What is Fate ransomware?
Fate is a new strain of STOP/Djvu ransomware. In most aspects, it is identical to other STOP/Djvu strains. However, the name of the virus, the hackers’ contact information, and the encryption method obviously differ. Fatp is another recent STOP/Djvu strain; if you compare the two, you will see that they’re very similar to each other. Even the ransom note and the demands are the same.
This means that the easiest way to distinguish these viruses is their name. Fate ransomware renames the files it encrypts, adding .fate file extension. Meaning, “note.docx” would be renamed “note.docx.fate”. This extension is the name of the virus.
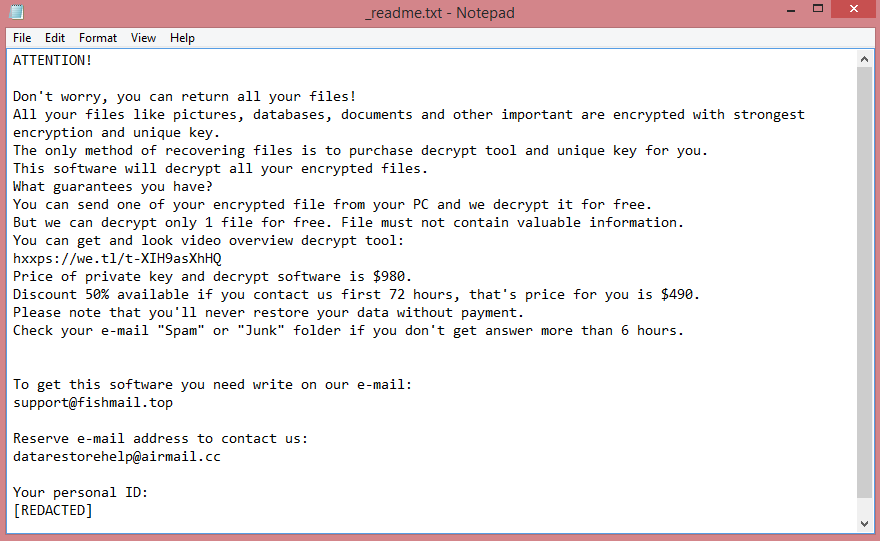
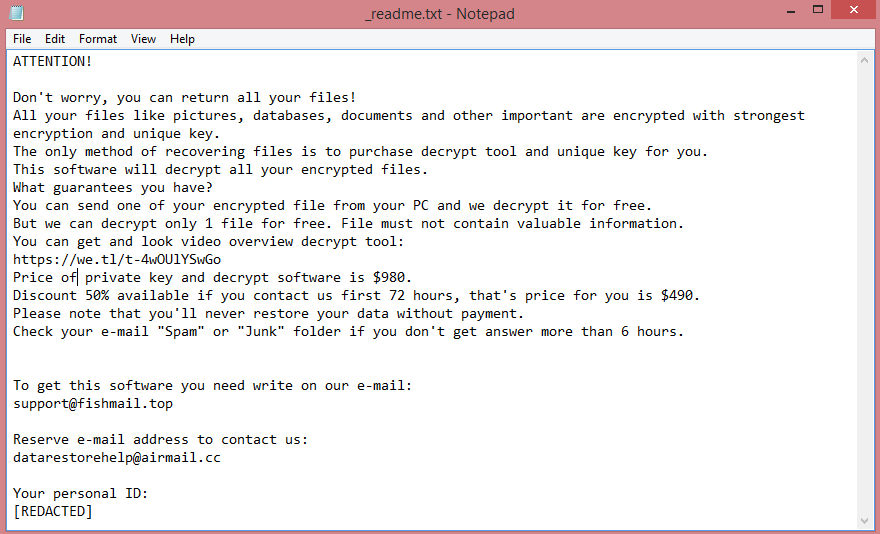
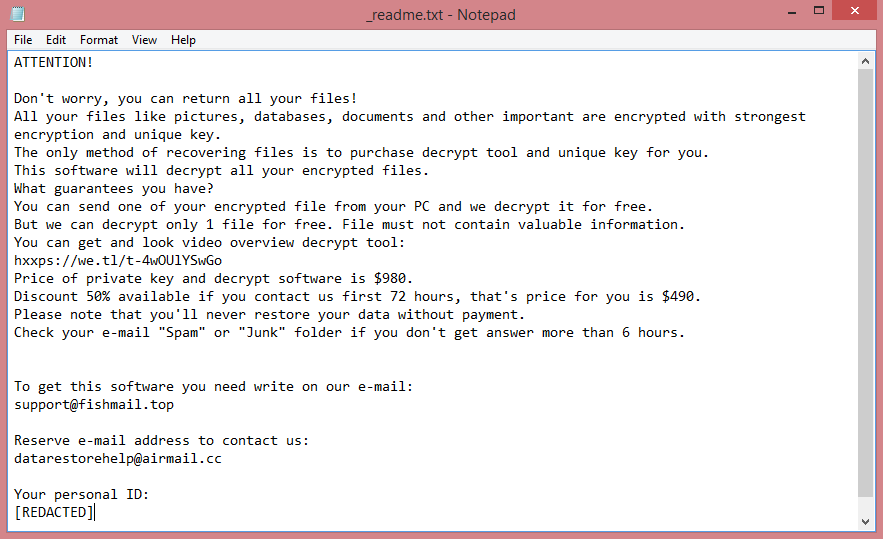
The ransom note, meanwhile, is located on the Desktop and bears the name “_readme.txt”. The image above contains the full text of the note, but basically, the hackers want $980 for decrypting the files. Those who pay within 3 days of infection are offered a 50% discount; the hackers demand $490 from them.
