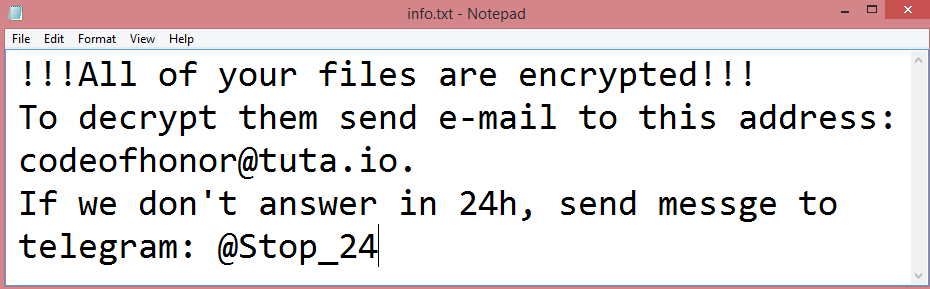
![Masons ransom note:
Attention! All your files are encrypted!
To restore your files and access them,
send an SMS with the text [REDACTED] to the User Telegram
@mineralIaha/@root_king1
You have 1 attempts to enter the code. If this
amount is exceeded, all data will irreversibly deteriorate. Be
careful when entering the code!
Glory @six62ix
This is the end of the note. Below you will find a guide explaining how to remove Masons ransomware.](https://www.computips.org/wp-content/uploads/2023/02/how-to-remove-masons-ransomware.png)
What is Masons ransomware?
Masons is a recently discovered virus that falls under the ransomware category. These viruses are designed to make money for the hackers by extorting it from the victims. The virus encrypts the data on the victim’s computer, which renders it inaccessible. Then, the virus demands money to decrypt the data. Many hackers behind ransomware are targeting companies, but regular people fall victims to ransomware as well.
Masons renames the files after encrypting them; they are given .masons file extension. This means that a file that was previously named “image.jpg” would become “image.jpg.masons”, for example. This is useful for identifying the virus.
The demands of the hacker are communicated using a text file called “six62ix.txt”. The full text of this ransom note can be read on the image above; sadly, it contains nothing of interest. The victim is not told how much they have to pay, merely instructed to contact the hacker on Telegram.
However, this is not a good idea. Nothing prevents the hacker from simply taking your money and disappearing; there’s no guarantee they will decrypt your files. This is why you should learn about alternate ways to remove Masons ransomware and decrypt .masons files. The guide below is a useful resource, describing several such ways.
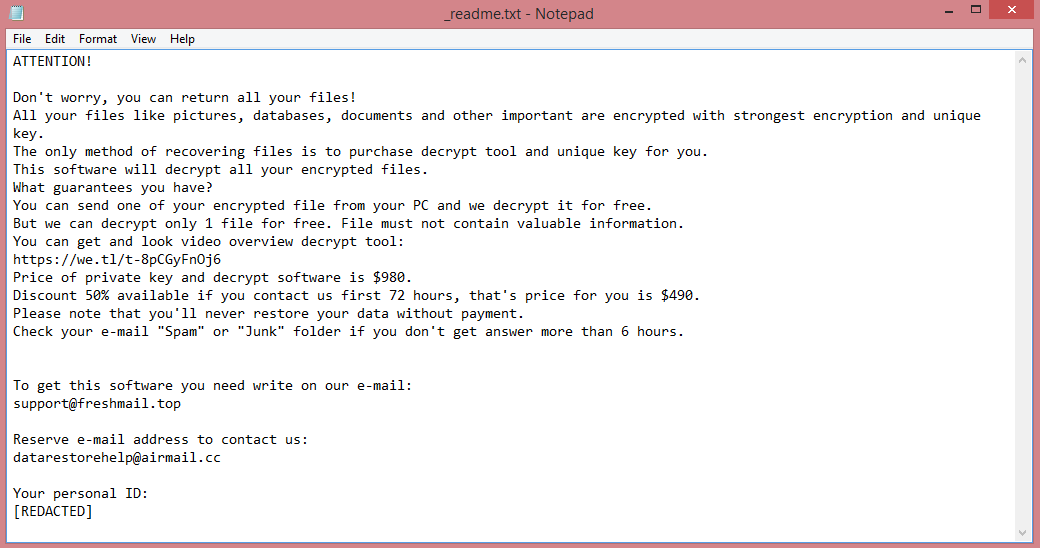
![ZFX ransom note:
::: Hey :::
Small FAQ:
.1.
