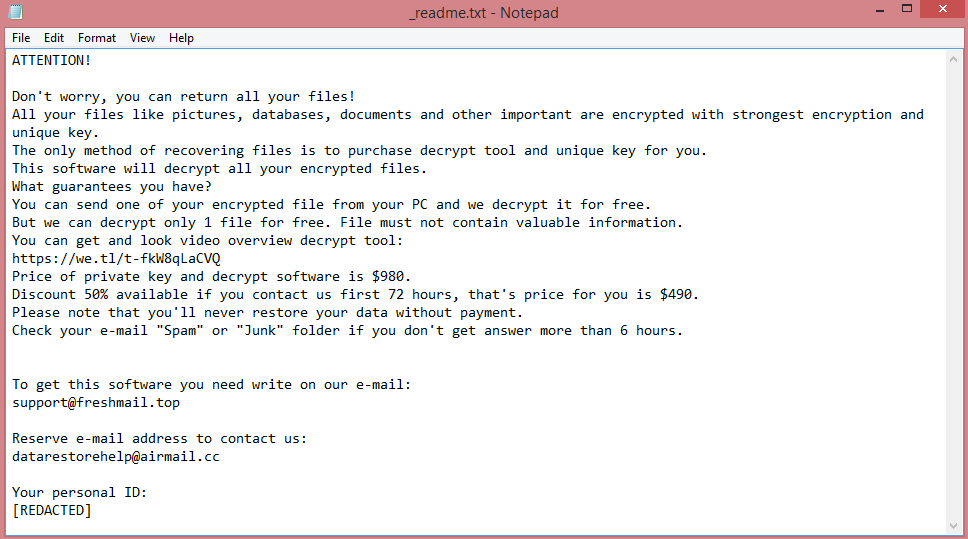
What is Jywd ransomware?
Jywd is a malicious program that infects computers via hacked websites, phishing links, shady e-mail attachments, and other channels. This program is classified as ransomware, a category of viruses that encrypt data on the victim’s computer and demand money for its decryption.
Jywd belongs to the STOP/Djvu ransomware family; all viruses in this family are made from the same template, and are very similar to one another as a result. For example, all of them give encrypted files a new four-letter extension. This virus gives them .jywd file extension, and was named after it. STOP/Djvu viruses also have the same ransom note and the same demands.
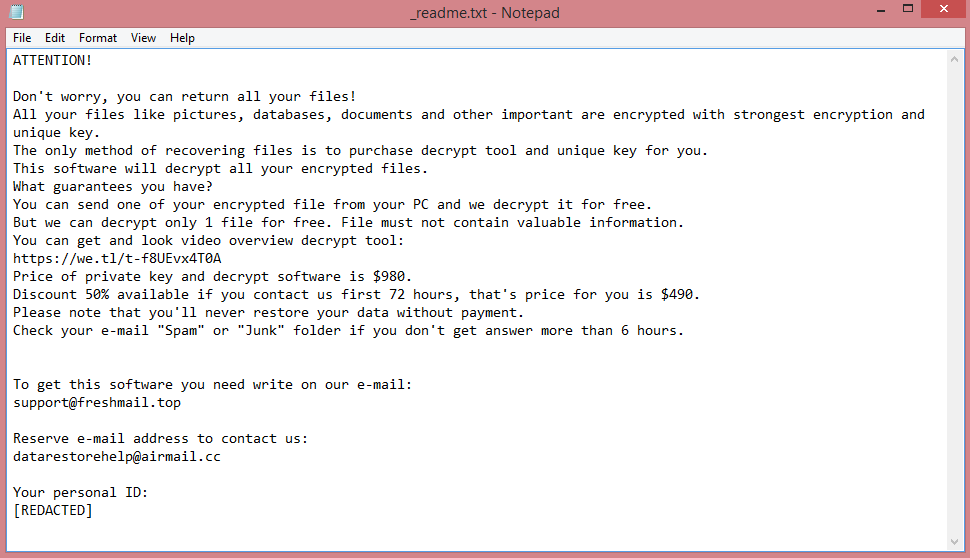
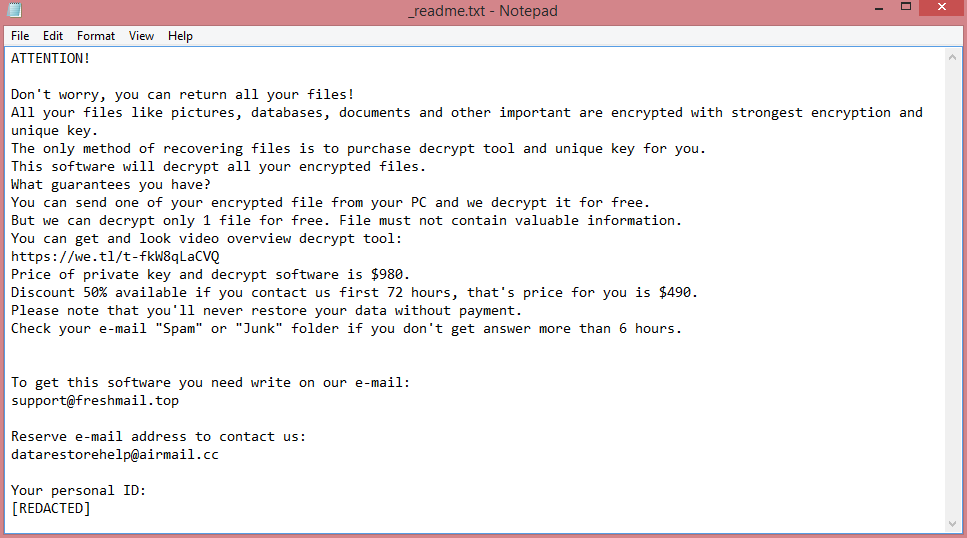
The note in question is called “_readme.txt”. You can read its text on the image above. However, reading the entirety of the note is unnecessary, since the demands can be easily summarized. The hackers want 980 US dollars in ransom, though victims that contact them quickly (within three days of infection) are given a 50% discount.
But $490 is still a lot of money, and the hackers might not even decrypt your files after payment (this happens quite often). This is why we advise you to follow our guide instead. It will explain how to remove Jywd ransomware and decrypt .jywd files without paying the criminals.