What is Epsilon Red ransomware
Epsilon Red is a ransomware that encrypts files found on the device using the AES+RSA infection algorithm. This virus encrypts all files found inside folders, including other executable files and DLLs, which can render programs or even the entire system unusable. Locked files have the extension .epsilonred . After the end of the encryption process, virus creates a file ransom_note.txt , which contains a note:
[+] What’s Happened? [+]
Your files have been encrypted and currently unavailable. You can check it. All files in your system have “EpsilonRed” extension. By the way, everything is possible to recover (restore) but you should follow our instructions. Otherwise you can NEVER return your data.
[+] What are our guarantees? [+]
It’s just a business and we care only about getting benefits. If we don’t meet our obligations, nobody will deal with us. It doesn’t hold our interest. So you can check the ability to restore your files. For this purpose you should come to talk to us we can decrypt one of your files for free. That is our guarantee.
It doesn’t metter for us whether you cooperate with us or not. But if you don’t, you’ll lose your time and data cause only we have the private key to decrypt your files, time is much more valuable than money.
[+] Data Leak [+]
We uploaded your data and if you dont contact with us then we will publish your data.
Example of data:
– Accounting data
– Executive data
– Sales data
– Customer support data
– Marketing data
– And more other …
[+] How to Contact? [+]
You have two options :
1. Chat with me :
-Visit our website: http://epsilons.red/***
-When you visit our website, put the following KEY into the input form.
-Then start talk to me.
2. Email me at : ***@protonmail.com
There are also other files related to Epsilon Red virus:
rutserv.exe is an installer file created with Remote Utilities that the attackers download to multiple computers on the target’s network to run later on.
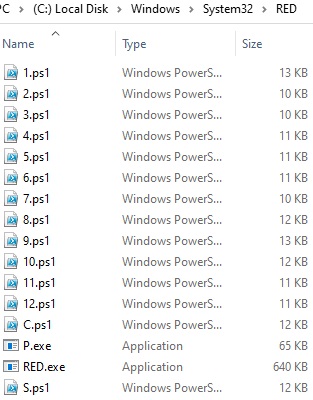
1.ps1 looks for processes containing any of the following strings in the name and tries to terminate them: sql, Sql, SQL, BASup, Titan, SBAM, sbam, vipre, Vipre, Cylance, cylance, Senti, senti, sql, backup, veeam , outlook, word, excel, office, ocomm, dbsnmp, onenote, firefox, xfssvccon, infopath, wordpa, isqlplussvc, sql, dbeng50, mspub, mydesktopqos, ocautoupds, thunderbird, encsvc, oracle, mydesktop, agntsvcd, thebcc , tbirdconfig, synctime, visio, sqbcoreservice, winword, msaccess, powerpnt, mepocs, memtas, svc $, vss, sophos, crm, quickbooks, pos, qb, sage, SQL, prc, w3wp, java, store, ax32, dbs, wordpad, VeeamAgent, Backup, Cloud, Mbae, MB3, WRSA, rsa, wrsa.
2.ps1 removes all system shadow copy volumes.
3.ps1 disables automatic repair that Windows may try to start after restarting.
4.ps1 tries to delete shadow copies in a different way:
wmic shadowcopy delete / nointeractive
Get-WmiObject Win32_ShadowCopy | % {$ _. Delete ()}
Get-WmiObject Win32_ShadowCopy | Remove-WmiObject
Get-WmiObject Win32_Shadowcopy | ForEach-Object {$ _Delete (); }
Get-CimInstance Win32_ShadowCopy | Remove-CimInstance
5.ps1 executes two commands that delete the Windows Event Logs), which makes it difficult to investigate incidents;
6.ps1 tries to terminate services based on the following list of strings that may appear in the names of these services:
sql, Sql, SQL, BASup, Titan, Cylance, cylance, Defend, NisSvc, Veeam, veeam, backup, Backup, rsa, wrsa, WRSA, RSA
7.ps1 disconnects almost all open sessions on the computer;
8.ps1 duplicates the script for the firewall rules included in red.ps1;
9.ps1 launches first and tries to invoke an uninstaller for security software from Sophos, Trend Micro, Cylance, MalwareBytes, Sentinel One, Vipre, Webroot and multiple cloud backup agents;
10.ps1 reruns the remote P.exe executable, which suspends processes containing the following lines and clears their logs:
MpCmd, MsMp, Senti, senti, sql, backup, veeam, outlook, word, excel, office, ocomm, dbsnmp, onenote, firefox, xfssvccon, infopath, wordpa, isqlplussvc, sql, dbeng50, mspub, mydesktopqos, ocautoupird encsvc, oracle, mydesktopservice, thebat, agntsvc, steam, ocssd, tbirdconfig, synctime, visio, sqbcoreservice, winword, msaccess, powerpnt, mepocs, memtas, svc $, vss, sophos, crm, quickbooks, pos, qb, sage, SQL , prc, w3wp, java, store, ax32, dbs, wordpad, VeeamAgent, Backup, Cloud, Mbae, MB3
11.ps1 runs the following commands to delete shadow copies (third time!), Change recovery options, and flush logs:
vssadmin.exe Delete Shadows / All / Quiet
bcdedit / set {default} recoveryenabled no
wmic shadowcopy delete
wbadmin delete backup
wbadmin delete systemstatebackup -keepversions: 0
bcdedit / set {default} bootstatuspolicy ignoreallfailures
bcdedit / set {default} recoveryenabled no
wevtutil.exe clear-log Application
wevtutil.exe clear-log Security
wevtutil.exe clear-log System
wbadmin delete systemstatebackup
wbadmin delete catalog -quiet
bootstatuspolicy ignoreallfailures
12.ps1 grants the group all permissions on every drive letter the computer can have to encrypt as many files as possible.