Don’t fall for this psychological trick. This discount is not a good deal, since you shouldn’t pay anything in the first place, and the sense of urgency this offer creates is completely manufactured. Beyond that, it is common for these hackers to simply disappear once they get the money, without decrypting anything at all.
Instead, you may follow our guide that will explain how to remove Fate ransomware and decrypt .fate files without involving these criminals.
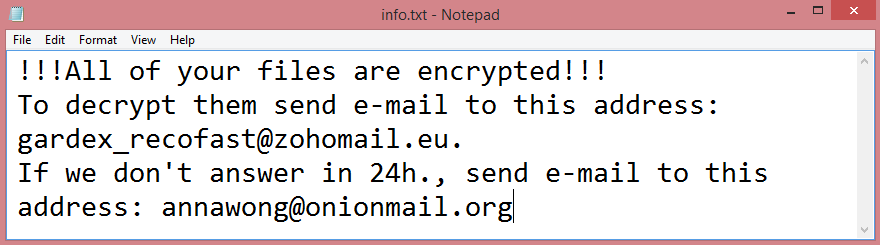
![ZeRy ransom note:
HELLO!
As you can see all your files are encrypted
To get them back, you have to pay me 0.05 bitcoins
At this address: bc1qgfef9nlwffftl6m5qet95yxa0x7arah0h580gs
After you have made the payment, contact me at this email address: zery@tuta.io
with this topic: [REDACTED]
After payment confirmation, you will receive the keys and a tutorial to decrypt your files.
If you don't own bitcoin, you can buy it very easily here:
www.localbitcoins.com
www.paxful.com
www.coinmama.com
You can find a larger list here:
hxxps://bitcoin.org/en/exchanges
If you don't contact me or you won't make the payment in 5 days
I will assume that you do not want to recover your files
and as a result I will delete the keys generated for your PC.
This is the end of the note. Below you will find a guide explaining how to remove ZeRy ransomware.](https://www.computips.org/wp-content/uploads/2022/11/how-to-remove-zery-ransomware.png)