Q: What's going on?
A: Your files have been encrypted. The file structure was not affected, we did our best to prevent this from happening.
.2.
Q: How to recover files?
A: If you want to decrypt your files, you will need to pay us.
.3.
Q: What about guarantees?
A: It's just business. We are absolutely not interested in you and your transactions, except for profit. If we do not fulfill our work and obligations, no one will cooperate with us. It's not in our interest.
To check the possibility of returning files, you can send us any 2 files with SIMPLE extensions (jpg, xls, doc, etc... not databases!) and small sizes (max 1 mb), we will decrypt them and send them back to you. This is our
guarantee.
.4.
Q: How to contact you?
A: You can write to us at our mailboxes: CryptedData@tfwno.gf
.5.
Q: How will the decryption process take place after payment?
A: After payment, we will send you our scanner-decoder program and detailed instructions for use. With this program you will be able to decrypt all your encrypted files.
.6.
Q: If I don't want to pay bad people like you?
A: If you do not cooperate with our service - it does not matter to us. But you will lose your time and data because only we have the private key. In practice, time is much more valuable than money.
:::BEWARE:::
DO NOT try to modify encrypted files yourself!
If you try to use third party software to recover your data or antivirus solutions - back up all encrypted files!
Any changes to the encrypted files may result in damage to the private key and, as a result, the loss of all data.
Note:
::::::IF WE HAVE NOT RESPONSE YOU BY MAIL WITHIN 24 HOURS::::::
Spare contact for communication:
If we have not answered your email within 24 hours, you can contact us via the free messenger qTox
Download from the link https://tox.chat/download.html
Next go qTox 64-bit
after downloading the program, install it and go through a short registration.
Our Tox ID
[REDACTED]
This is the end of the note. Below you will find a guide explaining how to remove ZFX ransomware.](https://www.computips.org/wp-content/uploads/2023/01/how-to-remove-zfx-ransomware.png)
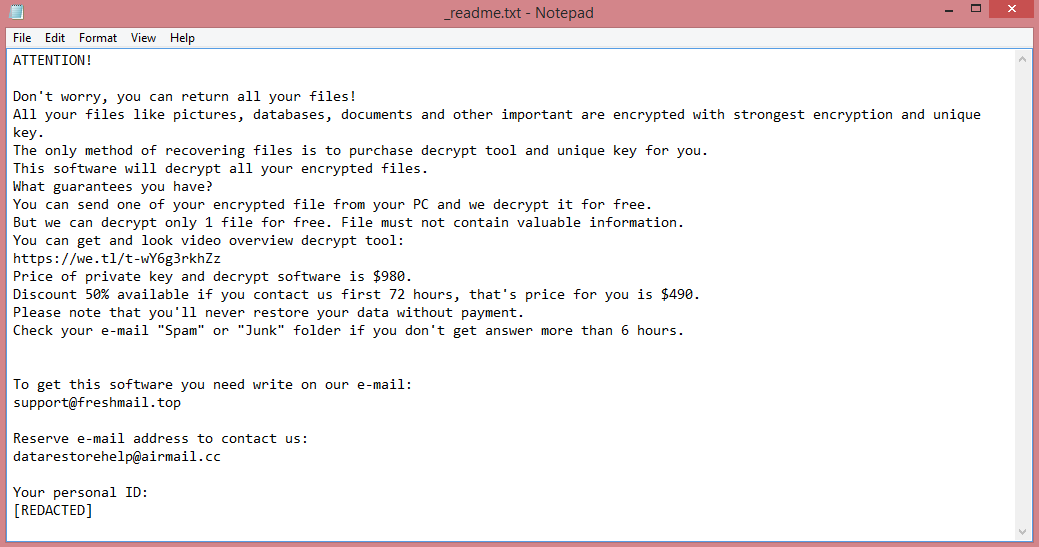
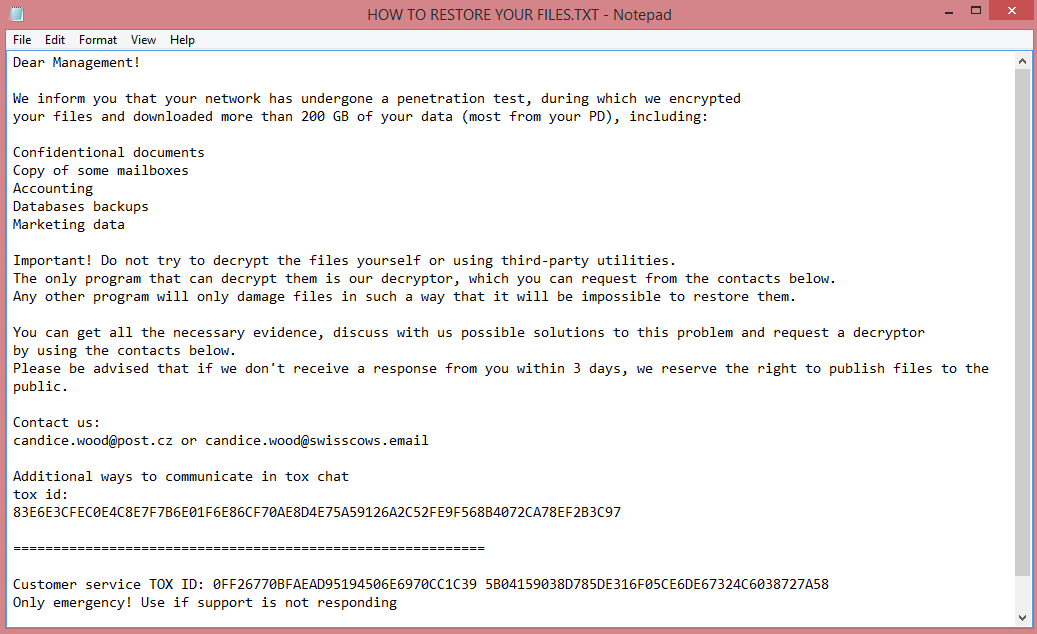
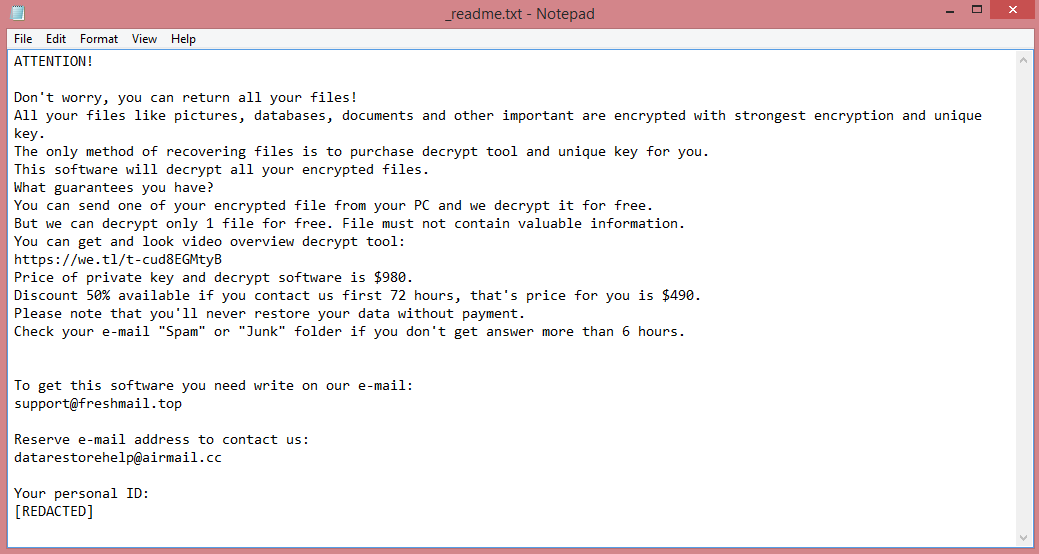
![BoY ransom note:
ATTENTION!!!
