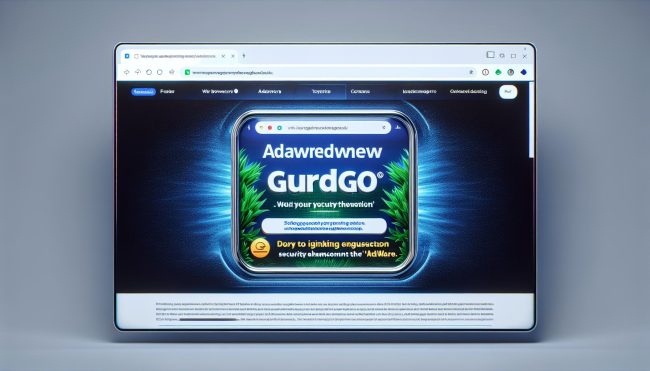
GuardGo adware is a type of malicious software that displays unwanted advertisements on a user's computer. These ads can be very intrusive and annoying, often popping up at random times and disrupting the user's browsing experience. GuardGo adware is typically installed on a computer without the user's knowledge or consent, and it can be difficult to remove.
Author: Aleksei A
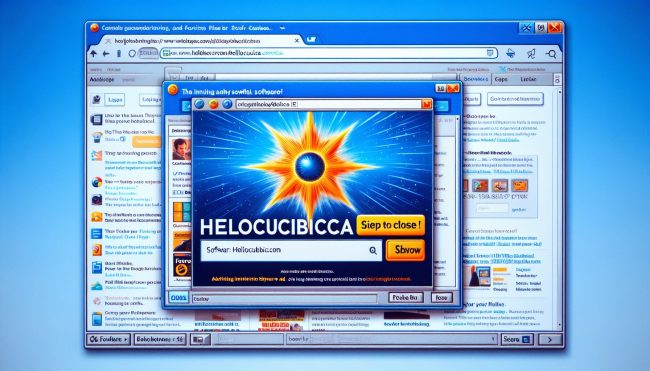
How to remove HelioCubica
HelioCubica is a type of adware that infects computers by displaying unwanted advertisements and pop-ups to users. This malicious software is designed to generate revenue for its creators by displaying targeted ads based on the user's browsing habits and preferences. HelioCubica can infiltrate a computer through various methods, such as downloading infected files or software, clicking on malicious links, or visiting compromised websites.
How to remove AnciPyror
AnciPyror adware is a type of malicious software that infiltrates computers and bombards users with unwanted and intrusive advertisements. This adware typically gets installed on a computer without the user's knowledge or consent, often bundled with free software downloads or through malicious websites. Once installed, AnciPyror collects information about the user's browsing habits and displays targeted ads based on this data.
How to stop American Express Card Deactivation email scam
American Express Card Deactivation email spam is a common phishing scam that targets American Express cardholders. These fraudulent emails often claim that the recipient's American Express card has been deactivated or suspended due to suspicious activity or security concerns. The email will typically prompt the recipient to click on a link or provide personal information, such as account numbers or passwords, in order to reactivate their card. However, clicking on these links or providing sensitive information can lead to identity theft, financial fraud, and unauthorized access to personal accounts.
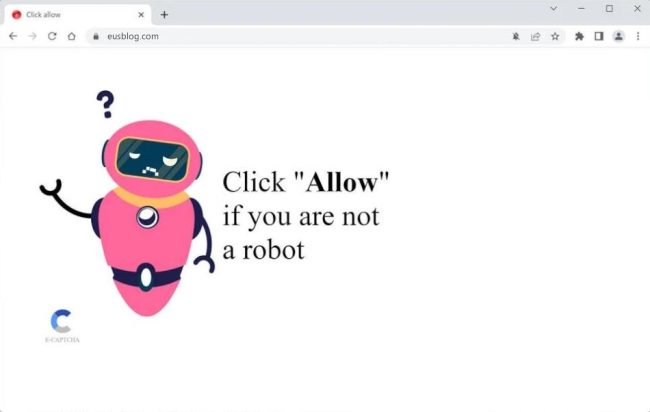
How to remove Eusblog.com
Eusblog.com is a malicious website that infects computers through various methods, including drive-by downloads and malicious scripts. Once a user visits the website, it may automatically download and install malware onto their device without their knowledge or consent. This malware can then steal sensitive information, track browsing habits, and even take control of the infected device.
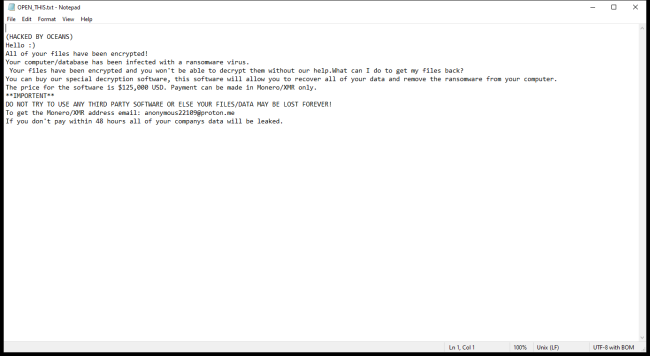
How to remove OCEANS Ransomware and decrypt random files
OCEANS Ransomware is a type of malicious software that encrypts files on infected computers and demands a ransom in exchange for the decryption key. It typically infects computers through phishing emails, malicious downloads, or exploiting vulnerabilities in software. Once a computer is infected, OCEANS Ransomware encrypts files by adding specific file extensions such as .oceans or .locked to them, making them inaccessible to the user.
How to remove Wonderstab.com
Wonderstab.com is a type of adware that infects computers and web browsers by displaying intrusive and unwanted advertisements. This malware typically infiltrates a user's system through deceptive tactics, such as bundling itself with other software downloads or posing as a legitimate program. Once installed, Wonderstab.com generates pop-up ads, banners, and other forms of advertising that can disrupt the user's browsing experience and compromise their online security.
How to remove Veza Ransomware and decrypt .veza files
Veza Ransomware is a type of malware that infects computers through deceptive email attachments, malicious websites, or software downloads. Once it infiltrates a system, Veza Ransomware encrypts the files on the computer, making them inaccessible to the user. It adds the .veza file extension to the encrypted files, indicating that they have been compromised. The ransomware uses a sophisticated encryption algorithm to lock the files, making it extremely difficult to decrypt them without the decryption key.
How to remove EDHST Ransomware and decrypt .edhst files
EDHST ransomware is a malicious software that encrypts files on the infected computer, making them inaccessible to the user. It typically infiltrates computers through phishing emails, malicious websites, or software vulnerabilities. Once the ransomware is activated, it adds the .edhst file extension to encrypted files, such as photos, documents, and videos, rendering them unreadable. EDHST ransomware uses a strong encryption algorithm to lock the files, making it nearly impossible to decrypt without the decryption key.
How to remove OPIX Ransomware and decrypt random files
OPIX Ransomware is a malicious software that encrypts files on a victim's computer and demands a ransom in exchange for decrypting them. This type of ransomware typically infects computers through phishing emails, malicious attachments, or by exploiting vulnerabilities in outdated software. Once infected, OPIX Ransomware adds specific file extensions to encrypted files, making them inaccessible to the user.