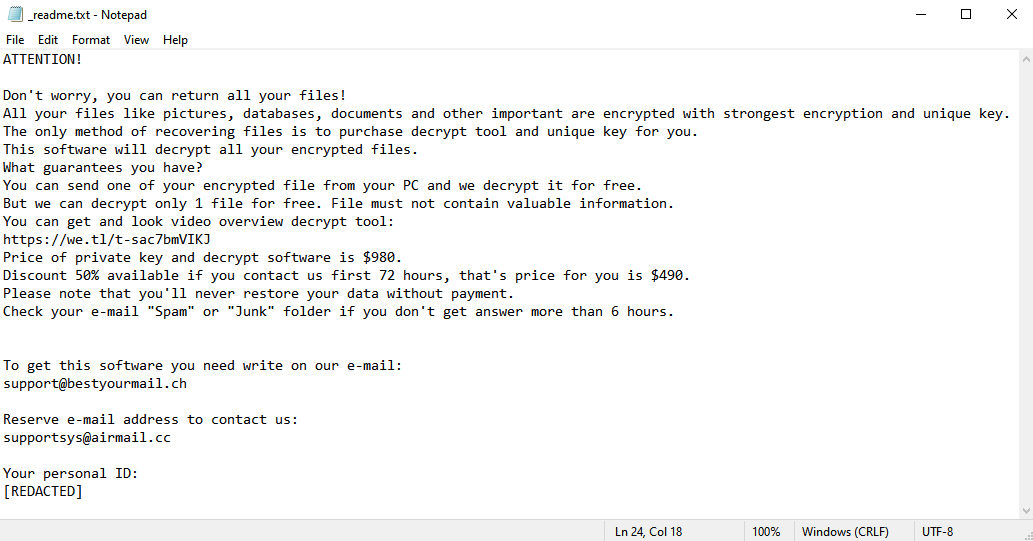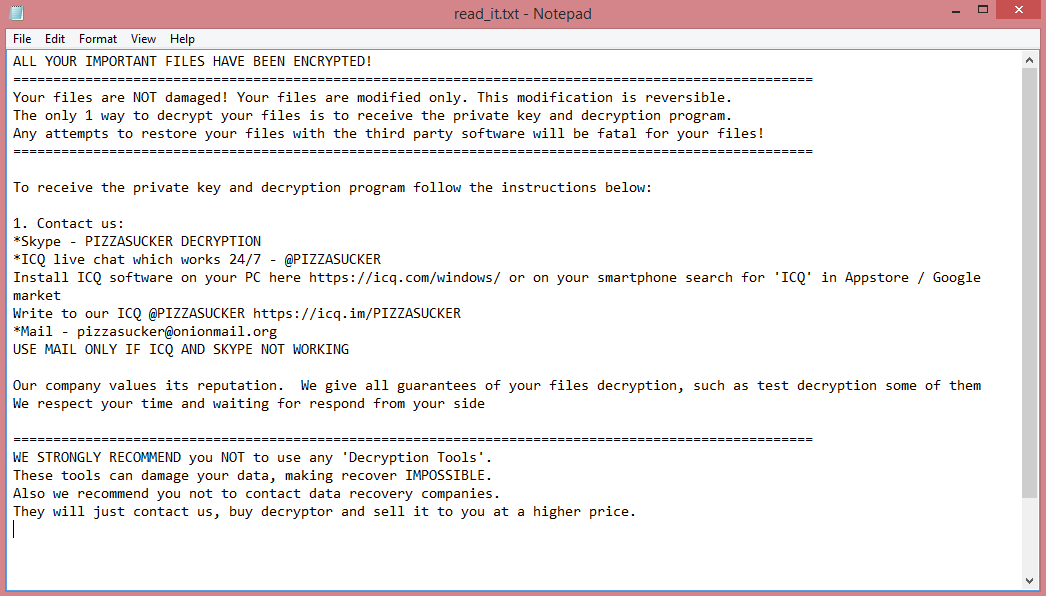
What is Pizzasucker ransomware
Pizzasucker is a illicit program that extorts money out of people by encrypting their files (ransomware). Encrypted files cannot simply be accessed; they need to be decrypted first. The hackers who wrote the virus offer the victim to do just that, for a large amount of money. The offer often includes psychological pressure and other tricks to get the victim to pay.
