What is Isza ransomware?
Isza is a ransomware virus that has been discovered recently. It operates under the same algorithm as any other ransomware program would; it encrypts the victim’s files, renames them (giving the files .isza file extension), and creates a ransom note named “_readme.txt”.
Isza belongs to the STOP/Djvu ransomware family (a group of viruses that share most of their code). As a consequence of this, it is nearly identical to other ransomware in this family (such as Bttu). Should you choose to compare them, you will see that the demands and even the text in the ransom note are pretty much the same.
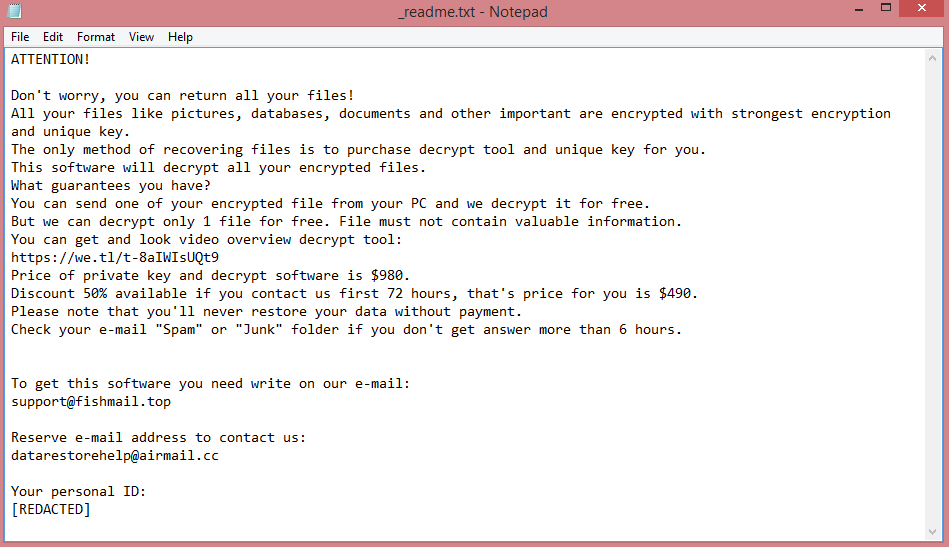
For reference purposes, Isza’s ransom note is pictured on the image above; it contains the entirety of its text. To summarize, the virus wants $980 in ransom, or $490 if the victim pays within several days.
Paying the hackers, however, is generally a bad idea, denounced by many organizations around the globe. That is because these criminals have a reputation for taking the money and disappearing without decrypting the files. But there are other ways to remove Isza ransomware and decrypt .isza files; the guide below will teach you some of them.
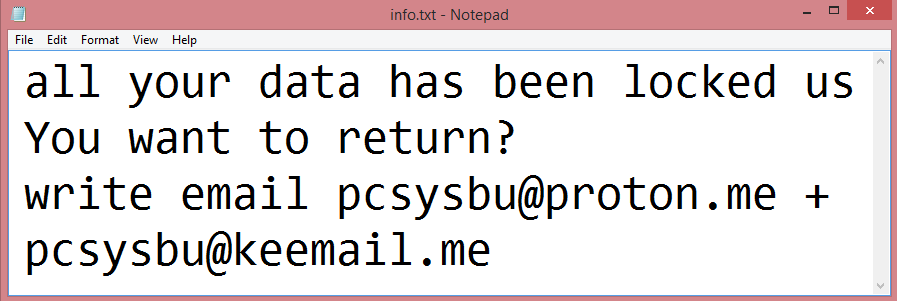
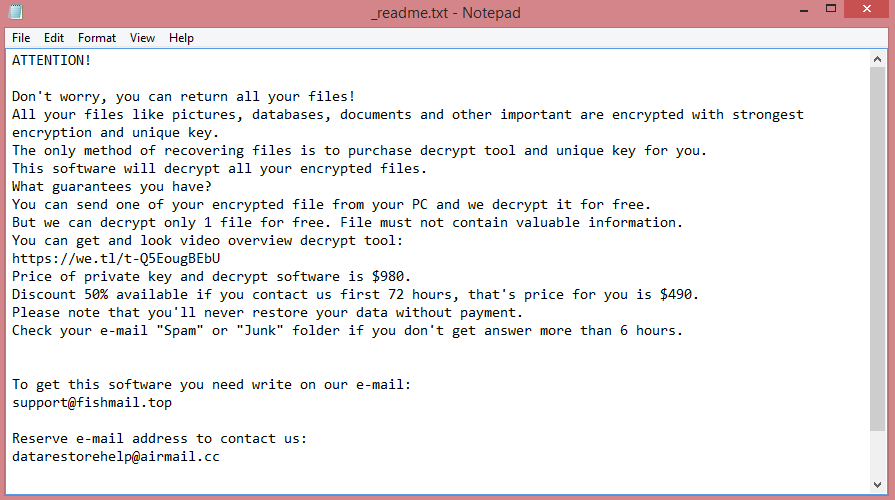
![HentaiLocker ransom note:
Well, looks like your files are encrypted by HentaiLocker.
