What is Dgnlwjw ransomware?
Dgnlwjw is a malicious program that encrypts the files on the victim’s computer. The hackers then offer “decryption services”, hoping that the victim had some sensitive or valuable data they’d want back. As the hackers are basically holding the files ransom, this category of programs is known as ransomware.
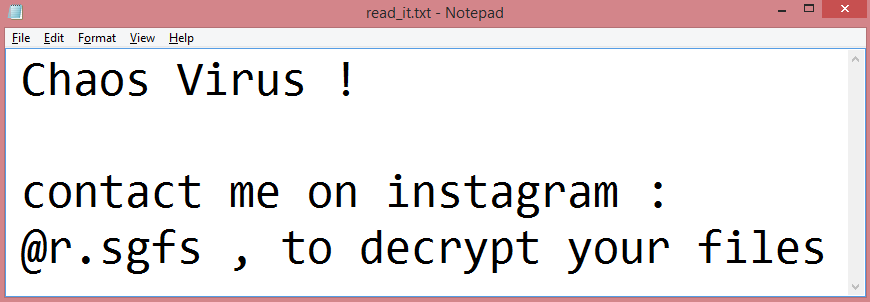
Dgnlwjw belongs to the Snatch ransomware family. It changes the encrypted files’ names, giving them .dgnlwjw file extension. This is not a coincidence; the virus was named after its extension, as it is often the only unique thing about them.
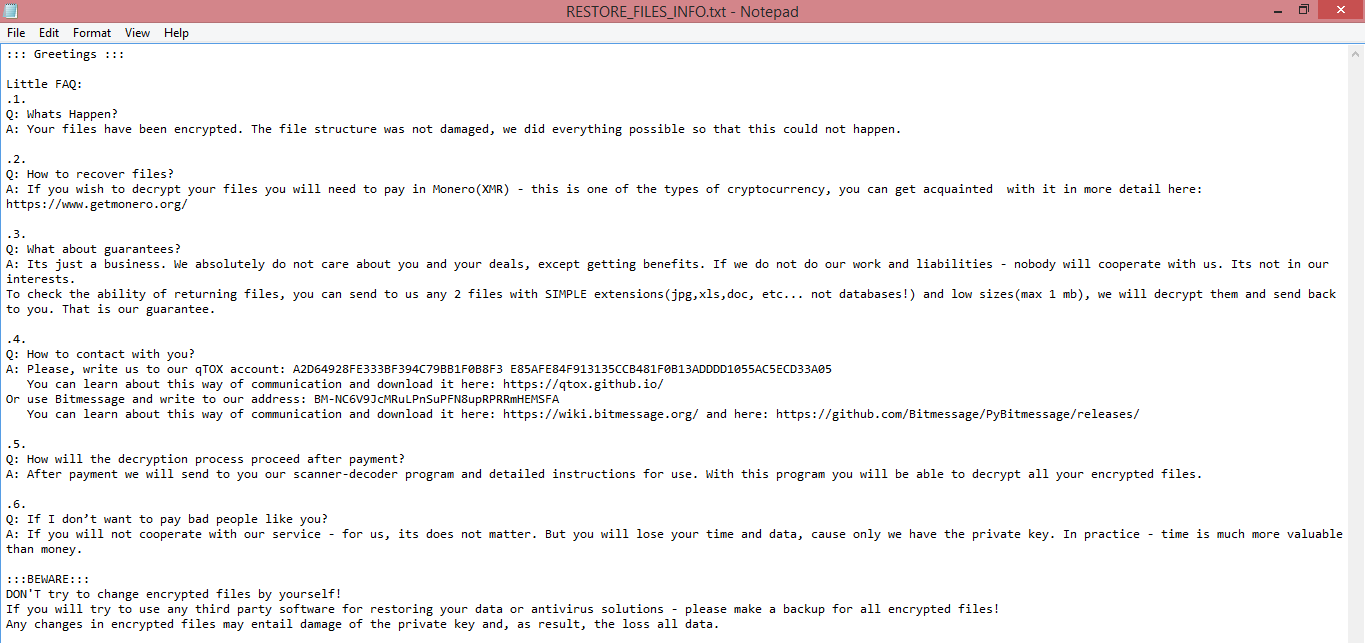
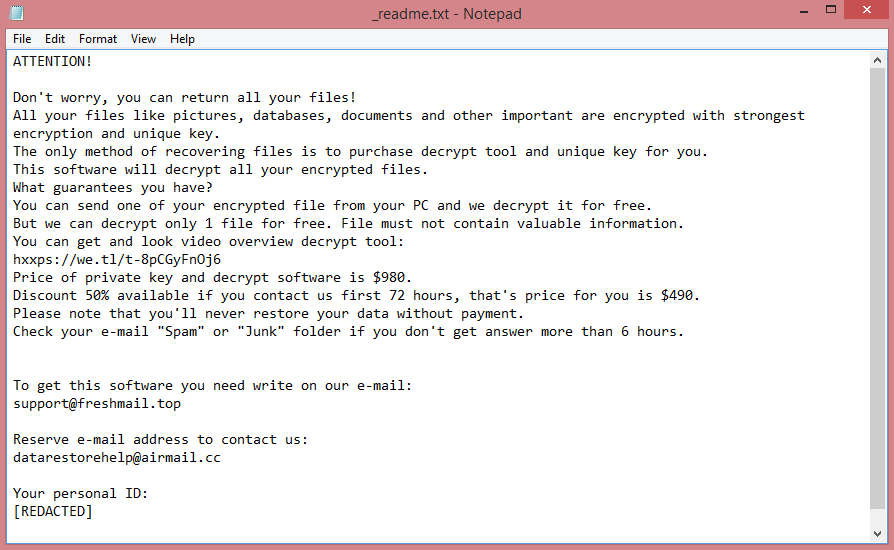
