What is TeslaRVNG1.5 ransomware?
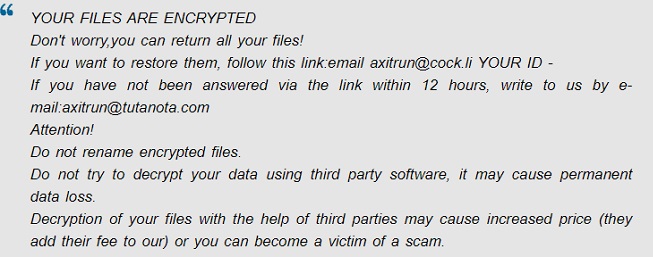
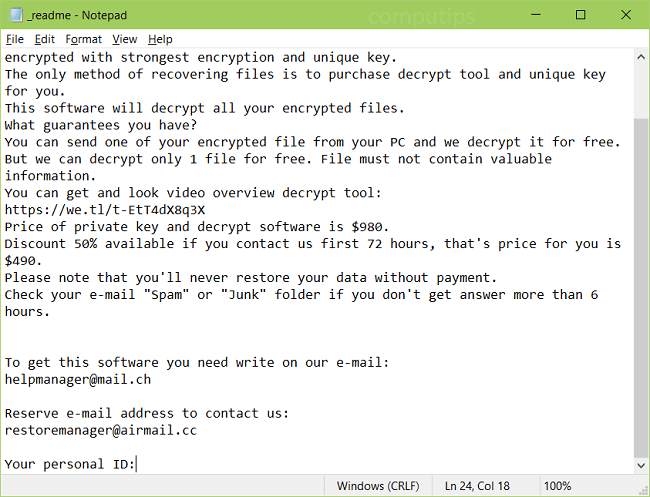
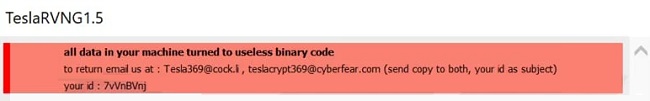
TeslaRVNG1.5 is a ransomware program from the Ouroboros family that encrypts files using a special infection algorithm. It renames encrypted files by adding victim ID, email address tesla369@cock.li and adding the extension “.teslarvng1.5” to file names to mark files with private access.