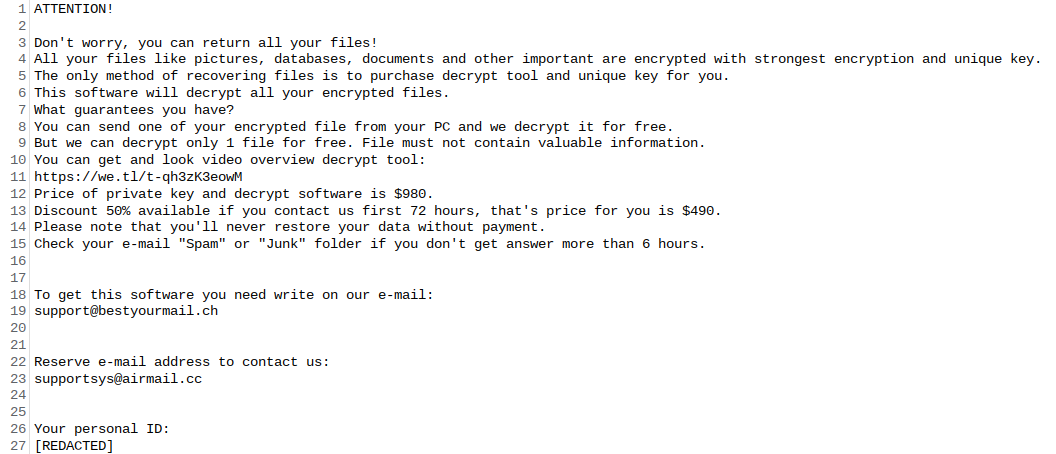
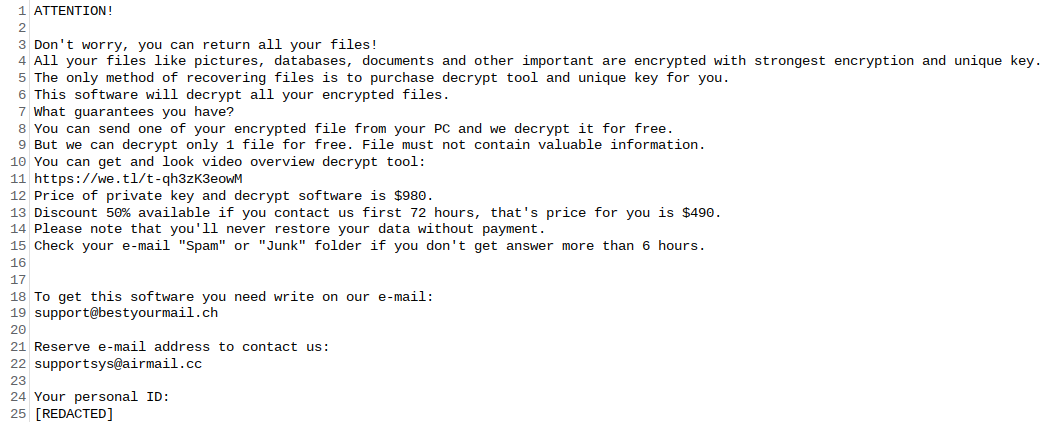
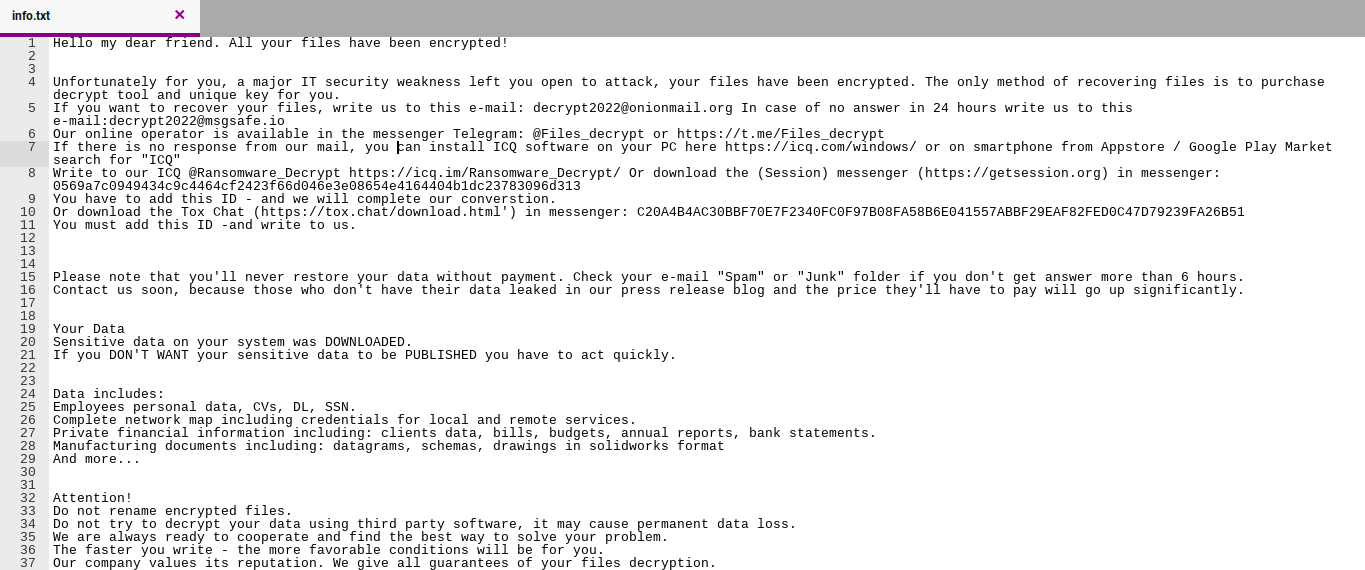
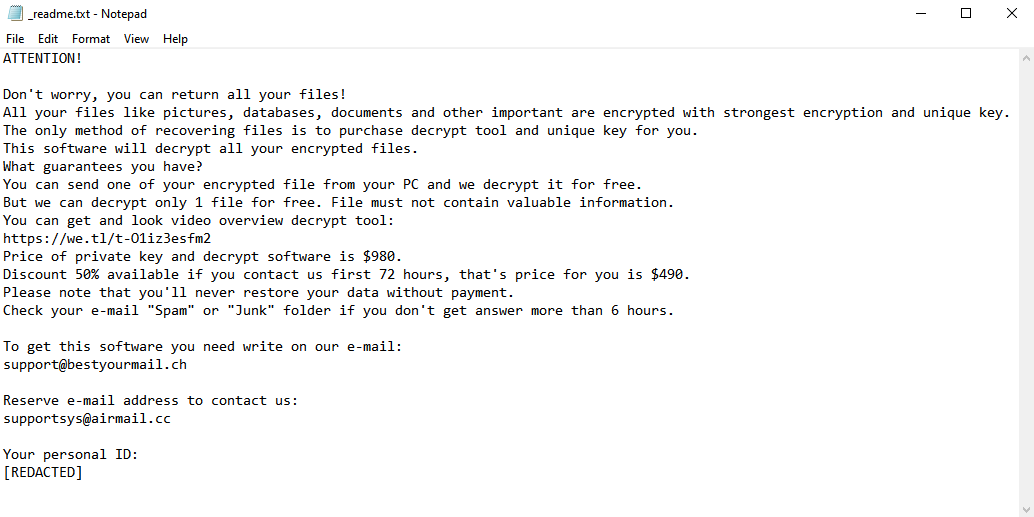
Most often such programs communicate these “offers” via a simple text file, referred to as a ransom note. The image above contains the full text of Pizzasucker’s ransom note, though it doesn’t really contain much beyond contact information.
In this case, the hackers went an extra mile to get their contacts as visible as possible; the virus gives all encrypted files .ICQ@PIZZASUCKER file extension.
As these cybercriminals often want a lot of money for their “services”, it is best to not pay them. Despite their reassurances to the contrary, it is possible to remove Pizzasucker for free, and you may be able to decrypt Pizzasucker files as well. The guide below will explain what to do.
