Claim Taiko Token is a type of cryptocurrency token that is often seen appearing in web browsers. It is a form of digital currency that can be earned by completing various online tasks or activities. Claim Taiko Token is typically used as a reward for users who engage with certain websites or applications, and can be exchanged for other cryptocurrencies or fiat currency.
Category: Removal Guides
Articles on malware and ways to remove it.
How to remove Access To This Apple Device Has Been Blocked pop-ups
Access To This Apple Device Has Been Blocked is a common error message that appears in browsers when there is an issue with accessing a particular Apple device. This error can occur for a variety of reasons, such as a security restriction, network connectivity issues, or a problem with the device itself. When this message appears, it typically means that the user is unable to access the device or its contents until the issue is resolved.
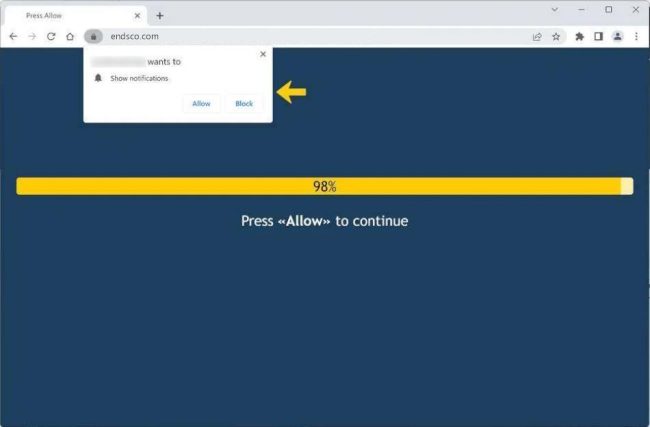
How to remove Endsco.com
Endsco.com is a malicious website that infects computers by exploiting vulnerabilities in popular web browsers. When a user visits the site, it can install malware onto their device without their knowledge or consent. This malware can then take control of the user's browser and display intrusive pop-up notifications, redirecting them to potentially harmful websites or prompting them to download more malware.
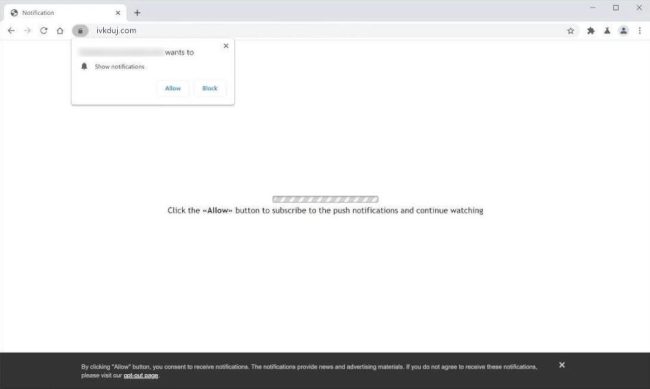
How to remove Ivkduj.com
Ivkduj.com is a malicious website that infects computers by tricking users into allowing browser notifications. When a user visits the website, they may be prompted to click on a button or link to enable notifications. Once the notifications are enabled, Ivkduj.com can push unwanted ads, pop-ups, and notifications to the user's browser, causing a disruptive and potentially harmful browsing experience.
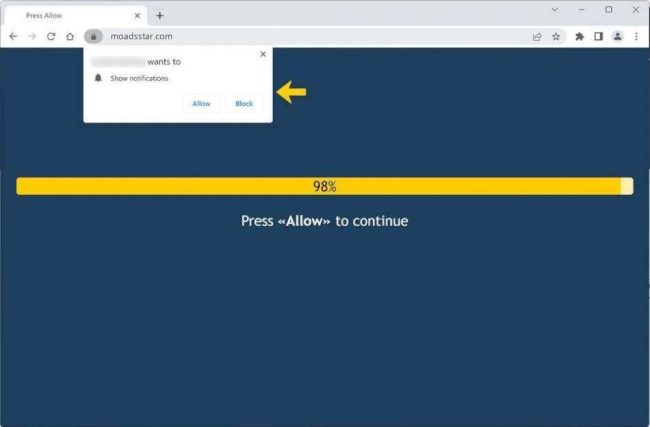
How to remove Moadsstar.com
Moadsstar.com is a malicious website that infects computers and devices by tricking users into allowing browser notifications. This type of malware typically spreads through deceptive practices, such as enticing users with fake offers or clickbait content. Once a user grants permission for notifications, Moadsstar.com can bombard them with unwanted pop-ups and advertisements, leading to a frustrating browsing experience.
