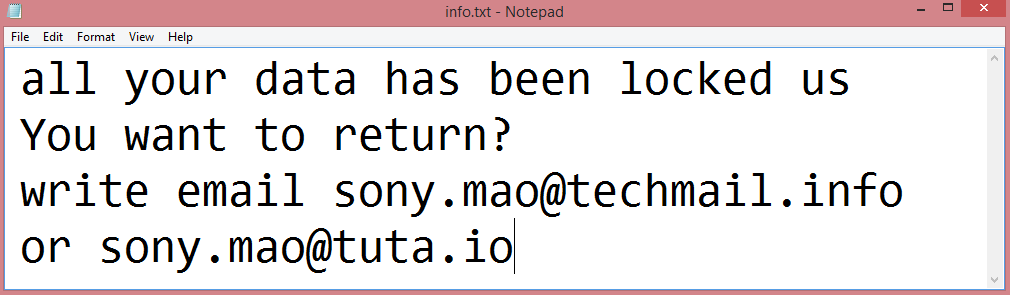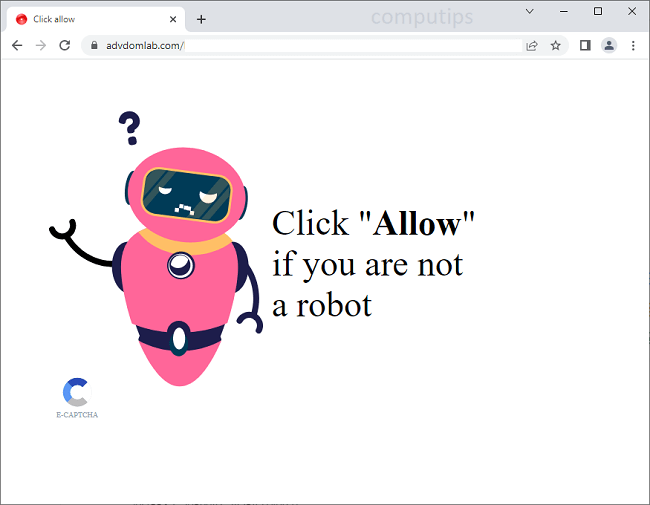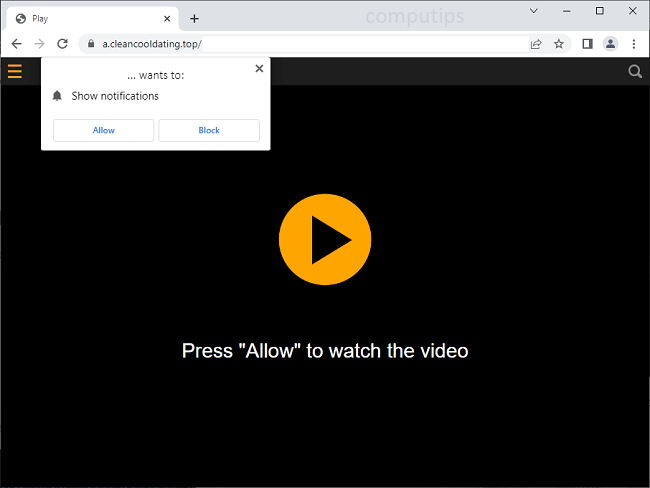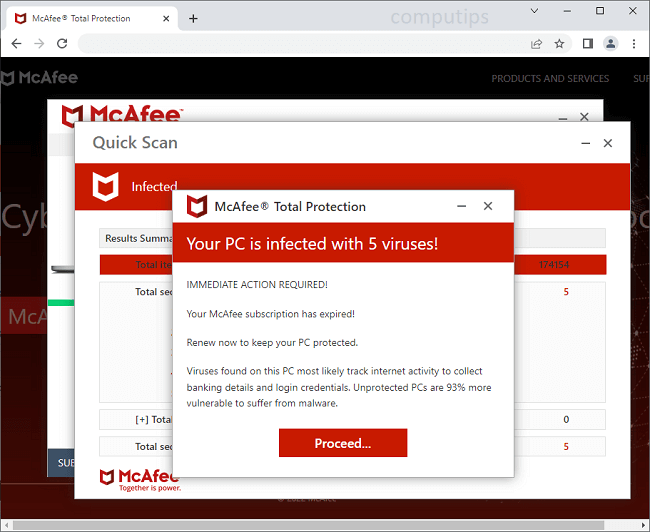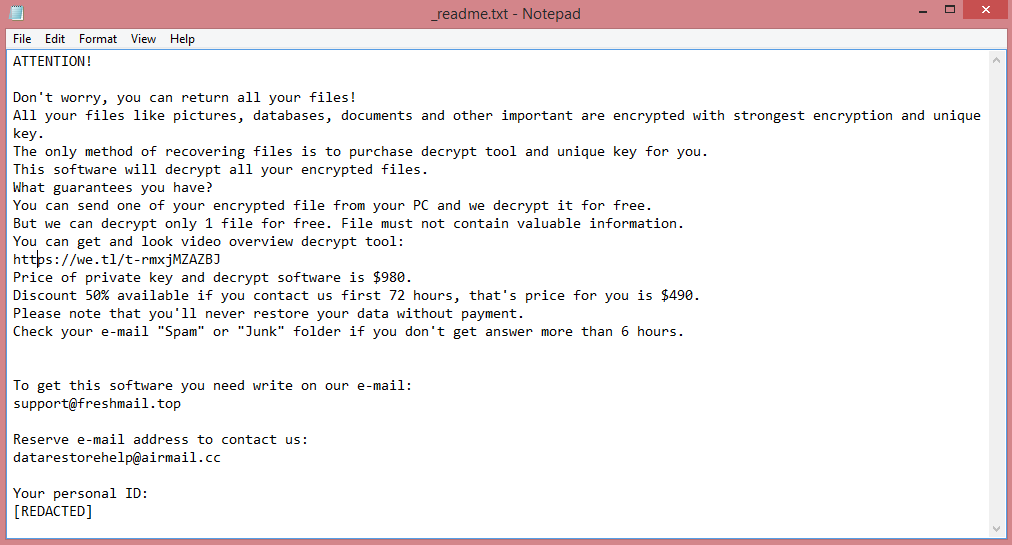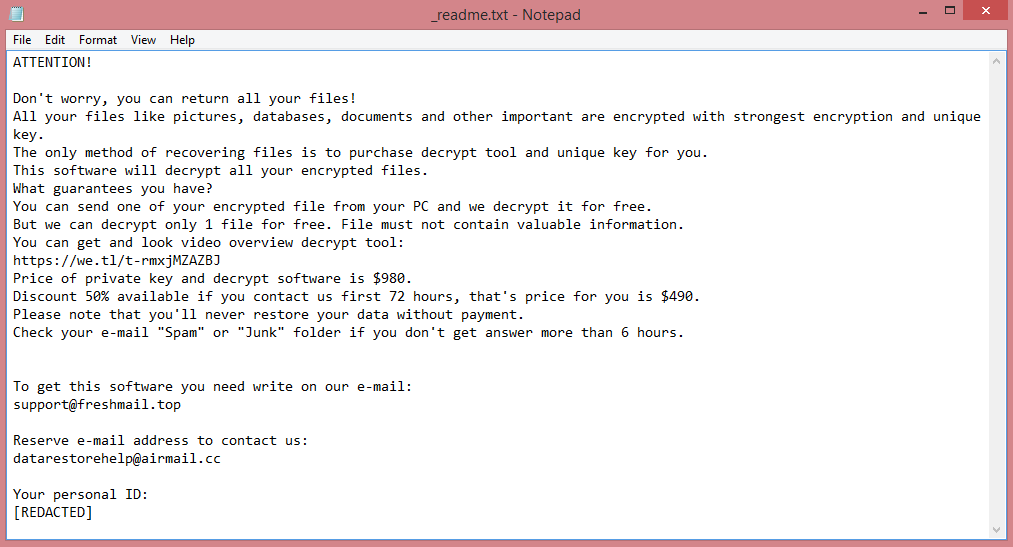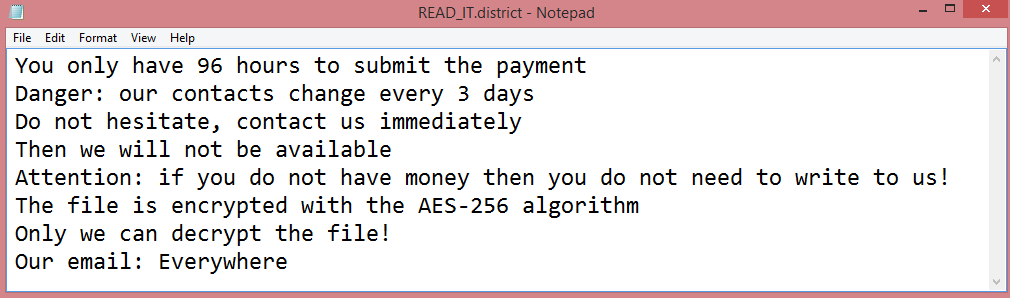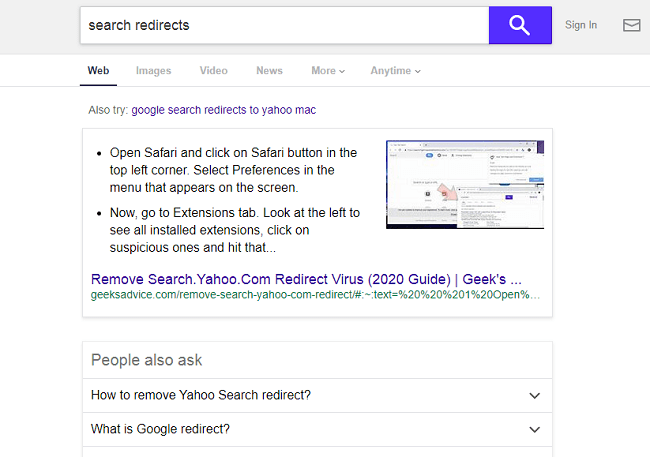
What Is Major Letter Search?
Major Letter Search is a browser hijacker that may appear on your Mac one day and resist your attempts to remove it. A browser hijacker is a piece of software that may alter Homepage, New Tab Page or Search Engine on browsers and stop users from changing those settings again. Most of the time hijackers get downloaded together with free or cracked applications or with files from untrustworthy sources. Major Letter Search, once installed, sets the default search engine on Google Chrome browser to a fake search engine which redirects all users’ searches to Yahoo. This step-by-step guide will help you remove Major Letter Search from your Macbook and get rid of the Yahoo Search redirect.