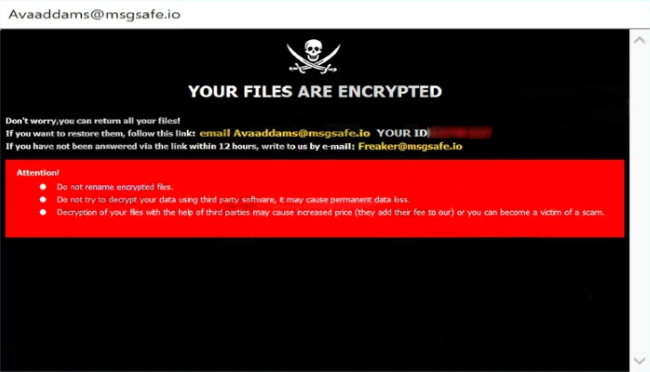
What is Avaad ransomware
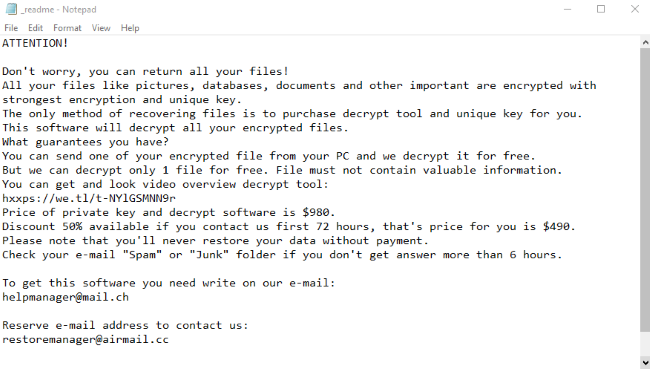
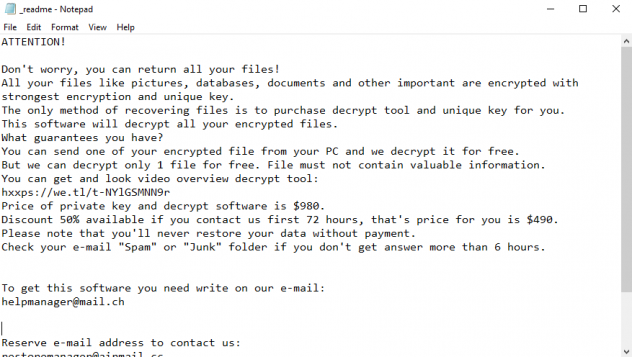
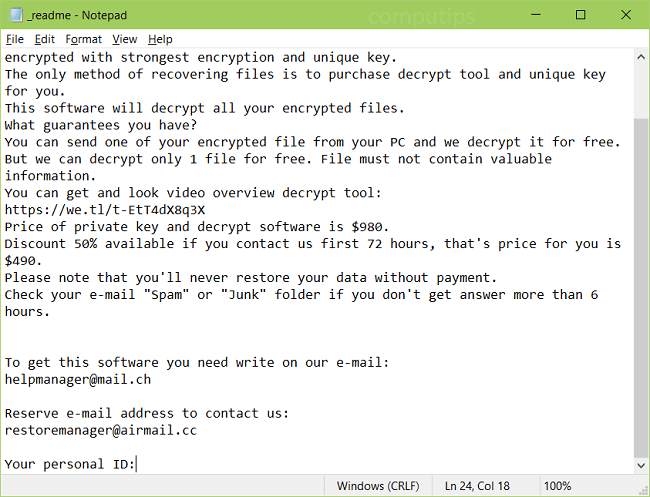
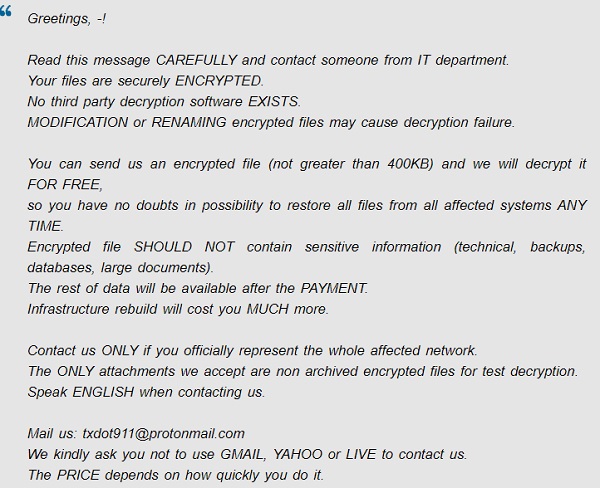
Avaad is a ransomware type of virus and it belongs to Dharma file-encryption ransomware family. This family is not new and contain a great amount of viruses. Talking exactly about Avaad ransomware, usually criminals spread it by the means of malicious installers. Victims face them on numerous file sharing services and torrent trackers. Criminals promote them as free or cracked software. Moreover, they can easily infect your computer or even network by the means of botnets and remote access terminals. If criminals are lucky to infect your device, Avaad begins to modify the registry folder and system processes. Then, by the means of these modifications, Avaad encrypts the data. As the result, your files get new “.id-*ID*.[Avaaddams@msgsafe.io].Avaad” extensions. We strongly recommend you not to try to remove Avaad ransomware and to decrypt “.Avaad” files by yourself without a guide. And if you need one, continue reading!