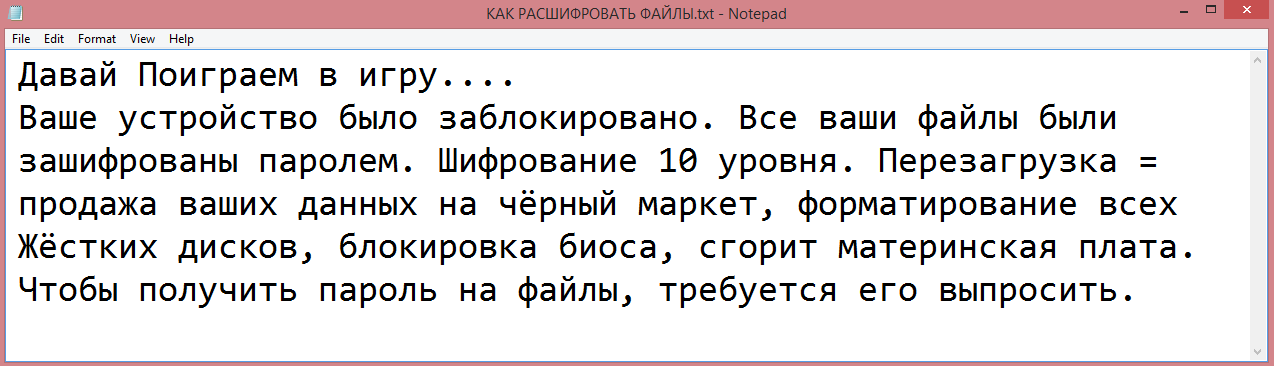
What is Saw ransomware?
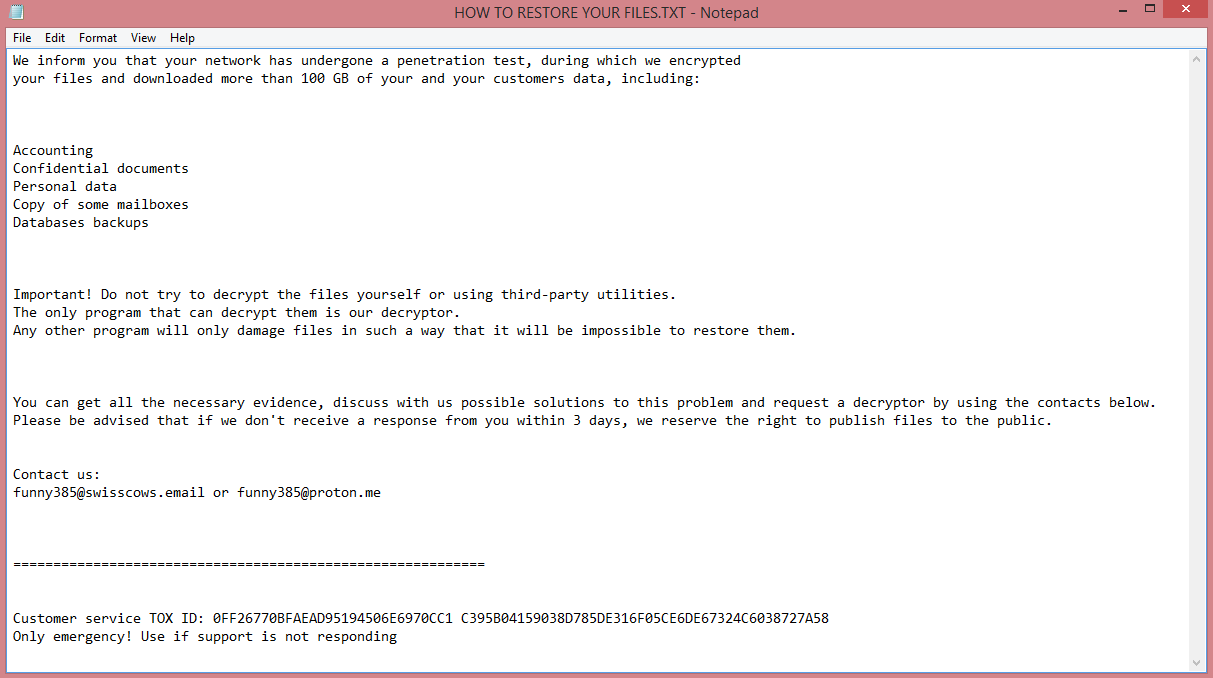
Saw is a recently discovered ransomware program. It encrypts the files on the victim’s computer and gives them .saw file extension. The name of the virus is a reference to the Saw movie. This is not speculation on our part; the virus changes the desktop wallpaper to a picture of Jigsaw, a villain in that movie. The ransom note, called “КАК РАСШИФРОВАТЬ ФАЙЛЫ.txt” also contains a reference.
