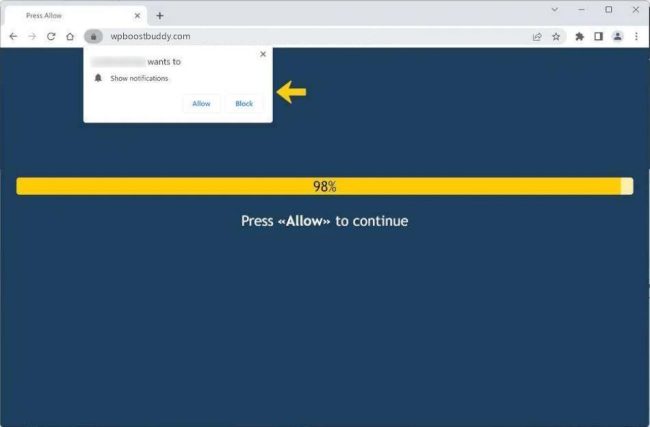
Wpboostbuddy.com is a malicious website that infects computers by exploiting vulnerabilities in web browsers. It typically spreads through deceptive pop-up ads or bundled software downloads. Once a user visits the site, the malicious code is executed, allowing the website to gain access to the user's system.
Category: Adware
Articles about removing adware: browser extensions generating ads, pop-ups and banners.
How to remove Udesmail.com
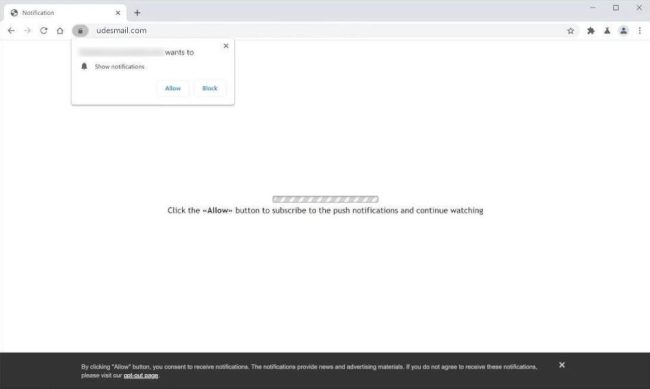
Udesmail.com is a malicious website that is known for infecting computers and exploiting browser notifications. This website typically tricks users into allowing push notifications by displaying misleading messages or offers. Once the notifications are enabled, users start receiving a barrage of unwanted ads, pop-ups, and notifications, which can be very frustrating and disruptive to the user's browsing experience.
How to remove Bectrocks.com
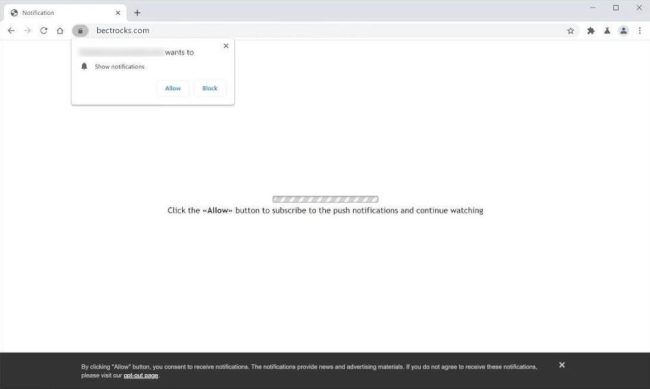
Bectrocks.com is a malicious website that infects computers by tricking users into allowing browser notifications. These notifications are then used to bombard the user with intrusive ads, pop-ups, and other potentially harmful content. The website typically prompts users to click on a button or link, claiming it is necessary to access a certain page or feature, but in reality, it is a tactic to gain permission to send notifications.
How to remove ProtocolView (Mac)
ProtocolView is a potentially unwanted program (PUP) that infects Mac computers by installing itself without the user's permission. It typically enters a system through software bundles or deceptive download links, often disguised as legitimate programs. Once installed, ProtocolView will display intrusive pop-up ads, redirect web browsers to sponsored websites, and track users' online activities to gather personal information.
How to remove Toppholasnow.com
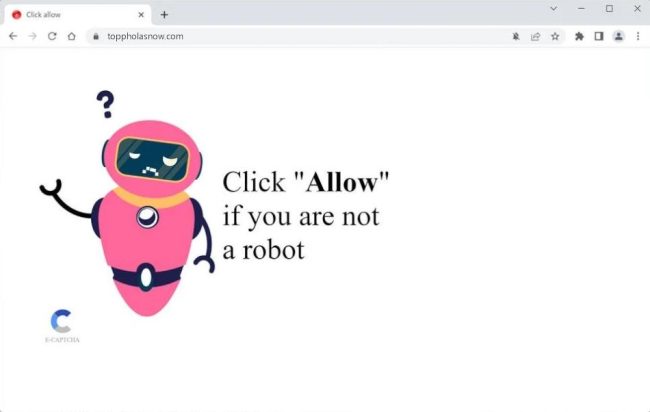
Toppholasnow.com is a malicious website that infects computers by tricking users into allowing browser notifications. Once a user visits the website, they may be prompted to click on a button that claims to be necessary for accessing content or continuing to the next page. By clicking on this button, users unknowingly give permission for the website to display notifications on their browser.