![RAMP ransom note:
Увага! Всі ваші файли зашифровані!
Щоб відновити свої файли та отримати до них доступ,
надішліть SMS з текстом [REDACTED] Користувачеві Telegram @WHITE_ROS4
У вас є 1 спроба ввести код. Якщо це
кількість буде перевищено, всі дані необоротно зіпсуються. Бувши
обережні при введенні коду!
Channels: @white_ros4bio | @vip_swatting |
привет от Killnet
Keygroup привет
This is the end of the note. Below you will find a guide explaining how to remove RAMP ransomware.](https://www.computips.org/wp-content/uploads/2022/11/how-to-remove-ramp-ransomware.png)
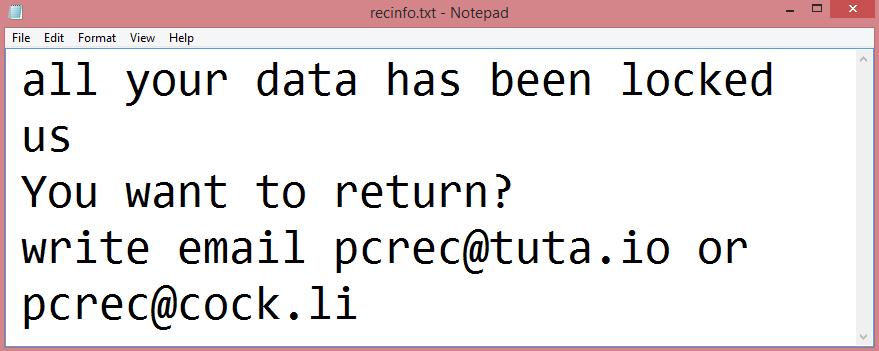
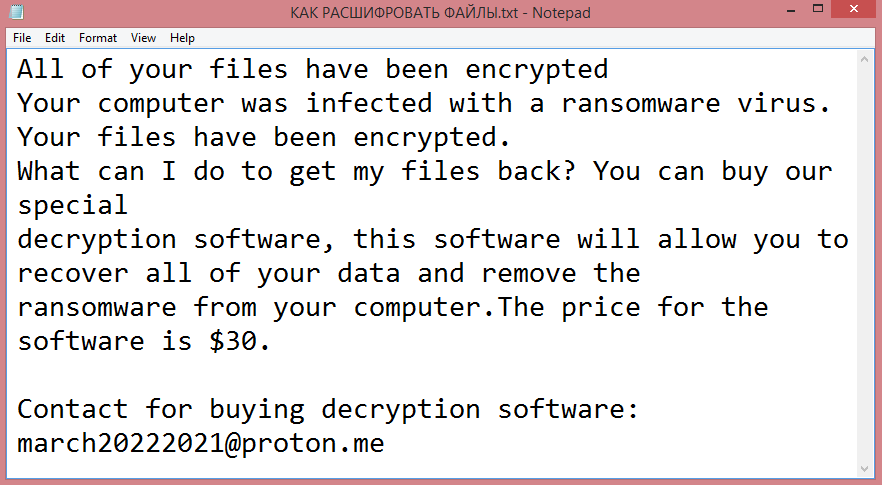
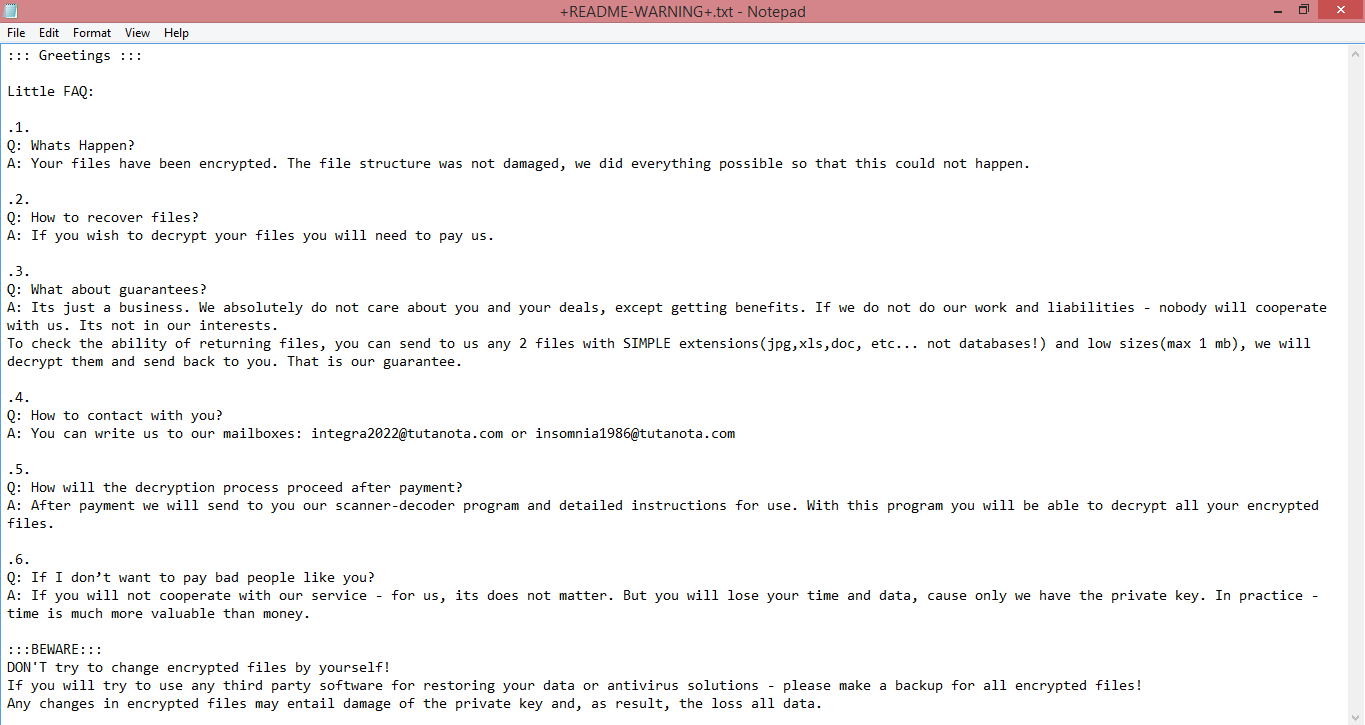
![Rar ransom note:
All your files have been encrypted. If you want to restore them, write us to the e-
mail:spystar1@onionmail.com
Write this ID in the title of your message [REDACTED]
You can also write us using this Telegram Username: @Rar_support
Do not rename encrypted files.
Do not try to decrypt your data using third-party software and sites. It may cause permanent data loss.
The decryption of your files with the help of third parties may cause increased prices (they add their
fee to our), or you can become a victim of a scam.
This is the end of the note. Below you will find a guide explaining how to remove Rar ransomware.](https://www.computips.org/wp-content/uploads/2022/11/how-to-remove-rar-ransomware.png)