What is Yguekcbe ransomware?
Yguekcbe ransomware is a malware program (a virus) that is designed to make money in a very specific way. First, it encrypts all files on the target computer using a cryptographic algorithm. This process renders the files inaccessible, but it is reversible. The virus then offers to do just that, to decrypt the files; that, however, would cost victim money. These viruses are called ransomware because this process essentially holds the files for ransom.
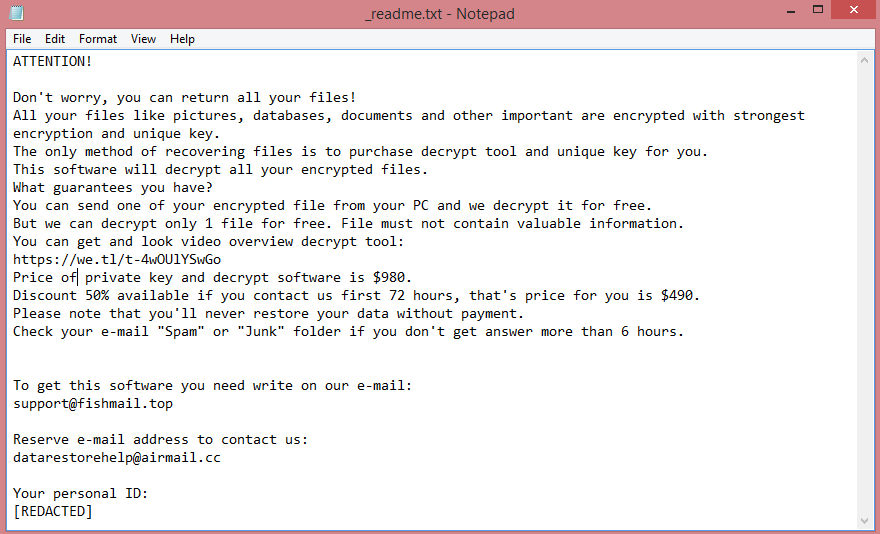
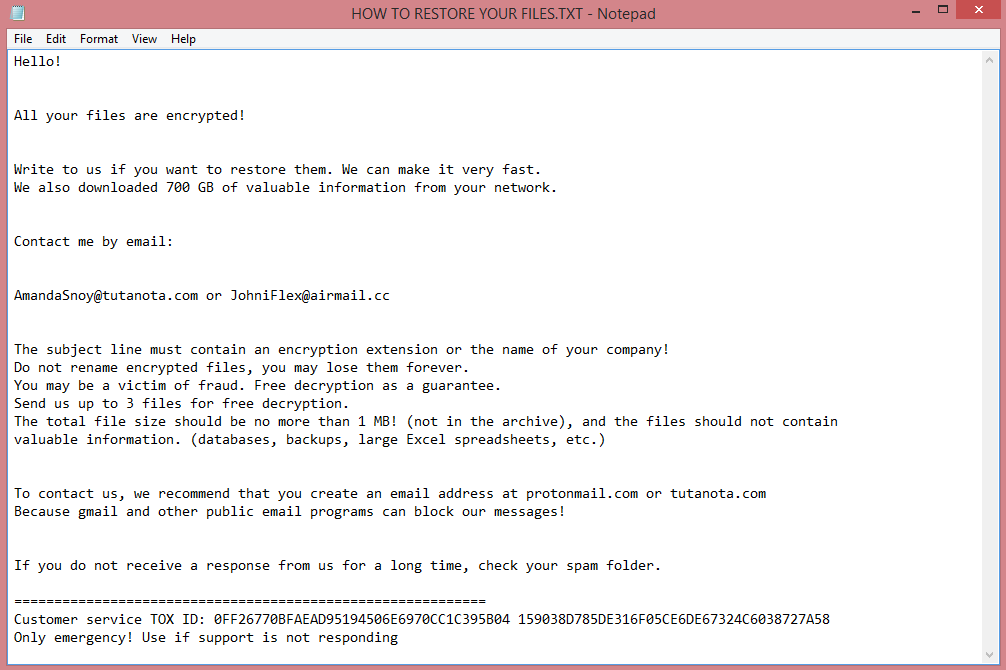
When Yguekcbe encrypts files, it also changes their names, adding .yguekcbe file extension. In fact, this is how the virus got its name. It also leaves a ransom note, “HOW TO RESTORE YOUR FILES.TXT”, on the Desktop. The image above contains the full text of the note, but we will also summarize it in the next paragraph.
The note indicates that Yguekcbe virus is designed to target companies, though of course, private individuals may also fall victim to it by accident. The hackers do not specify the ransom amount, only their contact information. Presumably this is because they intend to negotiate.
Contacting the hackers is a bad idea; in many cases they just ignore their victims after receiving payment. And if you really are just a citizen whose computer got infected with Yguekcbe by mistake, they likely wouldn’t even talk with you. This is why you should follow our guide, which will describe how to remove Yguekcbe ransomware and decrypt .yguekcbe files without their involvement.
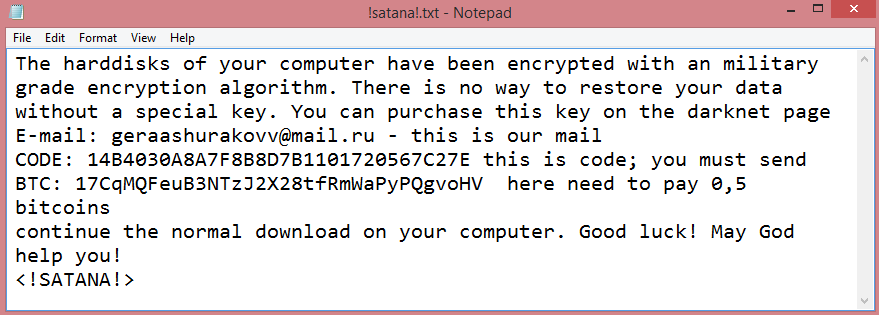
![Anthraxbulletproof ransom note:
Your computer was infected with a ransomware virus. Your files have been encrypted and you won't
be able to decrypt them without our help.What can I do to get my files back?You can buy our special
decryption software, this software will allow you to recover all of your data and remove the
ransomware from your computer.
How do I pay, where do I get Bitcoin?
Purchasing Bitcoin varies from country to country, you are best advised to do a quick google search
yourself to find out how to buy Bitcoin.
Payment informationAmount: 10 000 American Dolar ( Convert it in Bitcoin )
Bitcoin Address: [REDACTED]
After Sending Bitcoin Send us a message on telegram : @anthraxlinkers
This is the end of the note. Below you will find a guide explaining how to remove Anthraxbulletproof ransomware.](https://www.computips.org/wp-content/uploads/2022/11/how-to-remove-anthraxbulletproof-ransomware.png)