How to remove SourceUpdater (Mac)
SourceUpdater is a type of malware that specifically targets Mac computers. This malicious software infects Mac systems by disguising itself as a legitimate application or software update. Once SourceUpdater infiltrates a Mac, it can cause a variety of issues, including slowing down the system, displaying unwanted pop-up ads, and collecting sensitive information.
How to remove DefaultSection (Mac)
DefaultSection is a type of adware that specifically targets Mac computers. It is designed to bombard users with unwanted and intrusive advertisements, pop-ups, and banners while they browse the internet. DefaultSection can change the default homepage and search engine settings in the user's web browser without their permission, redirecting them to malicious websites and compromising their online security.
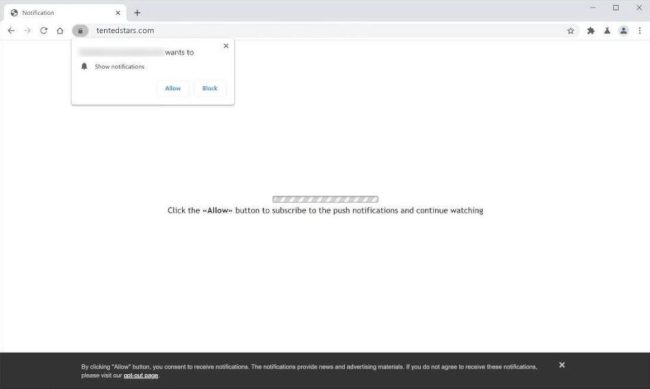
How to remove Tentedstars.com
Tentedstars.com is a malicious website that infects computers through various means such as drive-by downloads, malicious email attachments, or fake software updates. Once a computer becomes infected with Tentedstars.com, it can cause a range of issues including pop-up ads, browser redirects, and even data theft. This website is often used by cybercriminals to generate revenue through ad clicks or by stealing personal information from unsuspecting users.
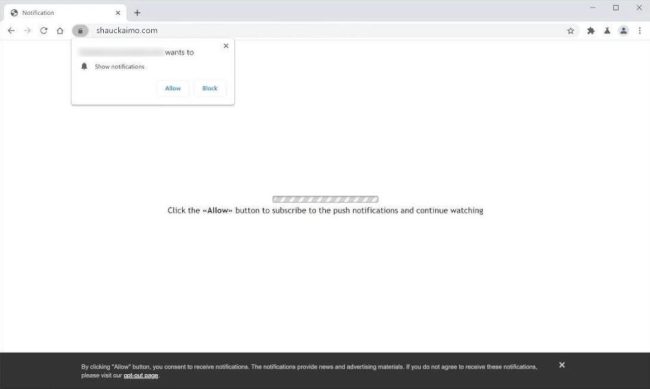
How to remove Shauckaimo.com
Shauckaimo.com is a malicious website that infects computers through various means, such as fake software updates, deceptive advertisements, or by tricking users into clicking on malicious links. Once a computer is infected with Shauckaimo.com, it can cause a range of issues, including slowing down the computer's performance, displaying unwanted pop-up ads, redirecting web searches, and even stealing sensitive information.
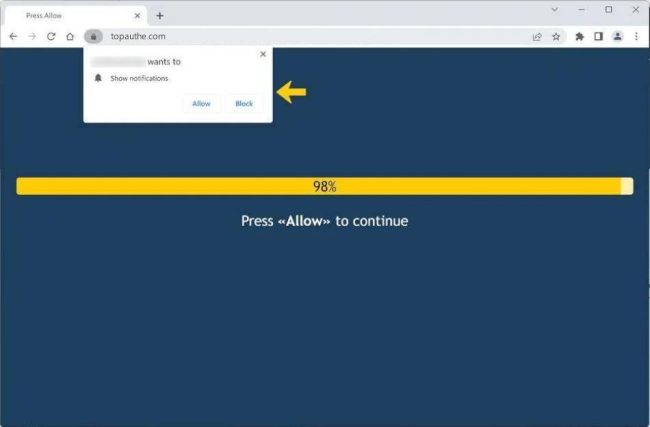
How to remove Topauthe.com
Topauthe.com is a malicious website that infects computers through various means, including malicious software downloads, phishing emails, and drive-by downloads. Once a computer is infected, Topauthe.com can exploit browser notifications to display intrusive pop-ups and advertisements, redirect users to other malicious websites, and collect sensitive information such as browsing history and login credentials.