But don't worry, you can still get them back. You need to use our special decrypter to get your files
back.
To get decrypter, you need to contact me by email (hlockdev@rungel.net) and send these infos :
- PC name (your PC name is [REDACTED])
- username (your username is [REDACTED])
- your personal ID ([REDACTED])
- date when your PC got infected
After i'll get these infos, you will get a link to download our decrypter...
...maybe i'll give it... maybe not.
This is the end of the note. Below you will find a guide explaining how to remove HentaiLocker ransomware.](https://www.computips.org/wp-content/uploads/2022/12/how-to-remove-hentailocker-ransomware.png)
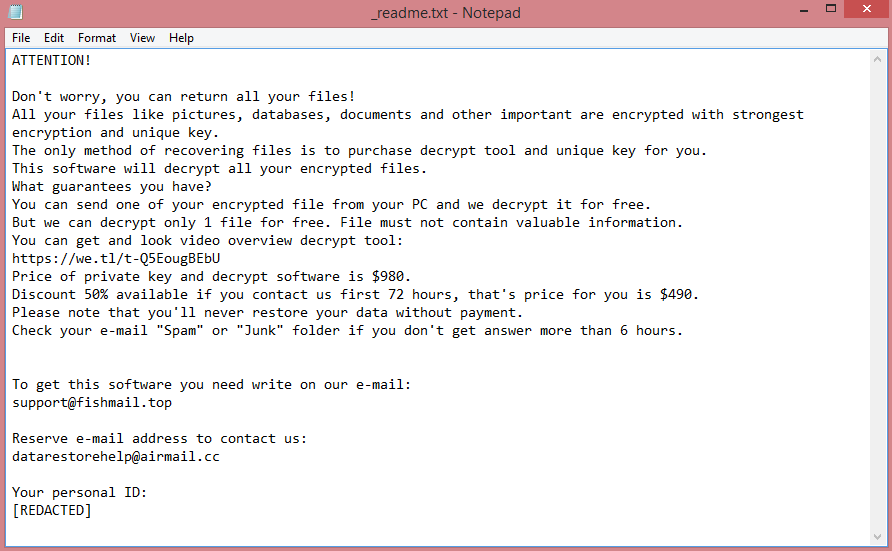
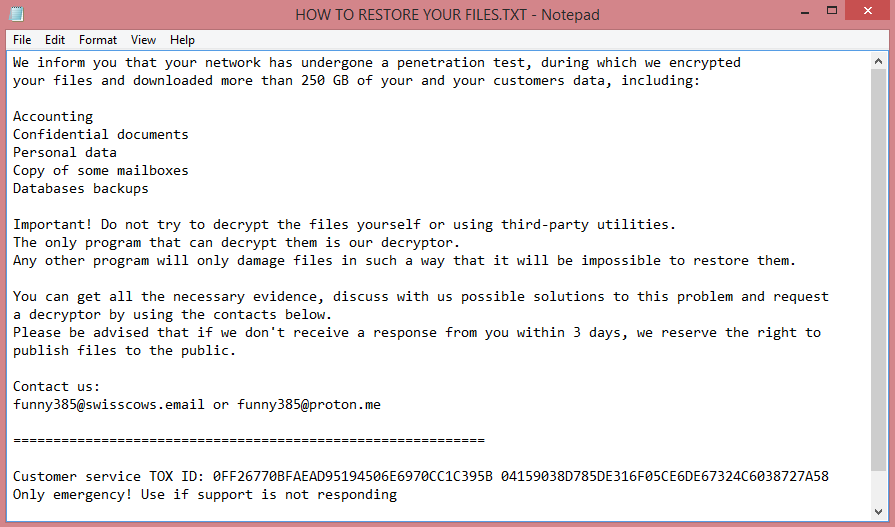
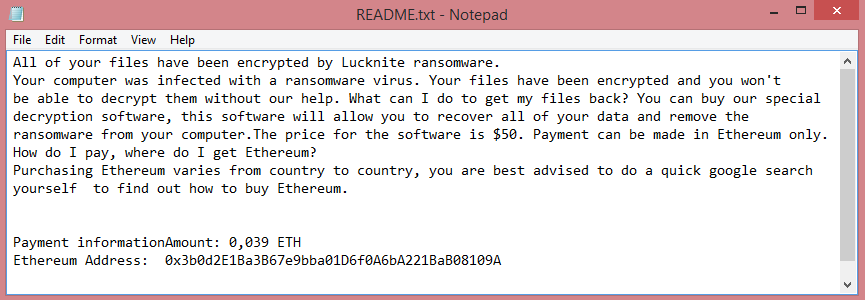
![MEOW ransom note:
MEOW! MEOW! MEOW!
Your files has been encrypted!
Need decrypt? Write to e-mail:
meowcorp2022@aol.com
meowcorp2022@proton.me
meowcorp@msgsafe.io
meowcorp@onionmail.org
or Telegram:
@meowcorp2022
@meowcorp123
Uniq ID: [REDACTED]
This is the end of the note. Below you will find a guide explaining how to remove MEOW ransomware.](https://www.computips.org/wp-content/uploads/2022/12/how-to-remove-meow-ransomware.png)