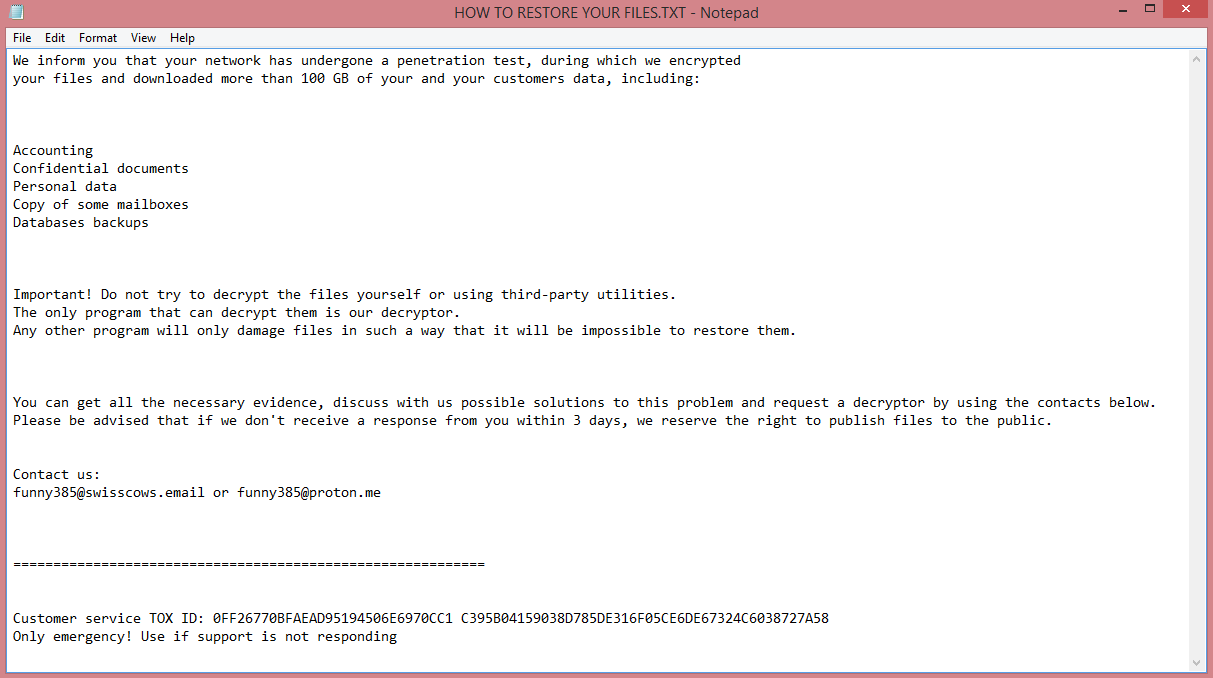
To demand ransom from their victims, the virus creates a text file named “HOW TO RESTORE YOUR FILES.TXT”. You can read the ransom note on the image above. Unfortunately, it doesn’t contain much information. The hackers do not mention how much they want for decryption. However, the note suggests that Dgnlwjw was made to target companies, so the ransom amount is likely quite substantial.
So what should you do if you’re a normal person whose computer has been infected with Dgnlwjw? Not give up, that’s for sure. Our guide contains several methods that will allow you to remove Dgnlwjw ransomware and decrypt .dgnlwjw files without involving the hackers.