CharacterRecord is a type of malware that specifically targets Mac users. This malicious software is designed to infiltrate Mac systems and steal sensitive information, such as usernames, passwords, and financial data. CharacterRecord can infect Mac devices through various means, including phishing emails, malicious websites, and fake software downloads.
Author: Aleksei A
How to remove News-guyete.cc
News-guyete.cc is a malicious website that infects computers through deceptive tactics and exploits browser notifications. Users may encounter this website when browsing the internet, often being redirected to it through pop-up ads or malicious links. Once on the website, users are prompted to allow notifications in order to access content, but in reality, this is a ploy to infect their device with malware.
How to stop Commercial Invoice email scam
Commercial Invoice email spam is a type of phishing scam where cybercriminals send fraudulent emails to individuals or businesses, pretending to be legitimate invoices from reputable companies. The emails typically contain a request for payment or personal information, and may appear convincing with official logos and company information. However, these emails are designed to trick recipients into clicking on malicious links or attachments, leading to malware infections or financial loss.
How to remove Stream-it.top
Stream-it.top is a malicious website that infects computers through deceptive tactics such as fake software updates or misleading advertisements. Once a user visits the site, Stream-it.top prompts them to enable browser notifications in order to access content. By doing so, the site gains the ability to display intrusive pop-up notifications even when the browser is closed.
How to remove AccessibilityUnit (Mac)
AccessibilityUnit is a type of malware that specifically targets Mac computers. This malicious software can infect a system through various means, such as downloading infected files or visiting compromised websites. Once installed on a Mac, AccessibilityUnit can cause significant harm by stealing personal information, monitoring online activities, and even taking control of the infected device.
How to remove ElementBuffer (Mac)
ElementBuffer is a type of malware that specifically targets Mac computers. It is designed to infect and compromise the security of these devices, allowing cybercriminals to gain unauthorized access to personal information and sensitive data. ElementBuffer typically spreads through malicious websites, email attachments, or software downloads, tricking users into unwittingly installing the malware on their systems.
How to remove News-doyogi.com
News-doyogi.com is a malicious website that infects computers through deceptive tactics such as fake software updates or free downloads. Once a user visits the site, it prompts them to allow notifications from the website. If the user agrees, News-doyogi.com can then bombard the user with unwanted advertisements and pop-ups, leading to a compromised browsing experience.
How to remove News-hupali.com
News-hupali.com is a malicious website that is known for infecting computers and exploiting browser notifications. This website typically lures users in with enticing headlines or fake news stories, prompting them to click on a link that redirects them to the site. Once on News-hupali.com, users may be prompted to allow notifications from the site, which can then be used to bombard them with unwanted pop-ups and advertisements.
How to remove HardDriveThread (Mac)
HardDriveThread is a type of malware that specifically targets Mac operating systems. This malicious software is designed to infiltrate a user's computer system and gain unauthorized access to sensitive information such as personal data, financial records, and login credentials. Once infected, HardDriveThread can cause severe damage to the system, including slowing down performance, corrupting files, and potentially stealing valuable information.
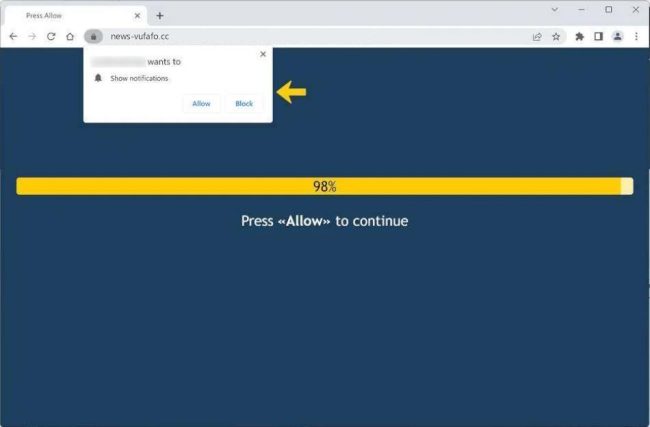
How to remove News-vufafo.cc
News-vufafo.cc is a malicious website that infects computers through deceptive tactics such as pop-up notifications and browser redirects. When users visit the site, they may be prompted to allow notifications in order to access content or download files. However, once permission is granted, the site can bombard the user with unwanted notifications, advertisements, and potentially harmful links.