![Encfiles ransom note:
Your files are now encrypted!
Your personal identifier:
[REDACTED]
All your files have been encrypted
And all your backup and NAS system deleted military grade ERASE Methods.
Now you should send us email with your personal identifier.
This email will be as confirmation you are ready to pay for decryption key.
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us.
After payment we will send you the decryption tool that will decrypt all your files.
If you want take back your files please contact us.
Email : dataprotection@tuta.io
Please send both email adress for contact us
Free decryption as guarantee!
Before paying you can send us up to 3 files for free decryption.
The total size of files must be less than 10Mb (non archived), and files should not contain
valuable information (databases, backups, large excel sheets, etc.).
How to obtain Bitcoins?
* The easiest way to buy bitcoins is LocalBitcoins site. You have to register, click
'Buy bitcoins', and select the seller by payment method and price:
https://localbitcoins.com/buy_bitcoins
* Also you can find other places to buy Bitcoins and beginners guide here:
http://www.coindesk.com/information/how-can-i-buy-bitcoins
Attention!
* Do not rename encrypted files.
* Do not try to decrypt your data using third party software, it may cause permanent data loss.
* Decryption of your files with the help of third parties may cause increased price
(they add their fee to our) or you can become a victim of a scam.
This is the end of the note. Read the guide below to learn how to remove Encfiles ransomware.](https://www.computips.org/wp-content/uploads/2022/09/how-to-remove-encfiles-ransomware.png)
