Search-it-now.com is a notorious adware that targets Mac computers, bombarding users with unwanted advertisements and redirects to dubious websites. This adware infiltrates Mac computers through deceptive techniques such as software bundling, where it is packaged with legitimate software and installed without the user's knowledge. Once installed, Search-it-now.com modifies browser settings and starts displaying intrusive ads in the form of pop-ups, banners, and sponsored links.
Author: Aleksei A
How to stop Citrix Attachments email scam
Citrix Attachments email spam is a type of phishing campaign that aims to trick users into downloading malicious attachments or clicking on harmful links. These emails often appear to be legitimate messages from Citrix, a popular software company known for its virtualization and networking solutions. However, these emails are actually crafted by cybercriminals who use social engineering tactics to deceive recipients into taking actions that can compromise their security.
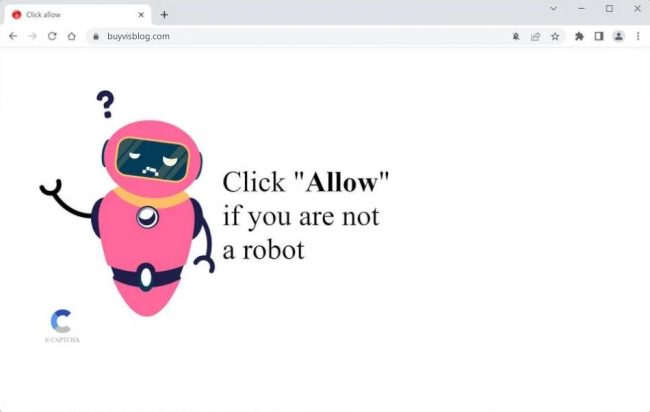
How to remove Buyvisblog.com
Buyvisblog.com is a malicious website that infects computers through various methods, such as drive-by downloads or software bundling. Once a user visits the website, it may execute malicious scripts that can infect the computer with malware or adware. One common tactic used by Buyvisblog.com is to exploit browser notifications, tricking users into allowing notifications that can then be used to display unwanted ads or redirect users to malicious websites.
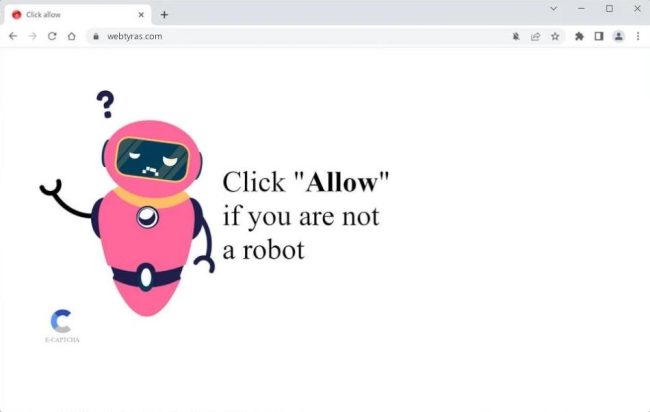
How to remove Webtyras.com
Webtyras.com is a malicious website that infects computers by tricking users into allowing browser notifications. When users visit the website, they are prompted with a notification that claims to be necessary for accessing the site's content. However, by clicking "Allow," users unknowingly grant permission for the website to send them notifications, which can then be used to deliver malicious content or redirect them to other harmful websites.
How to remove Getlloydsonline.com
Getlloydsonline.com is a malicious website that infects computers through various deceptive tactics. It often spreads through malicious ads, software bundles, or by tricking users into clicking on fake download buttons. Once a user visits the website, it may attempt to install malware or unwanted programs onto the computer without the user's consent.
How to remove Lifemnadsnews.com
Lifemnadsnews.com is a malicious website that infects computers by exploiting vulnerabilities in browsers and devices. Once a user visits the website, it can secretly install malware onto the device without the user's knowledge. This malware can then collect sensitive information, track online activities, and even hijack browser notifications.
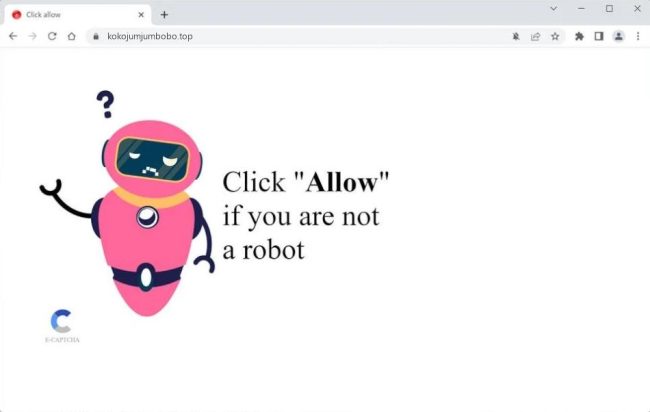
How to remove Kokojumjumbobo.top
Kokojumjumbobo.top is a malicious website that infects computers through deceptive tactics such as redirecting users to its page or tricking them into allowing browser notifications. Once a user visits the site, they may be prompted to click on a button to continue to the next page or to view content. By clicking on these prompts, users unknowingly give the site permission to send browser notifications to their device.
How to remove Globalwoldsinc.com
GlobalWoldsinc.com is a malicious website that infects computers by tricking users into allowing browser notifications. Once a user visits the website, they are prompted to click on a button to enable notifications in order to access content or continue browsing. By clicking on this button, users unknowingly give permission for the website to send them notifications, which can be used to display spammy ads, redirect users to other malicious websites, or even install malware on their devices.
How to remove Puabundler:Win32/Cheatengine
Puabundler:Win32/Cheatengine is a potentially unwanted application (PUA) that is classified as a bundler and is known for bundling other software with it during installation. This bundler is often used to distribute cheat engine software, which is used to modify video games to gain an unfair advantage. While cheat engines themselves are not always malicious, the bundler that comes with Puabundler:Win32/Cheatengine can lead to the installation of unwanted programs and can compromise the security of a computer.
How to remove Trojan:Bat/Alien.Rpa!Mtb
Trojan:Bat/Alien.Rpa!Mtb is a type of malicious software, commonly known as a Trojan horse, that is designed to infiltrate and compromise a computer system's security. This particular Trojan is known for its ability to disguise itself as a legitimate program or file in order to trick users into downloading and executing it on their systems. Once installed, Trojan:Bat/Alien.Rpa!Mtb can perform a variety of harmful activities, such as stealing sensitive information, disrupting system processes, and even allowing remote access to cybercriminals.