What is RONALDIHNO ENCRYPTER ransomware / r7 ransomware?
RONALDIHNO ENCRYPTER ransomware, also known as r7 ransomware, is a harmful program that encrypts all files on computers it infects. This is not done simply out of desire to cause harm, however. The hackers behind this are motivated by financial gain. Encrypted files are completely inaccessible; they cannot be viewed or modified in any way. But this encryption process is reversible. With the right cryptographic key, essentially a password, these files can be decrypted and made accessible again. The hackers offer to do this, and usually charge quite a lot for their “services”.
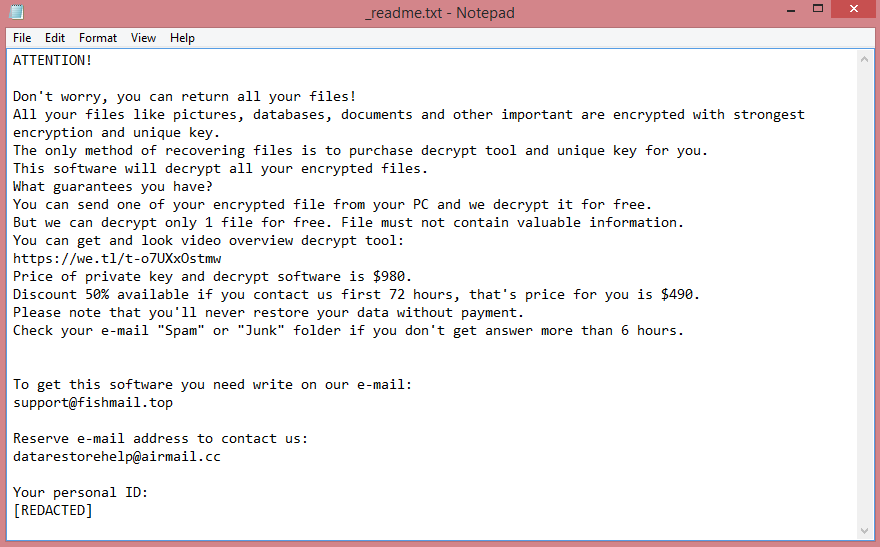
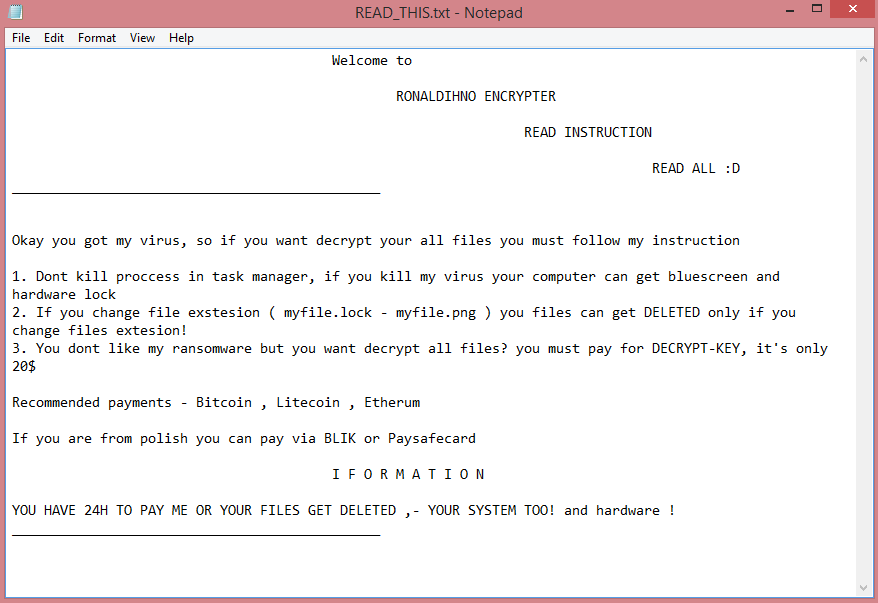
RONALDIHNO ENCRYPTER doesn’t simply encrypt files; it also renames them. All files affected by the virus receive .r7 file extension. For example, “video.mp4” would be renamed to “video.mp4.r7”. Its ransom note, meanwhile, is called “READ_THIS.txt”. You can read the full text of the note on the image above, but here’s the summary.
The hacker demands only $20 for decryption. This is exceptionally low; usually, the criminals demand hundreds and even thousands of dollars. The note lacks any contact information, but the virus also changes desktop wallpaper to a second note, which mentions the e-mail (dupex876@gmail.com).
Though the hacker doesn’t ask for much, you might still want to avoid paying for two reasons. First, you have no guarantee that you will get your files back. Second, if you pay, you may become a target of further virus attacks in the future. For this reason, we’ve prepared a guide that will explain how to remove RONALDIHNO ENCRYPTER ransomware and decrypt .r7 files without contacting the criminal.
![CMLOCKER ransom note:
Oops All Of your important files were encrypted Like document pictures videos etc..
Don't worry, you can return all your files!
All your files, documents, photos, databases and other important files are encrypted by a strong encryption.
How to recover files?
RSA is a asymmetric cryptographic algorithm, you need one key for encryption and one key for decryption so you need private key to recover your files. It’s not possible to recover your files without private key.
The only method of recovering files is to purchase an unique private key.Only we can give you this key and only we can recover your files.
What guarantees you have?
As evidence, you can send us 1 file to decrypt by email We will send you a recovery file Prove that we can decrypt your file
Please You must follow these steps carefully to decrypt your files:
Send $980 worth of bitcoin to wallet: bc1qzpa3j6qse5xfxft2xy7h2phq04wq9pk66lllz5
after payment,we will send you Decryptor software
contact email: leljicok@gmail.com
Your personal ID: [REDACTED]
This is the end of the note. Below you will find a guide explaining how to remove CMLOCKER ransomware.](https://www.computips.org/wp-content/uploads/2022/10/how-to-remove-cmlocker-ransomware.png)
![ESCANOR ransom note:
Oops All Of your important files were encrypted Like document pictures videos etc..
Don't worry, you can return all your files!
All your files, documents, photos, databases and other important files are encrypted by a strong encryption.
How to recover files?
RSA is a asymmetric cryptographic algorithm, you need one key for encryption and one key for decryption so you need private key to recover your files. It’s not possible to recover your files without private key.
The only method of recovering files is to purchase an unique private key.Only we can give you this key and only we can recover your files.
What guarantees you have?
As evidence, you can send us 1 file to decrypt by email We will send you a recovery file Prove that we can decrypt your file
Please You must follow these steps carefully to decrypt your files:
Send $980 worth of bitcoin to wallet: js97xc025fwviwhdg53gla97xc025fwv
after payment,we will send you Decryptor software
contact email: http://www.escanor-re.com/
Your personal ID: [REDACTED]
This is the end of the note. Below you will find a guide explaining how to remove ESCANOR ransomware.](https://www.computips.org/wp-content/uploads/2022/10/how-to-remove-escanor-ransomware.png)