What is District ransomware?
District ransomware is a recently discovered computer virus. It encrypts victims’ data with the intention of holding it ransom; for this reason, it has been categorized as ransomware.
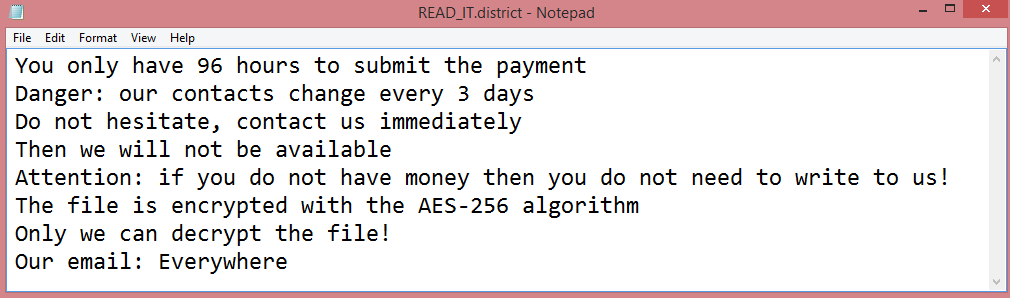
In addition to encrypting the files, District also renames them. The hackers’ e-mail, “altdelete@cock.li”, is added to the end of file names, as well as .district file extension. It also creates a ransom note named “READ_IT.district”. This note can be read on the image above.
The hackers say that victims have only 96 hours to pay them, and that their contacts change every three days. This, however, is inconsistent; 96 hours is four days, not three. This is most likely a lie designed to scare the victims into paying. The note does not mention how much the hackers want for decrypting the files. It is unclear whether this is intentional or an oversight on their part.
Regardless, you’re advised not to contact these criminals. These unscrupulous characters have a reputation of disappearing after receiving the money, without decrypting any files at all. This is why exploring other ways to remove District ransomware and decrypt .district files is a worthwhile endeavor. Some of them can be learned from the guide below.
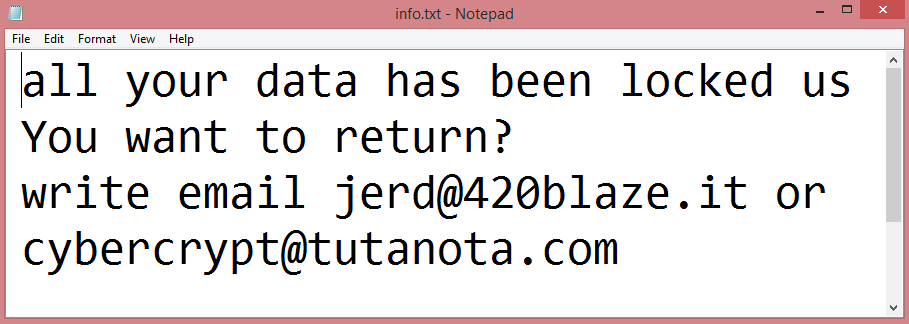
![Theva ransom note:
All your files have been encrypted due to a security problem with your PC.
If you want to restore them, write us to the e-mail: sql772@aol.com
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us.
After payment we will send you the decryption tool that will decrypt all your files.
FREE DECRYPTION AS GUARANTEE
Before paying you can send to us up to 3 files for free decryption.
Please note that files must NOT contain valuable information
and their total size must be less than 10Mb
How to obtain Bitcoins
The easiest way to buy bitcoin is LocalBitcoins site.
You have to register, click Buy bitcoins and select the seller
by payment method and price
https://localbitcoins.com/buy_bitcoins
Attention!
