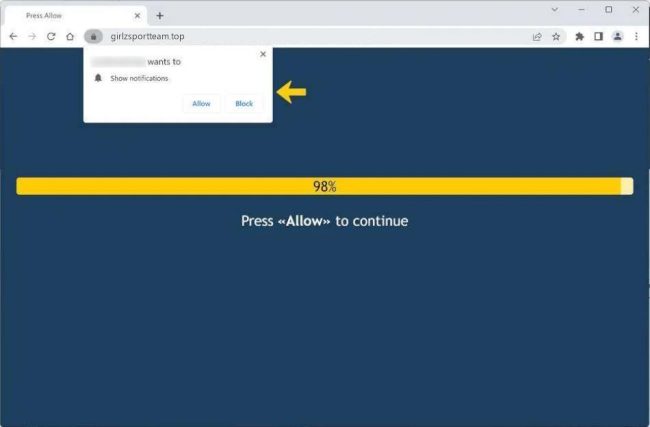
Girlzsportteam.top is a malicious website that infects computers through various deceptive tactics. It typically spreads through misleading online advertisements, software bundling, or malicious email attachments. Once a user visits the website, they may be prompted to allow notifications, which can then lead to a barrage of unwanted pop-up ads and notifications.
Author: Aleksei A
How to remove the fake deBridge website pop-ups
The fake deBridge website is a fraudulent website that mimics the legitimate deBridge website in order to deceive users into providing personal information or downloading malicious software. These fake websites often look very similar to the real website, making it difficult for users to differentiate between the two.
How to stop Wells Fargo – Account Verification Required email scam
Wells Fargo - Account Verification Required email spam is a phishing scam that targets individuals by posing as a legitimate communication from Wells Fargo, a major financial institution. The email typically informs recipients that their account needs verification or updating, and prompts them to click on a link to provide their personal and financial information. This type of phishing campaign is designed to steal sensitive data such as login credentials, credit card numbers, and other personal information.
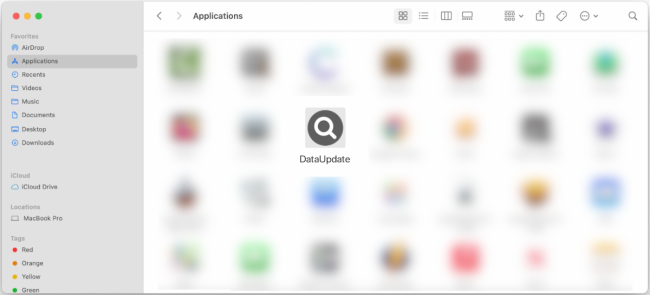
How to remove DataUpdate (Mac)
DataUpdate is a type of malware that infects Mac computers, typically through deceptive methods such as fake software updates or malicious email attachments. Once installed on a Mac system, DataUpdate can access and steal sensitive information, track user activity, and even take control of the computer remotely. This malware can also disrupt the normal functioning of the system, slowing it down and causing crashes.
How to remove RedStone Community Vote pop-ups
RedStone Community Vote is a browser extension that displays pop-up notifications asking users to vote on various community-related topics. These notifications often appear when browsing the internet, and users are prompted to provide their input by clicking on a button or selecting an option. The purpose of RedStone Community Vote is to gather feedback from users on a wide range of subjects, such as product preferences, website design, or even social issues.
How to remove Crude Oil Trade pop-ups
Crude oil trade refers to the buying and selling of crude oil as a commodity in the global market. Crude oil is one of the most valuable resources in the world, as it is used for various purposes such as fuel for vehicles, heating, and manufacturing. The trade of crude oil is a complex process that involves numerous parties, including oil companies, traders, refineries, and governments.
How to stop Request To Cancel Your Services email scam
Request To Cancel Your Services email spam is a type of phishing scam where cybercriminals send fake emails to trick recipients into believing that their services are being canceled. These emails often contain urgent language and instructions for the recipient to click on a link or provide personal information to prevent the cancellation. In reality, clicking on the link or providing personal information can lead to malware infection, identity theft, or financial loss.
How to remove USDT NFT Airdrop pop-ups
USDT NFT Airdrop is a promotional campaign where users are given free USDT (Tether) tokens in the form of non-fungible tokens (NFTs). NFTs are unique digital assets that are stored on the blockchain and cannot be replicated or exchanged for another token. These airdrops are often used by crypto projects to attract new users and create buzz around their platform.
How to remove Xam Ransomware and decrypt .xam files
Xam ransomware is a malicious software that encrypts the files on a victim's computer, making them inaccessible. This ransomware typically infects computers through phishing emails, malicious websites, or software vulnerabilities. Once installed, Xam ransomware adds a ".xam" extension to the encrypted files, making it easy to identify which files have been affected.
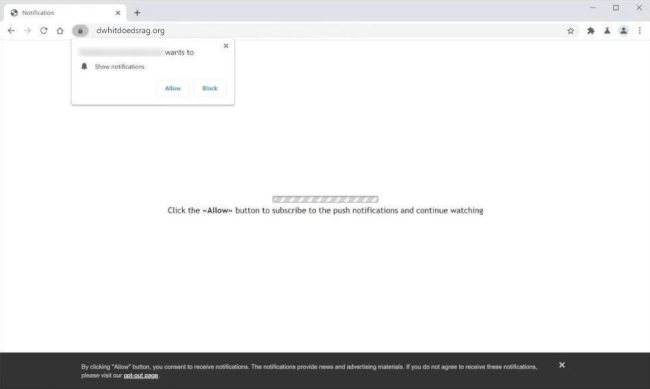
How to remove Dwhitdoedsrag.org
Dwhitdoedsrag.org is a malicious website that infects computers through various means, such as fake software updates, deceptive advertisements, or bundled with freeware. Once a user visits the website, it may prompt them to enable browser notifications, claiming it is necessary to access the content. However, by allowing these notifications, the website gains permission to send intrusive pop-up notifications to the user's desktop, even when the browser is closed.