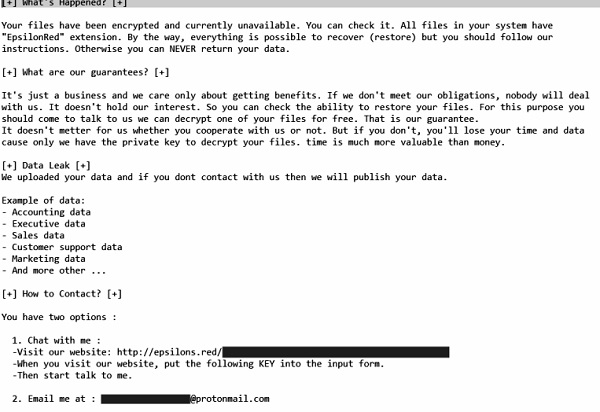
This is a note from the developers of Epsilon Red ransomware. They are trying to lure the victims of money in the amount of several hundred, promising to return the files, but this is only a trick and deception. Files cannot be decrypted while there is a virus in your device, so you need to get rid of Epsilon Red ransomware.
There are 2 options for solving this problem. The first is to use an automatic removal utility that will remove the threat and all instances related to it. Moreover, it will save you time. Or you can use the Manual Removal Guide, but you should know that it might be very difficult to remove Epsilon Red ransomware manually without a specialist’s help.
If for any reason you need to recover deleted or lost files, then check out our article Top 5 Deleted File Recovery Software
Epsilon Red Removal Guide

Remember that you need to remove Epsilon Red Ransomware first and foremost to prevent further encryption of your files before the state of your data becomes totally useless. And only after that, you can start recovering your files. Removal must be performed according to the following steps:
- Download Epsilon Red Removal Tool.
- Remove Epsilon Red from Windows (7, 8, 8.1, Vista, XP, 10) or Mac OS (Run system in Safe Mode).
- Restore Epsilon Red files
- How to protect PC from future infections.
How to remove Epsilon Red ransomware automatically:
[Best_Wordpress_Gallery id=”48″ gal_title=”Malwarebytes”]
Malwarebytes antivirus may help you to get rid of this virus and clean up your system. In case you need a proper and reliable antivirus, we recommend you to try it.
If you’re Mac user – use this.
Manual Epsilon Red Removal Guide
Here are step-by-step instructions to remove Epsilon Red from Windows and Mac computers. Follow these steps carefully and remove files and folders belonging to Epsilon Red . First of all, you need to run the system in a Safe Mode. Then find and remove needed files and folders.
Uninstall Epsilon Red from Windows or Mac
Here you may find the list of confirmed related to the ransomware files and registry keys. You should delete them in order to remove virus, however it would be easier to do it with our automatic removal tool. The list:
Epsilon Red .dll
_readme.txt
readme.txt
Windows 7/Vista:
- Restart the computer;
- Press Settings button;
- Choose Safe Mode;
- Find programs or files potentially related to Epsilon Red by using Removal Tool;
- Delete found files;
Windows 8/8.1:
- Restart the computer;
- Press Settings button;
- Choose Safe Mode;
- Find programs or files potentially related to Epsilon Red by using Removal Tool;
- Delete found files;
Windows 10:
- Restart the computer;
- Press Settings button;
- Choose Safe Mode;
- Find programs or files potentially related to Epsilon Red by using Removal Tool;
- Delete found files;
Windows XP:
- Restart the computer;
- Press Settings button;
- Choose Safe Mode;
- Find programs or files potentially related to Epsilon Red by using Removal Tool;
- Delete found files;
Mac OS:
- Restart the computer;
- Press and Hold Shift button, before system will be loaded;
- Release Shift button, when Apple logo appears;
- Find programs or files potentially related to Epsilon Red by using Removal Tool;
- Delete found files;
How to restore encrypted files
You can try to restore your files with special tools. You may find more detailed info on data recovery software in this article – recovery software. These programs may help you to restore files that were infected and encrypted by ransomware.
Restore data with Stellar Data Recovery
Stellar Data Recovery is able to find and restore different types of encrypted files, including removed emails.
[Best_Wordpress_Gallery id=”45″ gal_title=”Stellar Data Recovery”]
- Download and install Stellar Data Recovery
- Choose drives and folders with your data, then press Scan.
- Select all the files in a folder, then click on Restore button.
- Manage export location. That’s it!
Aiseesoft Data Recovery
[Best_Wordpress_Gallery id=”61″ gal_title=”aiseesoft”]
Aiseesoft Data Recovery recovers deleted files (like photos, documents, emails, audio, video), and also recovers from a computer, hard drive, flash drive, memory card, digital cameras. Recover from accidental deletion, formatted partition, hard drive problem, RAW hard drive, computer crash
We hope this guide was helpful to you. Feel free to leave a comment and tell us what recovery software was (or wasn’t) effective in your case.
How to prevent ransomware infection?
It is always rewarding to prevent ransomware infection because of the consequences it may bring. There are a lot of difficulties in resolving issues with encoders viruses, that’s why it is very vital to keep a proper and reliable anti-ransomware software on your computer. In case you don’t have any, here you may find some of the best offers in order to protect your PC from disastrous viruses.
Malwarebytes
[Best_Wordpress_Gallery id=”48″ gal_title=”Malwarebytes”]
Malwarebytes is a reliable antivirus application, that is able to protect your PC and prevent the infection from the start. The program is designed to be user-friendly and multi-functional.