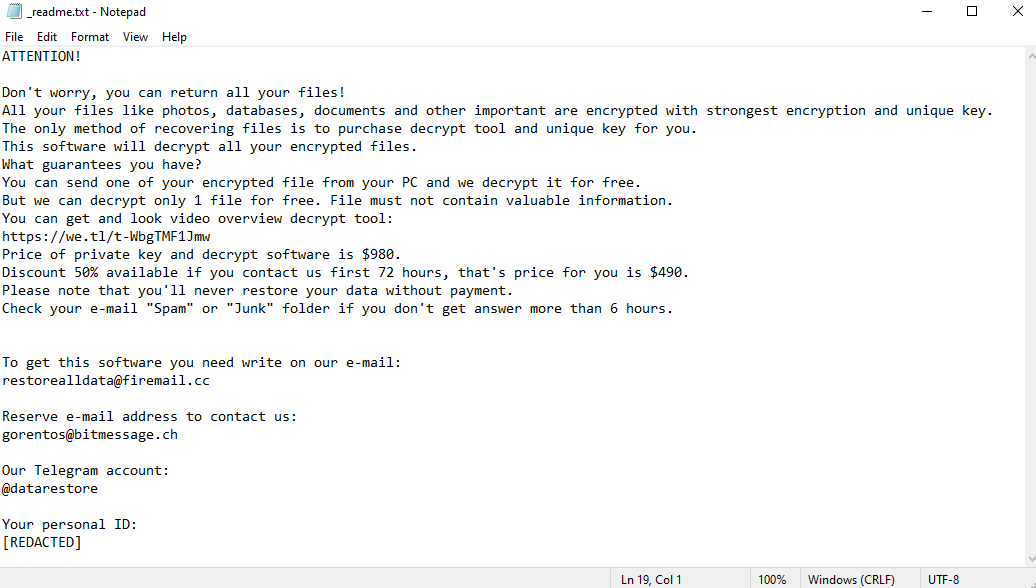
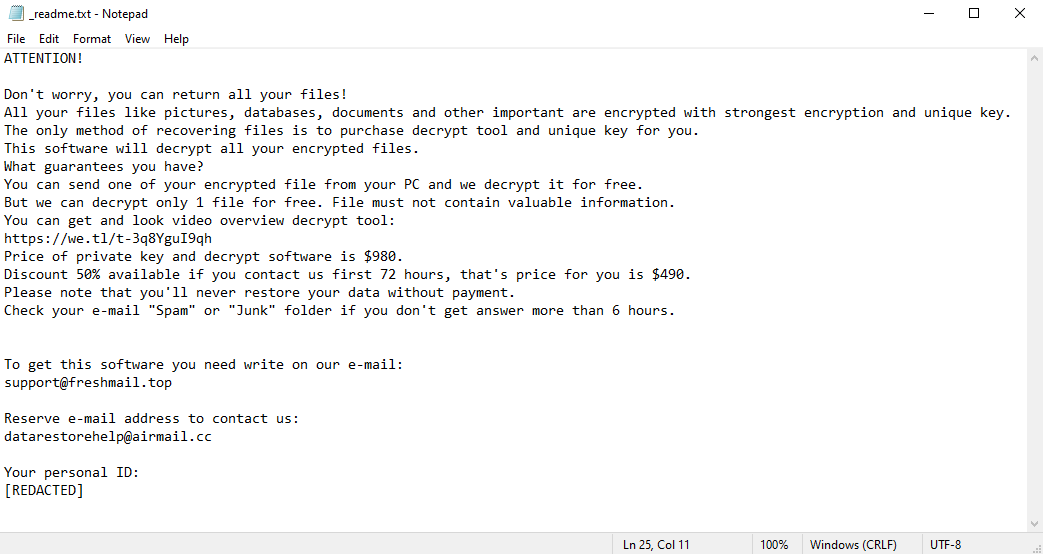
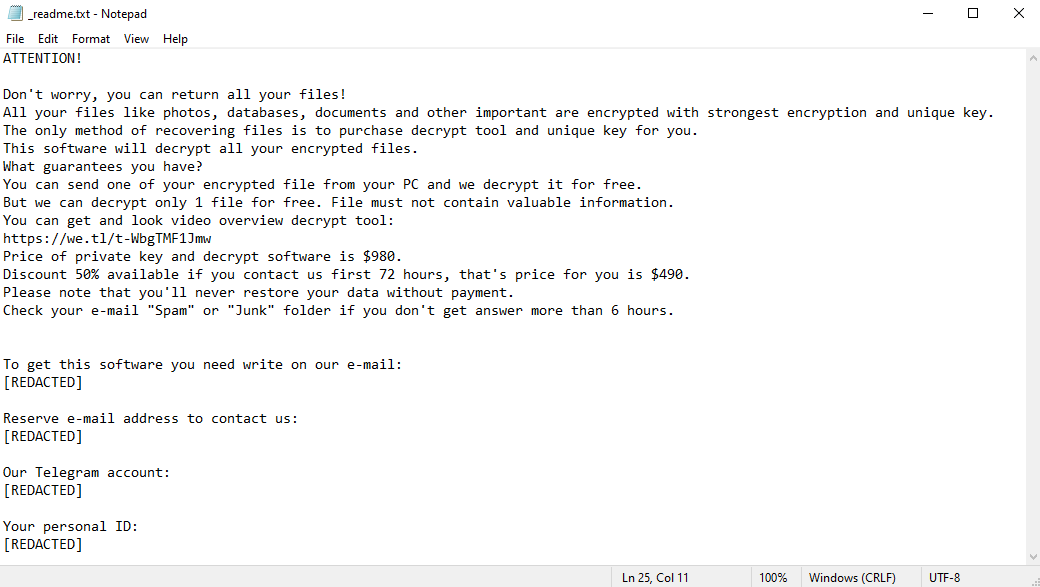
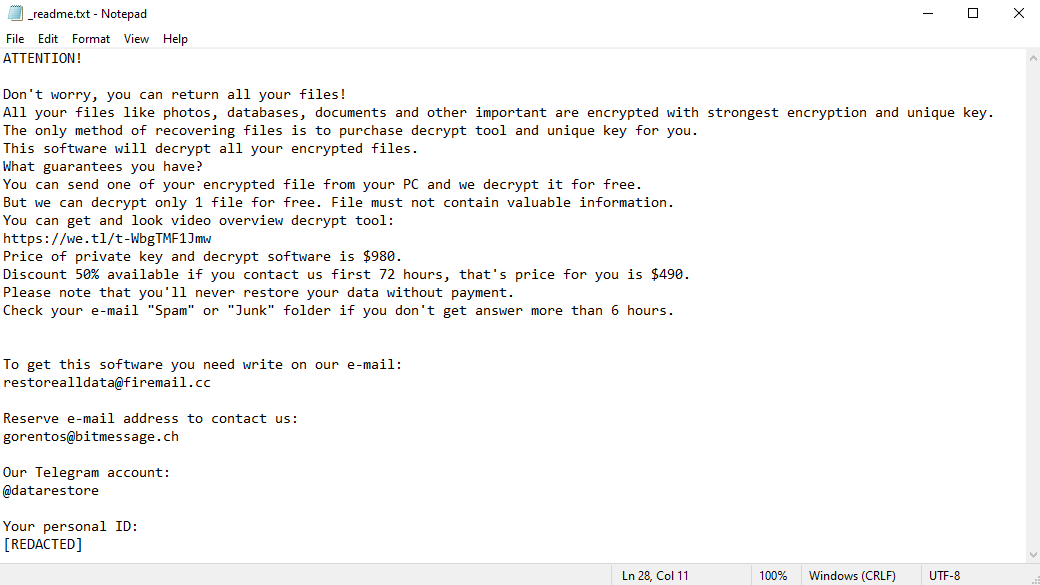
Ahgr ransomware is a malicious program that encrypts all files on your computer. Since encrypted files cannot be accessed, this is the same as losing them. The hackers behind Ahgr virus, however, can theoretically decrypt these files, and promise to do just that for a handsome amount of money. They may very well be lying, however. After encrypting the files, the virus creates a ransom note – a text file called “_readme.txt”. This file tells the victims how much money the hackers want and how to contact them. The price may very well shock you – one thousand dollars. Well, $980, to be precise, but it changes little. The price is lower for the first three days – $490 – to pressure the victims into paying. Still, few people would be willing to part with so much money. And, as we mentioned before, the hackers may not hold up their end of the bargain; many don’t bother decrypting the files after receiving payment. This is why you should investigate alternate ways to remove Ahgr ransomware and decrypt .ahgr files instead of dealing with these criminals. The guide below contains several such methods.