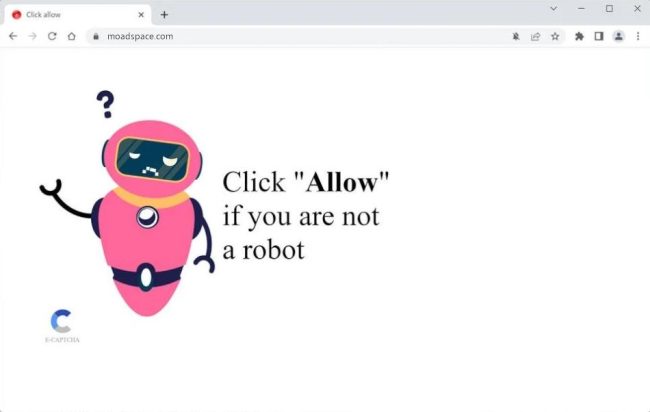
How to remove Moadspace.com
Moadspace.com is a malicious website that is known for infecting computers and exploiting browser notifications. When users visit this website, they may unknowingly download malware onto their devices. This malware can then spread throughout the system, causing various issues such as slow performance, pop-up ads, and even data theft.
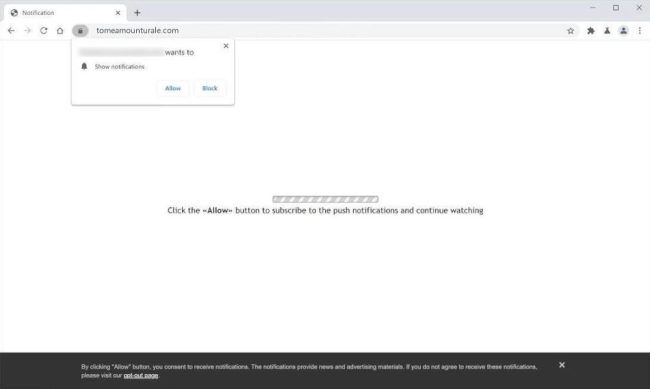
How to remove Tomeamounturale.com
Tomeamounturale.com is a malicious website that infects computers through drive-by downloads and social engineering tactics. Users may unknowingly visit the site through malicious links or advertisements, which then prompts the download of malware onto their devices. Once installed, the malware can gather sensitive information, track user activity, and even take control of the infected computer.
How to remove KoiStealer
KoiStealer is a type of malware that is designed to steal sensitive information from infected computers. It is often used by cybercriminals to steal login credentials, financial information, and other valuable data. KoiStealer can infect computers through various methods, such as malicious email attachments, compromised websites, or software vulnerabilities.
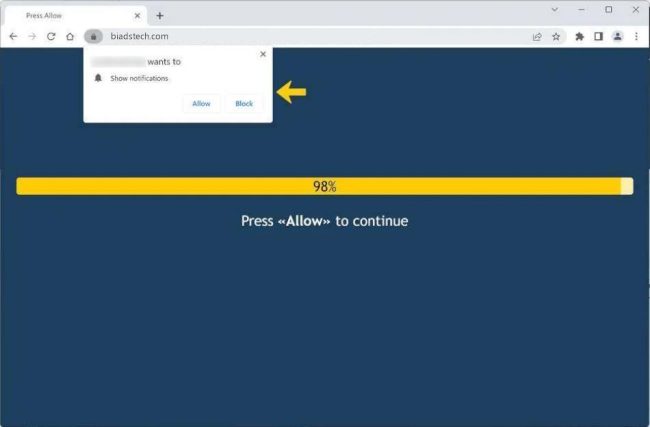
How to remove Biadstech.com
Biadstech.com is a malicious website that infects computers through various means, such as deceptive ads, fake software updates, or bundled with other software. Once a user visits the website, Biadstech.com may prompt the user to allow notifications in their web browser. If the user agrees, Biadstech.com can then exploit these browser notifications to display unwanted advertisements, redirect the user to other malicious websites, or even install malware on the infected device.
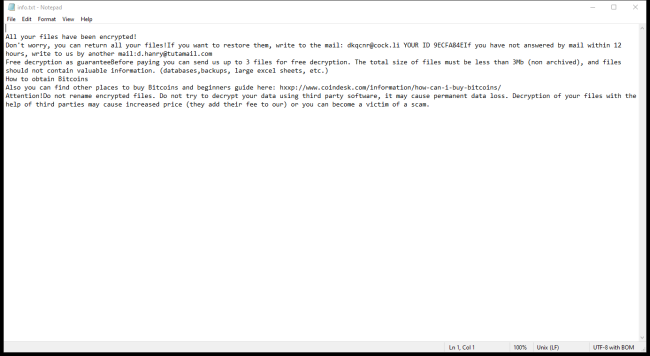
How to remove Dkq Ransomware and decrypt .dkq files
Dkq Ransomware is a malicious software that infects computers by encrypting files and demanding a ransom for their decryption. This ransomware typically spreads through phishing emails, malicious attachments, or compromised websites. Once a computer is infected, Dkq Ransomware adds a specific file extension to the encrypted files, making them inaccessible to the user.