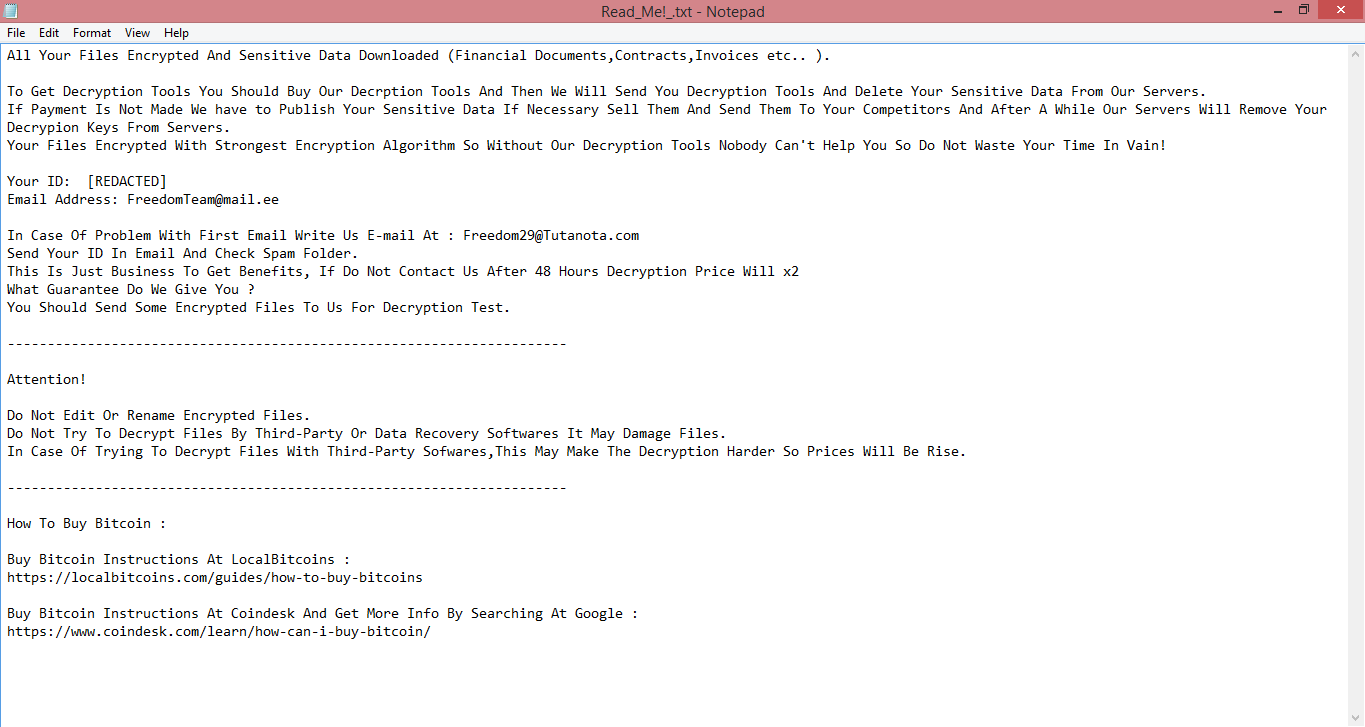
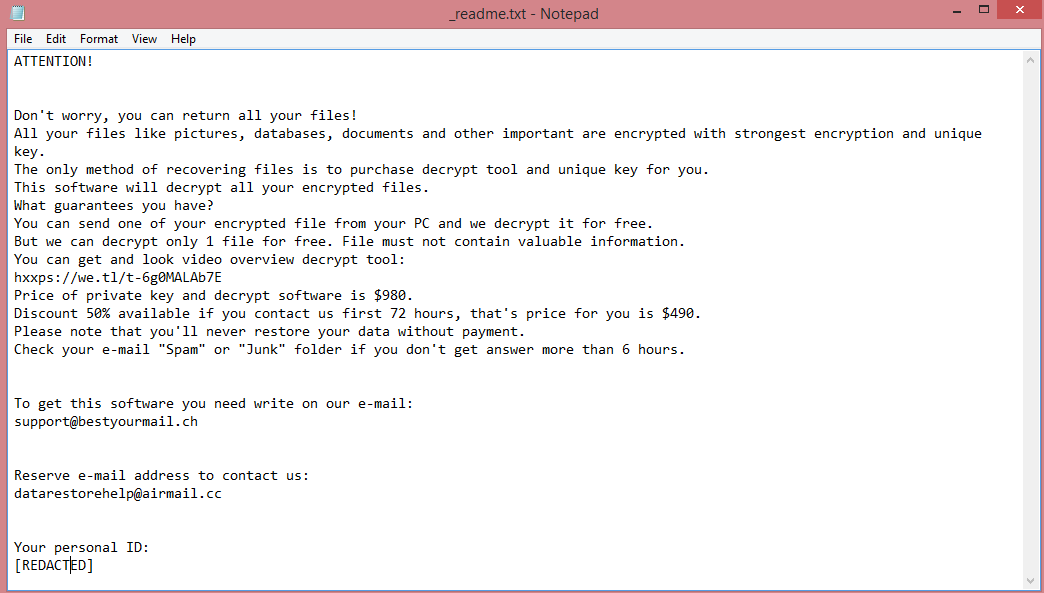
![IceFire ransom note:
********************Your network has been infected!!!********************
IMPORTANT : DO NOT DELETE THIS FILE UNTIL ALL YOUR DATA HAVE BEEN RECOVERED!!!
All your important files have been encrypted. Any attempts to restore your files with thrid -party software will be fatal for your files!
Restore your data possible only buying private key from us. We have also downloaded a lot of private data from your network. If you
do not contact us in a 5 days, we will post information about your breach on our public news webs.
You should get more information on our page, which is located in a Tor hidden network.
1.Download Tor browser - https://www.torproject.org/
2.Install Tor browser
3.Open link in Tor browser : kf6x3mjeqljqxjznaw65jixin7dpcunfxbbakwuitizytcpzn4iy5bad.onion
4. Follow the instructions on this page
Your account on our website
*******************************************************************************
username: [REDACTED]
password: [REDACTED]
ATTENTION:
1.Do not try to recover files yourself, this process can damage your data and recovery will become impossible.
2.Do not waste time trying to find the solution on the internet. The longer you wait, the higher will become the decryption key price.
3.Tor Browser may be blocked in your country or corporate network. Use Tor Browser over VPN.
This is the end of the ransom note. The guide below will explain how to remove IceFire ransomware.](https://www.computips.org/wp-content/uploads/2022/08/how-to-remove-icefire-ransomware.png)