All your files have been encrypted!
Files can only be decrypted with the keys that have been generated for your PC!
The amount you have to pay to get the keys is 0.06 Bitcoin
We do not accept another payment method!
This is where you need to send bitcoin:
bc1q6x4kev9pefay37uctaq9ggqmxrg7a6txn2tanf
After sending, contact us at this email address: boyka@tuta.io
With this subject: [REDACTED]
Use the sites below to quickly buy bitcoin
www.localbitcoins.com
www.paxful.com
Another list of sites can be found here:
https://bitcoin.org/en/exchanges
After confirming the payment, you will receive a tutorial and the keys for decrypting the files.
This is the end of the note. Below you will find a guide explaining how to remove BoY ransomware.](https://www.computips.org/wp-content/uploads/2023/01/how-to-remove-boy-ransomware.png)
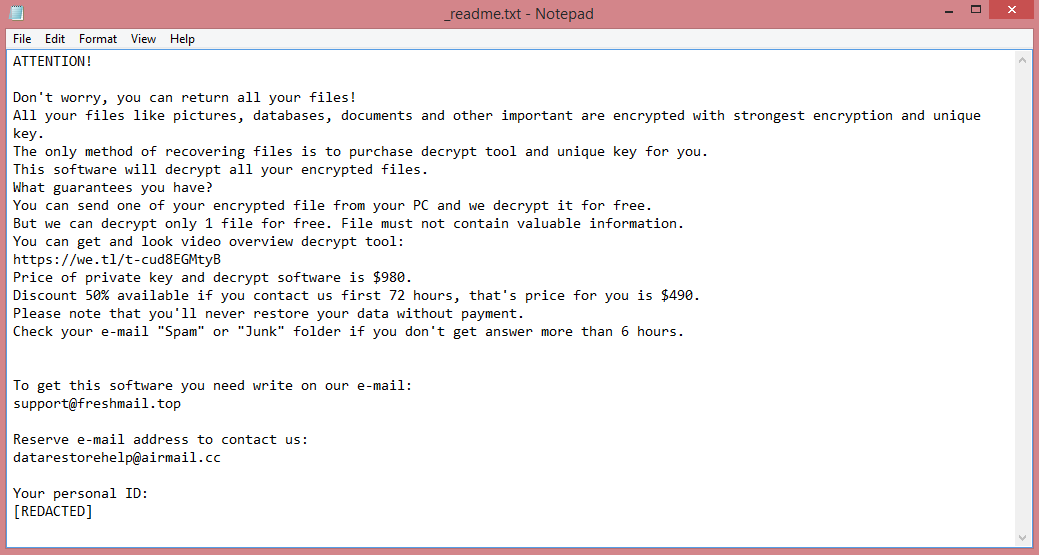
![GOGO ransom note:
All your files have been encrypted!
All your files have been encrypted due to a security problem with your PC. If you want to restore them, write us to the e-mail; gotocompute@tutanota.com
Write this ID in the title of your message : [REDACTED]
In case of no answer in 24 hours write us to theese e-mails: gotoremote@onionmail.org
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us. After payment we will send you the decryption tool that will decrypt all your files.
Free decryption as guarantee
Before paying you can send us up to 1 file for free decryption. The total size of files must be less than 1Mb (non archived), and files should not contain valuable information. (databases,backups, large excel sheets, etc.)
How to obtain Bitcoins
The easiest way to buy bitcoins is LocalBitcoins site. You have to register, click 'Buy bitcoins', and select the seller by payment method and price.
https://localbitcoins.com/buy_bitcoins
Also you can find other places to buy Bitcoins and beginners guide here:
http://www.coindesk.com/information/how-can-i-buy-bitcoins/
Attention!
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
This is the end of the note. Below you will find a guide explaining how to remove GOGO ransomware.](https://www.computips.org/wp-content/uploads/2023/01/how-to-remove-gogo-ransomware.png)