The full text of the note is shown on the image above, but, chances are, you cannot read it. That is because the note is written in Russian. Please note that this note may not look the same on your computer due to an encoding issue.
Either way, we have translated the note for you so you can read what it says.
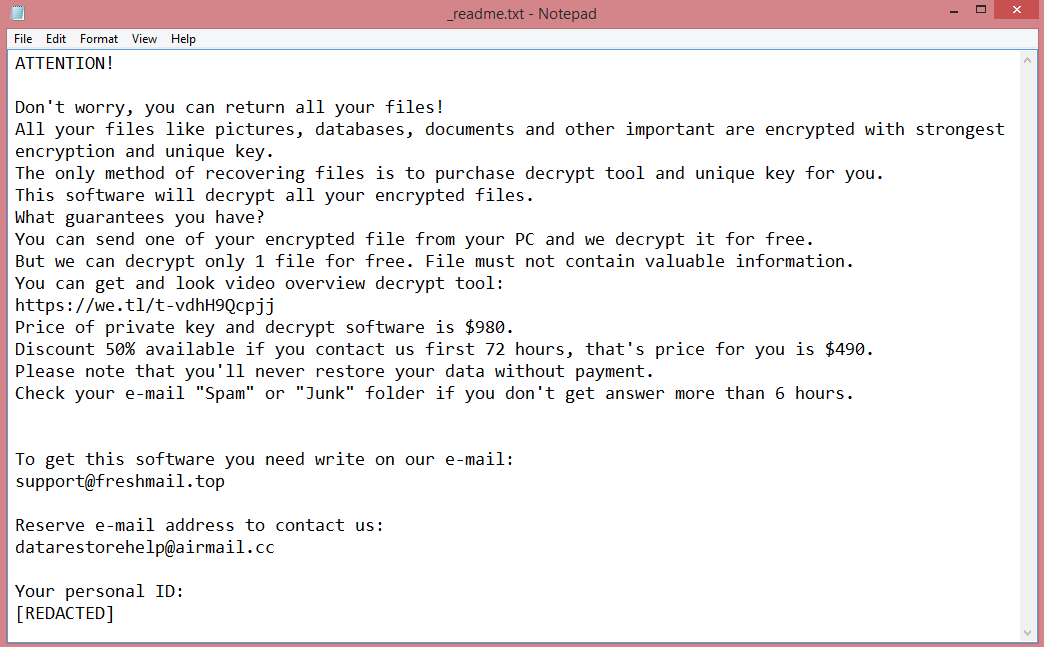
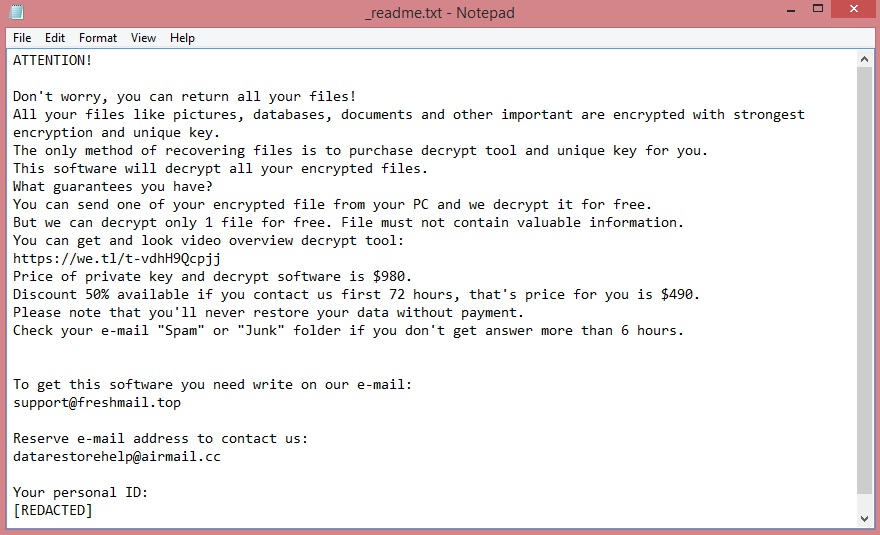
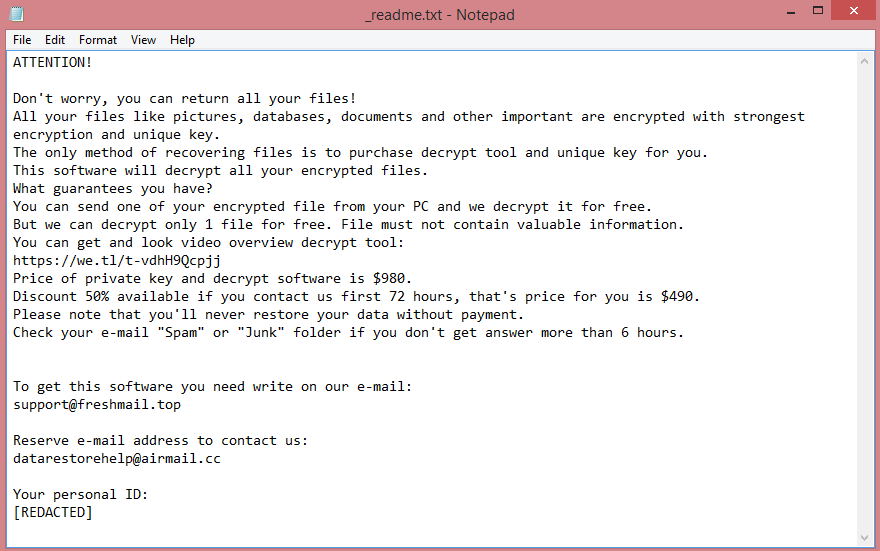