Do not rename encrypted files
Do not try to decrypt your data using third party software, it may cause permanent data loss
If you not write on e-mail in 3 days - your key has been deleted and you cant decrypt your files
Your ID:
[REDACTED]
This is the end of the note. Below, you will find a guide explaining how to remove Theva ransomware.](https://www.computips.org/wp-content/uploads/2022/12/how-to-remove-theva-ransomware.png)
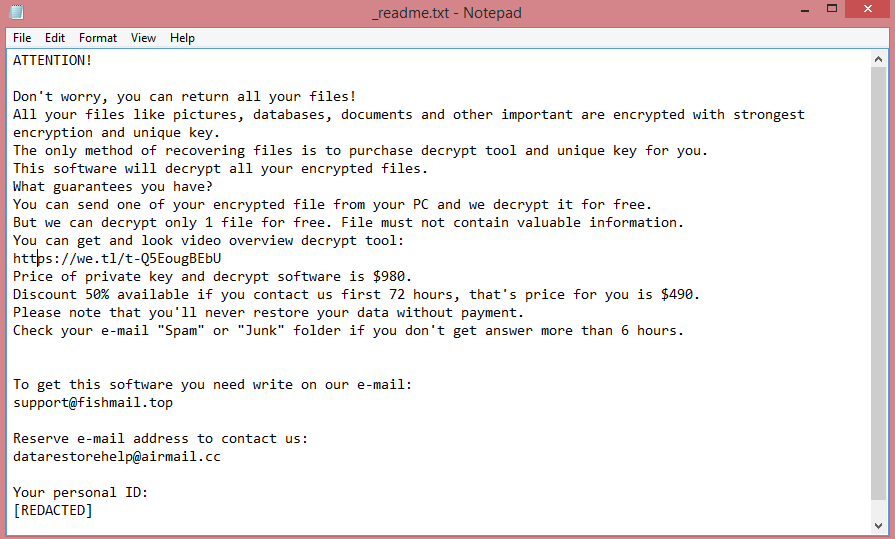
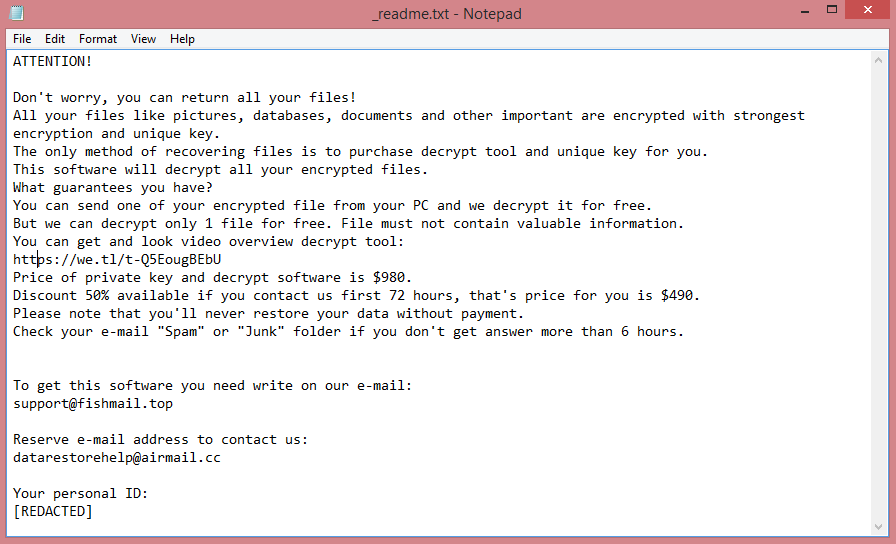
![Rans_recovery ransom note:
~~~ Hello! Your company has been hacked! ~~~
Your data are stolen and encrypted
What guarantees that we will not deceive you?
We are not a politically motivated group and we do not need anything other than your money.
If you pay, we will provide you the programs for decryption and we will delete your data.
Life is too short to be sad. Be not sad, money, it is only paper.
If we do not give you decrypters, or we do not delete your data after payment, then nobody will pay us in
the future.
Therefore to us our reputation is very important. We attack the companies worldwide and there is no
dissatisfied victim after payment.
You need to contact us by email rans_recovery@aol.com and decrypt some files for free
Your personal ID:
[REDACTED]
Provide your personal ID in the email
Warning! Do not DELETE or MODIFY any files, it can lead to recovery problems!
Warning! If you do not pay the ransom we will attack your company repeatedly again!
