TechRangeSearch is a type of adware that infects computers and displays unwanted advertisements and pop-ups to users. This adware is typically installed on a computer without the user's knowledge or consent, often bundled with other software downloads or through malicious websites. Once installed, TechRangeSearch tracks the user's browsing activity and collects data on their online behavior in order to display targeted ads.
Author: Aleksei A
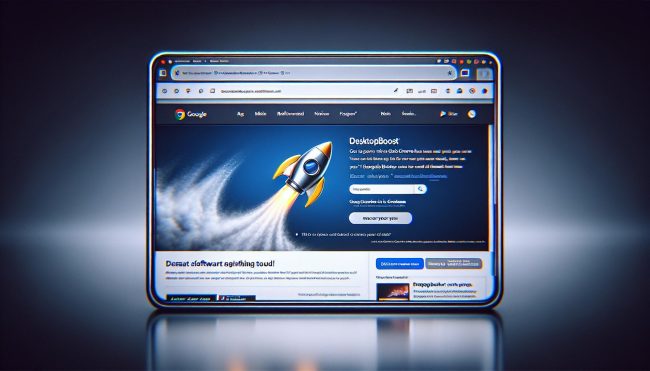
How to remove DesktopBoost
DesktopBoost is a type of adware that infiltrates computers and bombards users with unwanted advertisements. This adware typically enters a computer through free software downloads, deceptive advertisements, or malicious websites. Once installed, DesktopBoost will display pop-up ads, banners, and in-text advertisements on the user's desktop, browser, or within other applications.
How to remove Guardian Angel
Guardian Angel is a type of adware that infects computers through deceptive means, often by bundling itself with other software programs or by disguising itself as a legitimate application. Once installed on a computer, Guardian Angel displays unwanted advertisements in the form of pop-ups, banners, and sponsored links. These ads can be intrusive and disruptive to the user's browsing experience, and may also lead to security risks if clicked on.
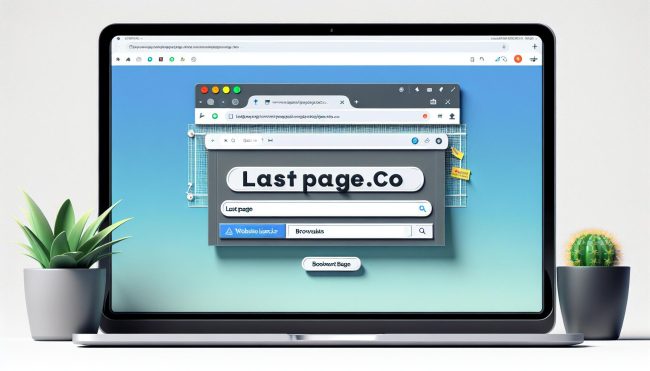
How to remove Last-page.co
Last-page.co adware is a type of malicious software that is designed to display unwanted advertisements on a user's computer or web browser. This adware can be very intrusive and disruptive, as it can cause pop-up ads to appear frequently while browsing the internet. In addition to being annoying, Last-page.co adware can also pose a security risk, as it may track a user's browsing habits and collect personal information.
How to remove $PunkAI Airdrop Registration pop-ups
$PunkAI Airdrop Registration is a form that appears in web browsers, prompting users to sign up for an airdrop of a cryptocurrency called $PunkAI. Airdrops are a marketing tactic used by cryptocurrency projects to distribute tokens to a wide audience in order to increase awareness and adoption of their coin.
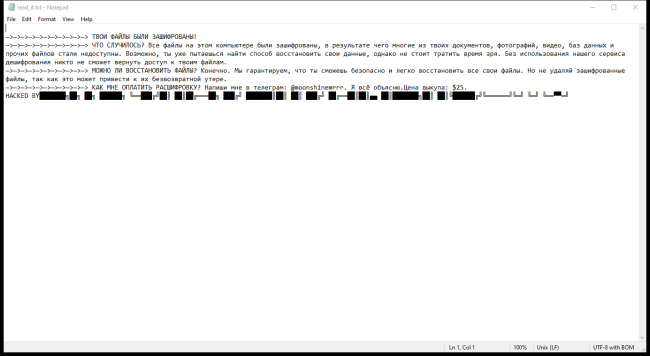
How to remove ZHO Ransomware and decrypt random files
ZHO Ransomware is a type of malicious software that encrypts files on a victim's computer, rendering them inaccessible. It typically infects computers through phishing emails, malicious downloads, or exploiting vulnerabilities in software. Once a computer is infected, ZHO Ransomware adds a specific file extension to encrypted files, making them easily identifiable. The ransomware uses advanced encryption algorithms to lock the files, making it nearly impossible to decrypt them without the decryption key.
How to remove Web-organize.co
Web-organize.co is a type of adware that infiltrates computers and web browsers to display unwanted advertisements and pop-ups. This adware is designed to generate revenue for its creators by redirecting users to sponsored websites and displaying various ads. Users may encounter Web-organize.co adware when downloading freeware or shareware programs from untrustworthy sources, as it is often bundled with software installers.
How to remove Bitget Wallet (BWB) Airdrop pop-ups
Bitget Wallet (BWB) Airdrop is a promotional campaign that aims to distribute free BWB tokens to users as a way to attract more people to use the Bitget Wallet platform. Airdrops are a common marketing strategy in the cryptocurrency industry where companies give away tokens or coins for free to create awareness and encourage adoption of their platform. By participating in the BWB Airdrop, users can receive a certain amount of BWB tokens without having to make any financial investment.
How to remove Guardian Angel
Guardian Angel adware is a type of malicious software that infiltrates computers and web browsers in order to display unwanted advertisements and collect user data without their consent. This adware often disguises itself as a legitimate program or browser extension, making it difficult for users to detect and remove.
How to stop Unapproved Emails email scam
Unapproved Emails email spam refers to unsolicited emails that are sent to individuals without their consent, usually for the purpose of promoting products or services. These emails often contain misleading information and may contain malicious links or attachments that can infect a computer with malware. Unapproved Emails spam campaigns are typically sent out in bulk to a large number of email addresses, with the hope that some recipients will click on the links or download the attachments.