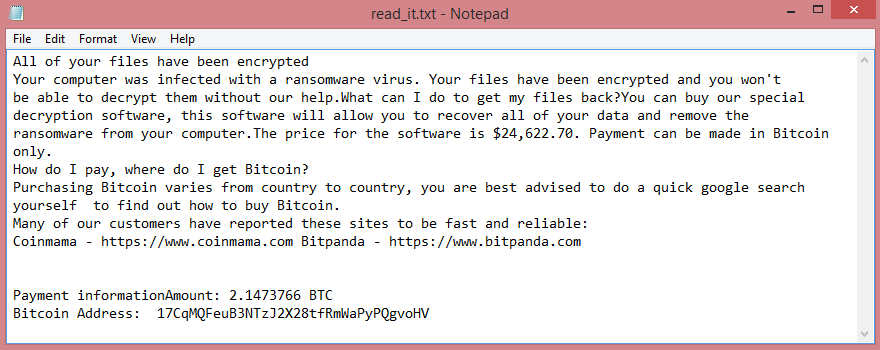
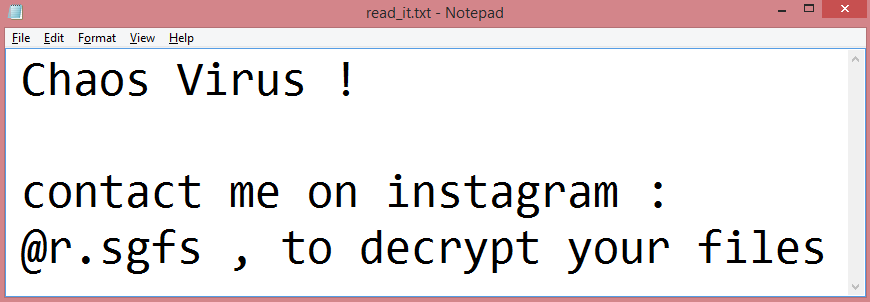
![ScareCrow ransom note:
ScareCrow encrypted your files!
To restore contact us in telegram(desktop.telegram.org):
@ScareCrowRestore1
@ScareCrowRestore2
@ScareCrowRestore3
Your ID: [REDACTED]
This is the end of the note. Below you will find a guide explaining how to remove ScareCrow ransomware.](https://www.computips.org/wp-content/uploads/2023/02/how-to-remove-scarecrow-ransomware.png)