This is the end of the note. Below you will find a guide explaining how to remove Rans_recovery ransomware.](https://www.computips.org/wp-content/uploads/2022/12/how-to-remove-rans_recovery-ransomware.png)
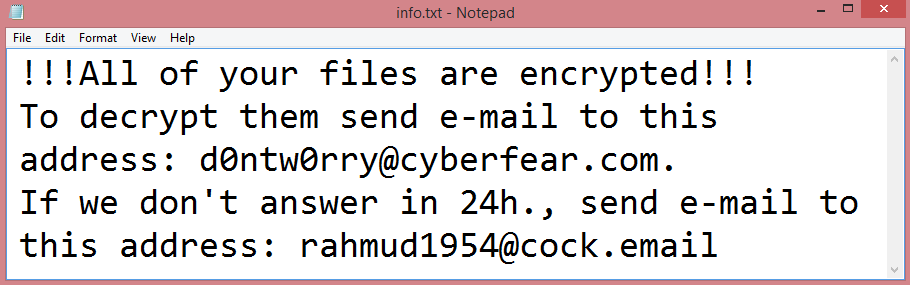
![Sunjun ransom note:
All your files have been encrypted. If you want to restore them, write us to the e-
mail:sunjun3412@mailfence.com
inCase of no answer :sunjun3416@mailfence.com
Write this ID in the title of your message [REDACTED]
send RSAKEY file stored in C:/ProgramData or other drives in email
Do not rename encrypted files.
Do not try to decrypt your data using third-party software and sites. It may cause permanent data loss.
The decryption of your files with the help of third parties may cause increased prices (they add their fee
to our), or you can become a victim of a scam.
This is the end of the note. Below you will find a guide explaining how to remove Sunjun ransomware.](https://www.computips.org/wp-content/uploads/2022/12/how-to-remove-sunjun-ransomware.png)
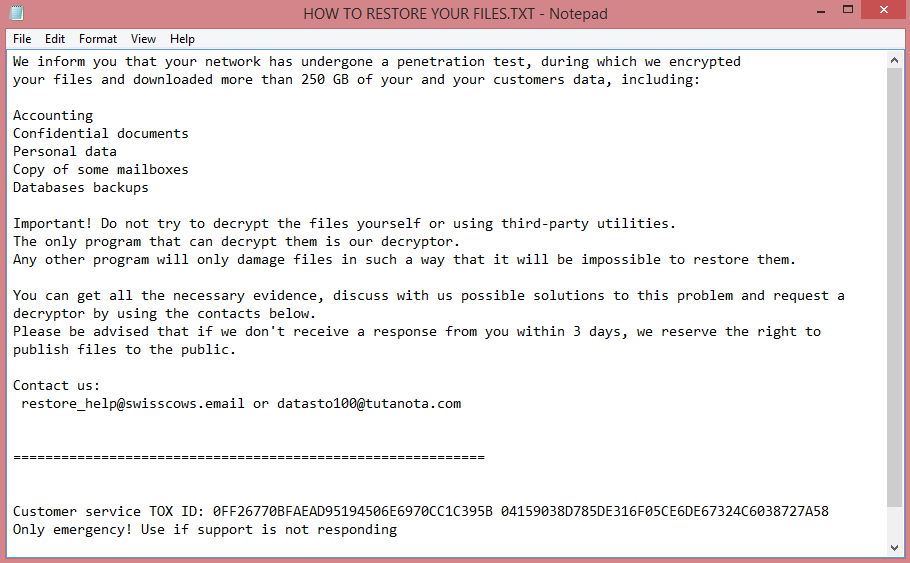
![Black Hunt ransom note:
As you can see we have penetrated your whole network due some critical network insecurities
All of your files such as documents, dbs and... Are encrypted and we have uploaded many important data from
your machines,
and believe we us we know what should we collect.
However you can get your files back and make sure your data is safe from leaking by contacting us using
following details :
Primary email :sentafe@rape.lol
Secondary email(backup email in case we didn't answer you in 24h) :justin@cyberfear.com ,
magicback@onionmail.org
Your machine Id : [REDACTED]
use this as the title of your email
(Remember, if we don't hear from you for a while, we will start leaking data)
This is the end of the note. Below you will find a guide explaining how to remove Black Hunt ransomware.](https://www.computips.org/wp-content/uploads/2022/12/how-to-remove-black-hunt-ransomware.png)